With all of the various web applications we use nowadays, it can be daunting to remember all of those passwords. Many people turn to password management software to help with this. Rather than remembering 20 passwords, you can store them all in a (presumably) secure database that’s protected by a single strong password. It’s a good idea in theory, but only if the software is actually secure. [Matteo] was recently poking around an Android password management software and made some disturbing discoveries.
The app claimed to be using DES encryption, but [Matteo] wanted to put this claim to the test. He first decompiled the app to get a look at the code. The developer used some kind of code obfuscation software but it really didn’t help very much. [Matteo] first located the password decryption routine.
He first noticed that the software was using DES in ECB mode, which has known issues and really shouldn’t be used for this type of thing. Second, the software simply uses an eight digit PIN as the encryption key. This only gives up to 100 million possible combinations. It may sound like a lot, but to a computer that’s nothing. The third problem was that if the PIN is less than eight characters, the same digits are always padded to the end to fill in the blanks. Since most people tend to use four digit pins, this can possibly lower the total number of combinations to just ten thousand.
As if that wasn’t bad enough, it actually gets worse. [Matteo] found a function that actually stores the PIN in a plain text file upon generation. When it comes time to decrypt a password, the application will check the PIN you enter with the one stored in the plain-text file. So really, you don’t have to crack the encryption at all. You can simply open the file and reveal the PIN.
[Matteo] doesn’t name the specific app he was testing, but he did say in the Reddit thread that the developer was supposedly pushing out a patch to fix these issues. Regardless, it goes to show that before choosing a password manager you should really do some research and make sure the developer can be trusted, lest your secrets fall into the wrongs hands.
[via Reddit]

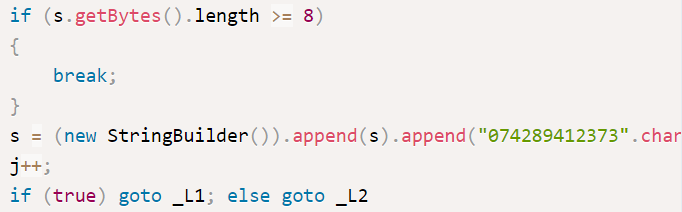














“… a function that actually stores the PIN in a plain text file upon generation.”
Great. The software writes your PIN on a Post-It Note.
Hey, it’s the same acronym. How are we to know the difference?
I… never noticed that 8|
It’s no coincidence that Post-It-Note and Personal-Identification-Number share the same acronym.
well sticking to memorizing.
If the combination is only up to 100 million, the burden on the criminal would be no different if the PINs are hashed for storage. 100 million combinations can be cracked in a blinked with a simple rainbow table.
ID federations (single-sign-on services and password managers) create a single point of failure, not unlike putting all the eggs in a basket. It remembers all my passwords when un-hacked and loses all my passwords to criminals when hacked. It should be operated in a decentralized formation or should be considered mainly for low-security accounts, not for high-security business which should desirably be protected by all different strong passwords unique to each account. Needless to say, the strength of the master-password is crucially important.
That’s only an issue if there’s a hash to check against. If the PIN is used in a pbkdf2 derived key which is used to decrypt the database then 100’000’000 is plenty. Rainbow tables won’t work.
Assume Mr A uses a 13-bit-strong 4-digit PIN and Mr B uses a 53-bit-strong alphanumeric password. The protection for Mr A is a trillion times weaker than for Mr B.
Whatever calculation we may use, a shorter PIN is weaker than a longer alphanumeric password on top of the cognitive fact (*) that PIN is harder to manage.
* Many people take it for granted that PIN is easier to remember than an alphanumeric password because it is simpler. The fact is, however, that PIN, a numbers-only short password, is even more subject to the interference of memory exactly because it is simpler, say, it contains less information, which gets the user confused more easily and more badly than a longer alphanumeric password. It is, therefore, more difficult for us to eliminate the reuse across many accounts. You could listen to yourself for your own experience.
well at least this password manager don’t phone home…
I wonder if saving the PIN in plaintext is actually a flaw, or a feature deliberately included as recourse for those who have forgotten their PIN. It’s funny how the some folks demand no less than triple quantum 4096-qubit cryptography, yet when they lose their key, assume the developer can help them remotely retrieve their data. And when you tell them you can’t, try begging/sobbing/throwing a tantrum to see if it changes your answer. Still, saving the PIN in plaintext isn’t the greatest idea.
> feature deliberately included as recourse for those who have forgotten their PIN
Yup, the person who has access to your phone also “forgot” YOUR pin, but hey no worries, it is stored in a text file so that he can just look it up for himself than to ask you. Right?
It is a pity that the password manager isn’t named. Like this the article doesn’t really help the people who might be using it to store their sensitive data at all – not everyone has the means and knowledge to perform a similar analysis and has to rely on reviews made by others.
My thought too.
recommendations on safe password managers ?
Print out a fake library card. On the back, like the terms and conditions you can hide whatever you want. Criminals don’t read and at least this way they can’t check dvds out on your card. Basically, in your home in a random book or on your person are the safest places. The folks on here are a mixture of crazy/stupid so they like to create their own problems to fix. I guess you could try HaD’s on mutlipass gadget (if it ever got produced lol).
How about KeePass? Free and Open Source. There are many implementations for desktop and mobile.
As far as I’ve heard, the encryption on your brain’s internal storage hasn’t been broken yet. ;)
Torture doesn’t work, so they say?
It sounds very similar to an issue I spotted with the keepsafe app designed to hide files and folders etc.
The app does a reasonably good job of encrypting files, until you realise that the key is hard coded.
The app checks the pin you use against a stored pin and then uses the hardcoded key to unlock the files.
Removing and reinstalling the app or moving the .keepsafe folder to another device and setting up a new pin (e.g. 1111) will let you into the other persons ‘encrypted’ files.
The question here is How else do you want to lock the password manager (or any other app)? Using a PIN or the graphical line-dot-thingy is pretty useless when considering its safety.. so how then? When forcing a user to enter yet another reasonably-long alpha-numeric password is a hassle..
Oh yes, the line-dotty thing is awful! If you leave a smear then a ‘hacker’ only has 2 possible solutions – forwards or backwards. At least if you leave smudges from a 4 digit pin there are 24 ways to try.
Unfortunately, ANY system will have flaws. Biometric? Worst case cut off the finger or decapitate you to get access. Long password? Brute force has long been the solution, with multiple round hash/encryption only slowing the process down. The password is only as secure as the net number of bits used in the hash/encryption key, and often much less secure. PIN, such as for a bank card or online bank account? Only security is the time it takes to try them, and any timeout or penalty for wrong guesses, unless the server is compromised, in which no security at all. If I can hold the device in my hand and don’t mind breaking it, there is no security at all.
Am I a pessimist? Only sort of. Like good physical security, it keeps honest people honest, and hopefully slows the rest down to where they either get caught or give up. Personally, I use the note is a random book method for some (close to 10000 volumes in the house… good luck finding it), memorization for others. Those I write down are low use, and aside from the physical hiding, they are also incomplete or encoded, so finding the book still leaves way too many options to brute force.
I don’t even bother locking cellphone. I just make sure that there is nothing of concern on it. I put little trust in anything that is so easy to break or lose.