We’re going to warn you right up front that this is not a hack. Or at least that’s how it turned out after [LiveOverflow] did some digital forensics on a mysterious device found lurking in a college library. The path he took to come to the conclusion that nothing untoward was going on was interesting and informative, though, as is the ultimate purpose of the unknown artifacts.
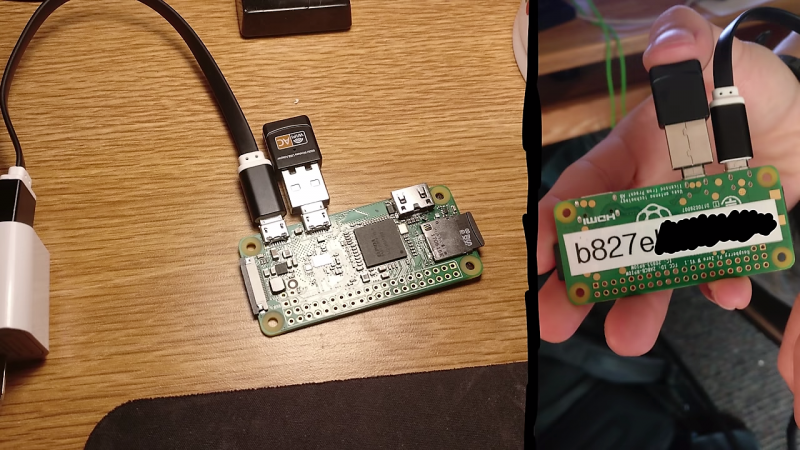
As [LiveOverflow] tells us in the video below, he came upon a Reddit thread – of which we can now find no trace – describing a bunch of odd-looking devices stashed behind garbage cans, vending machines, and desks in a college library. [LiveOverflow] recognized the posted pictures as Raspberry Pi Zeroes with USB WiFi dongles attached; curiosity piqued, he reached out to the OP and offered to help solve the mystery.
The video below tells the tale of the forensic fun that ensued, including some questionable practices like sticking the device’s SD card into the finder’s PC. What looked very “hackerish” to the finder turned out to be quite innocuous after [LiveOverflow] went down a remote-diagnosis rabbit hole to discern the purpose of these devices. We won’t spoil the reveal, but suffice it to say they’re part of a pretty clever system with an entirely non-nefarious purpose.
We thought this was a fun infosec romp, and instructive on a couple of levels, not least of which is keeping in mind how “civilians” might see gear like this in the wild. Hardware and software that we deal with every day might look threatening to the general public. Maybe the university should spring for some labels describing the gear next time.















For those of us without 20 minutes to watch a YouTube video, what are they for?
Congestion monitors that sniffed mobile device IDs to let university students plan around peak use.
Sounds like something better done by checking how many devices are connected to the APs?
Or an IR counter on the entrance and exit of the library that is reset to zero every night.
That would require people to actually connect to the APs. Passively tracking device ids is something routinely done around shopping centres, leisure complexes, etc.
Exactly. I’m at work. I can’t watch a YouTube video. Just tell me.
It tracks people by cataloging what mac addresses are seen when and where, tells you when the library or cafeteria is full. Skip to the end where they tell you how after all the “research” they just googled the name they found in the program + the school and got directed to a website that explained everything, then they checked the original reddit page where the owner had explained what it did and asked them to return it to the library. They got caught up in solving the mystery and didn’t see the obvious answer.
Is it only me who turns Wifi off on my phone when I’m not using it? For one thing it rinses the battery.
I’m afraid it’s only you.
I usually only turn wifi off if it’s giving me an access point with a dodgy connection, but even my phone is clever enough to work that out and switch to the cellular network these days. I mostly leave wifi and bluetooth on all the time now.
My S9+ does that by itself. It learns what WiFi networks you use and when there isn’t one in range it shuts the WiFi off.
I use an open source Android app called Wi-Fi Privacy Police to prevent tracking of my phone by stopping it from continuously screaming into the void for a connection. It does mean it takes slightly longer to connect once it enters the range of a friendly AP though, since it waits until it receives a beacon.
https://www.ucsdwaitz.com/ is the service it is from.
Even if you label things people will freak out. Remember when [Adult Swim] marketeers inadvertently shut down Boston with some LED boards people thought were bombs despite being in the outline of cartoon characters.
well, to be fair, a “b-word” could be almost any shape and size.
They’d run the same viral campaign in other cities without incident. The boards were literally LEDs poked through some black board with a few batteries on them.
As we learned in those stimulating days after 9/11, “If it’s not an American flag, it’s probably a bomb.”
Hmmm. American flag bombs… SHIT! Did I say that out loud?
Stay right there….
America doesn’t (officially) put flags on it’s bombs. We don’t want anyone knowing where they come from.
Sgt Sandbox
Yeah, that’s why they only have the manufacturers name and part serial number on them.
One of the first synthetic fibers were made from nitrated cellulose…. Also dubbed as “Schwiegermutterseide” (“mother-in-law silk”) as the stuf was really flammable.
There’s nothing you can do to avoid the stupidity of the Boston PD. After the LED sign debacle they then went on to blow up a legitimate traffic monitoring device installed by the local transit authority.
When your only tool is a hammer so many problems begin to look like nails…..
Been more than 25 years since I lived there, and they still use the same hammer, but now it is painter homeland security yellow.
Yeah, same thing happened around here, local country cops shutdown a main route and closed a bridge over a river when a kayaker found a “device” attached to the bridge.
Cops called the phone number on the “bomb” and NOAA told them it was one of their river level observation stations…
Was it painted black ?
Free pi0? where can I get one!
Get a job, work for an hour or so and then buy one. They cost next to nothing.
“Security Professional” trying to use Imgburn to image SD card… The entire video feels like two teens trying to act that they know more than they actually do.
In his defence he seemed to have been remotely guiding someone who couldn’t into linux. That’s still not an excuse to waste 10 minutes of video on mounting a raspi filesystem
Presumably as a security professional he usually uses the right tool for the job, the person he was guiding didn’t have the right tool, so he was trying to find a cheap (free) alternative.
That moment
https://www.youtube.com/watch?v=sqgW-2orQQg
:o)
Exactly. A Linux “try before you install” thumb drive would have gotten him to the same point without a bunch of heartache.
“Security Professional” has automount enabled…
Now we wait few days until someone makes MAC flooder with ESP8266 that makes these devices think it’s Woodstock in library.
I am up for it. But our library is always empty,so ….
LOL, time to screw with the department stores and malls that use this for data analytics, Have a bunch of “people” go and stand in front of those annoying music players by the scented candles for an hour then just disappear.
If they’re tracking probe requests rather than MAC:
https://hackaday.com/2017/04/29/linger-keeps-you-around-after-youve-gone/
Why did they not ask their IT Dept what it was? Could’ve saved so much time… Couldn’t the guy just have copied the files to a folder and shared it to himself ? Whole thing seems sketchy to me.
Its a throwie.
It lets u connect to (in this case) the library AP without exposing the ip of the user on the other side. A sort of proxy if you will.
And there are so many people using them that the library is littered with them? Unlikely. The first reply to the first comment reveals its purpose: it’s for tracking busy times at the library based on wifi devices.
Did anyone else who watched the video get the feeling that this guy went to the Billy Mays advertising college and this was his clickbait class homework?
Warning – am a cranky old geezer of the generation that killed Amerikkkka.
The interwebs is freakin amazing. Instant information. Always on. It has given young folk the illusion of knowledge and competency. About three years past, the neighbor’s kid (high school athlete that had been told he is special and so very smart) ‘found’ some plastic boxes mounted on my perimeter fence. He proceeded to remove and dismantle one of my widgets. Long story short – he went to jail for criminal trespass, property damage, and theft. His defense was that he was investigating illegal surveillance equipment.
At least I am smart enough to know that I am stupid. Now get off of my dirt…
You got a kid sent to jail for being curious? Did he smash the boxes into pieces? Did he just open them and poke around? Yeah, kids poke the wrong things sometimes and end up in handcuffs because someone with zero understanding of the ideals behind the “hacker manifesto” thinks its dangerous to have curious minds. Kids also smash people’s property because they think it’s fun or makes them look cool. Which was it? If I caught a kid checking out something I built, I’d try to foster a mentorship with them rather than calling the police.
Yes, it is quite obvious that I am wrong and a very bad person. Should have been happy that the kid cut into my fence line to get onto my property and should have been supportive of his efforts that cut the battery cables to my box and ecstatic that the kid broke off the charger cable to my box. Then I should have granted him further dispensations when he sawed open my $50 NEMA box and, finally, was very much in the wrong in that I did not provide a social support structure when he broke the two internal PCBs ($125 and 30 hours of my time).
see brian? you’re not as dumb as you thought!
Yikes, I thought you were going to say that he just opened the box. That’s just plain old destruction of property.
Interestingly the same hardware could be deployed in a univerity library, connect to the local public internet, use that to connect to a VPN server out on the net somewhere and route traffic from that server out the local internet connection. A crafty network “craftsman” could use such a setup to access univerity-subscribed science journals from home. How many readers here have wanted to read a scientific journal artical but can only access the abstract but a university is too far away or hard to get to? I know it’s at least one. The whole restriction disgusts me since lots of public money went into doing most of the research. The public should be able to easily access the results.
Clockboy II