We’ve all stared at that button in the elevator with the phone icon on it, supremely confident that if the cab came to a screeching halt while rocketing up to the 42nd floor, a simple button press would be your salvation. To be fair, that’s probably true. But the entire system is not nearly as robust as most people think.
Friday at DEF CON 27, [Will Caruana] took the stage to talk about phone phreaking on an elevator. The call buttons first appeared on elevators in 1968 as actual phone handsets, eventually becoming a mandated feature starting in 1976. Unfortunately, the technology they use hasn’t come all that far since. Phone modules on elevators did benefit when DTMF (touch tones) and voice menu systems rolled around. But for the most part, they are a plain old telephone service (POTS) frontend.
[Will] spends his spare time between floors pressing the call button and asking for the phone number. It’s the lowest bar of social engineering, by identifying yourself as an elevator service technician and asking for the number he is calling from. His experience has been that the person at the other end of the phone will give you that number no questions asked nearly every time. What can you do with a phone number? Turns out quite a bit.
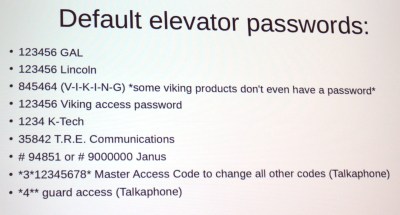 The keys to the castle are literally in the elevator phone user manuals. The devices, shipped by multiple manufacturers, come with a default password and [Will’s] experience has been that nobody changes them. This means that once you have the phone number, you can dial in and use the default password to reprogram how the system works. This will not let you directly control the elevator, but it will let you speak to the people inside, and even change the call-out number so that the next time that little button is pressed it calls you, and not the phone service it’s intended to dial. That is, if the system was even correctly set up in the first place. He mentioned that it’s not too hard to find elevators that don’t have their location set up in the system — if you do need help, it may be hard to figure out which elevator you’re actually in. There have also been instances where these call the 24-hour maintenance staff for the building, a bewildering experience for sleepy personnel who didn’t sign up for this.
The keys to the castle are literally in the elevator phone user manuals. The devices, shipped by multiple manufacturers, come with a default password and [Will’s] experience has been that nobody changes them. This means that once you have the phone number, you can dial in and use the default password to reprogram how the system works. This will not let you directly control the elevator, but it will let you speak to the people inside, and even change the call-out number so that the next time that little button is pressed it calls you, and not the phone service it’s intended to dial. That is, if the system was even correctly set up in the first place. He mentioned that it’s not too hard to find elevators that don’t have their location set up in the system — if you do need help, it may be hard to figure out which elevator you’re actually in. There have also been instances where these call the 24-hour maintenance staff for the building, a bewildering experience for sleepy personnel who didn’t sign up for this.
Want to go beyond the call button and dig deeper into the secrets of pwning elevators? [Will] suggests watching the HOPE X talk from [Deviant Ollam] and [Howard Payne] called Elevator Hacking: From the Pit to the Penthouse.

















As with most pen-tester talks, the real point of discussing these problems is to shed light on them in the hopes that the industry takes notice and starts fixing them.
Agreed. What’s the point of a changeable password if people aren’t going to change it?
Perhaps changing the password causes significant problems in actual use, so maybe shouldn’t have been implemented in the first place.
Maintenance. People forget passwords, do not record them, and that adds another hassle to reset them. The usual mess.
Are they actual real-life problems, though? Just because a security guy jumped through all the hoops to come up with a conference talk doesn’t mean it’s been an actual problem.
Rooting an elevator phone isn’t much of a win, is it.
It is when you can control the elevator with it and cause mayhem.
For example, pull off a “denial of service” attack on your competitor’s headquarters as you’re pulling some sort of shady move on the market. They’ll be spending time and effort getting their people unstuck from the elevators, while you’re trading on the stock market pulling deals in front of their noses.
You’ll notice the article said you can’t directly control the elevator itself….
I’ll assume you only update your computer if it’s patching something that has been exploited in the wild…
[Jon H], I’m very confused at the point you are trying to make.
You first point out, mostly in an incorrect way, but correct in that without fixing these problems someone can get killed.
But then you flip flop and multiple times seem to suggest the problems that can get people killed should not be fixed, and even suggesting they be fixed so people don’t die is a bad thing.
If having a working safety feature like an emergency call button really is as simple as just not allowing the bad guys to disable it or reroute it by typing “12345”, why shouldn’t that be done? I don’t understand why you are so against such a simple fix
as someone who has done elevator phone installs I highly recommend people not tamper with them. all it takes is somebody dying from a heart attack and not be able to reach emergency services for all hell to break loose
” He mentioned that it’s not too hard to find elevators that don’t have their location set up in the system — if you do need help, it may be hard to figure out which elevator you’re actually in. There have also been instances where these call the 24-hour maintenance staff for the building, a bewildering experience for sleepy personnel who didn’t sign up for this.”
Seems to me there’s bigger problems than people playing with the elevator programming.
Except hackers aren’t helping and besides we don’t known if Will Caruana is just making s**t up to justify his screwing with someone else’s private property. Which is a criminal act.
The very fact he is encouraging criminal activity borders on the sociopathic. It’s like finding your neighbor’s home poorly secured and deciding it’s okay to break in and f**k things up to educate the owner.
“where these call the 24-hour maintenance staff for the building, a bewildering experience for sleepy personnel who didn’t sign up for this.”
They did, in fact, sign up for this. They probably even live in the building. They’d probably prefer a 3AM call about a stuck elevator than a call about an overflowing toilet flooding the apartment downstairs. They’d actually have to fix the toilet themselves.
” if you do need help, it may be hard to figure out which elevator you’re actually in”
I can’t imagine it’d be very difficult if the person at least knows the address. Most buildings only have one elevator. Buildings with banks of elevators probably have the elevators set up correctly.
You are completely missing the point. What he is encouraging is buildling owners to demand their elevators are properly configured and maintained.
Often the elevator phone is a POTS line off the building PABX with hotline (autodial) or speedial to the service centre.
If its correctly configured by the PABX installer it should never be able to dial anything else…
But its usually an afterthought to check the lift phone works as the tech is packing up and leaving the building!
They are properly configured and working fine. Until a yahoo like this dork messes with the settings of it. Now he just encouraged a crap ton of other goof balls to try the same thing.
It is like breaking into a bank, and telling the owners they ‘need’ better vault security. I love the thought process here to justify public vandalism. Pathetic article. As if we owe this guy the Nobel prize…
The presenter is a security penetration tester, that is literally his job description and the “bank” pays him a lot of money to do it.
Oh wouldn’t it be interesting to do an article on how DoorKing authenticates the connections on their commercial telephone entry systems (183x).
A huge WTF.
Like:
Software: call 225-235-3423…(ring)…(ring)
Telephone entry:hello, my master code is 1234, can I connect to software?
Software: lemme see….. 1234… yup … connected
Now *that* is something worth investigating.
Reconfigure the elevator phone in your building to call a really expensive toll number.
Press the call button a bunch of times and I guarantee the system will be propperly protected with a password after the next phone bill comes around.
That’s the combination I have on my luggage!
One other report of abusing the elevator call boxes – I’ve heard several reports of robocalls accidentally dialing elevator call boxes and playing their telemarketing spiel.
He definitely needs a life.
I have worked in a number of elevator emergency phones. They are usually programmed to call the superintendent of the building or the elevator company in case of an EMERGENCY. If script kiddies start messing with it because of this d**head hacker wannabe, then it can potentially leave people stranded in elevators for hours and risk their lives. There are numerous times when the elevator phone was not working. when people got stuck on the elevator they ended up calling 911 instead of using the emergency phone. Fire department would show up and destroy the elevator doors just to get the people out. That ended up costing the building thousands of dollars to replace the doors. Guess who ends up paying for those doors? Residents of that building. Their rents go up because of stupid expenses like these.
There’s a real easy way to keep the majority of these “script kiddies” from tampering with something like this. DON’T USE THE DEFAULT PASSWORD. I want to say there was an article about this recently…
Loved this talk, especially since one of the particular manufacturers of elevators, United Technologies Corp. (UTC) which owns OTIS elevators, offered me a spot on their project zero team, and this was definitely one of the attack surfaces of note to pop up in my interview. I sense quite a bit of hostility in this comments section, but all I can say is that Will C. pointed out some opportunities for denial of service and surveillance that needs to be publicized and eventually patched/secured.