Everyone loves a good bubble machine. These oddly satisfying novelty items have brought children and adults mindless entertainment since their inception. [8BitsAndAByte] had the same thought, but wanted to give their bubble machine a taste of the IoT-age.
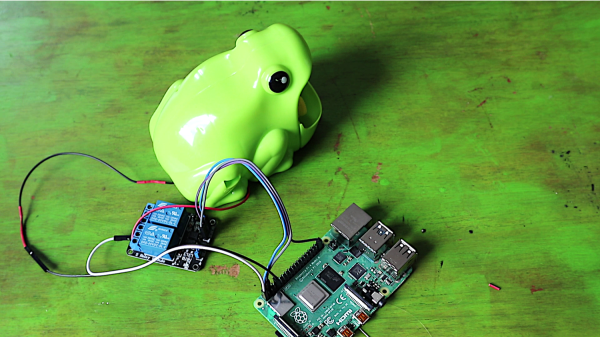
First, they modified an off-the-shelf bubble machine with a Raspberry Pi and relay module. The Pi can easily trigger the bubbling mechanism by controlling power to the machine using the relay. Seems simple enough. The part of this project that might be a bit more unfamiliar to you is controlling the robot over the internet using remo.tv.
Remo.tv is a robot controller platform that’s both free and open-source, and we’ve seen [8BitsAndAByte] take advantage of this web controller before. Seems like they’re really getting the hang of it. Their writeup links to a detailed setup guide for configuring the Pi, so hopefully, that’s not too much trouble.
Couple the IoT setup with a Pi camera and you’ve got a live stream that’s admittedly oddly satisfying to watch with or without the bubbles.