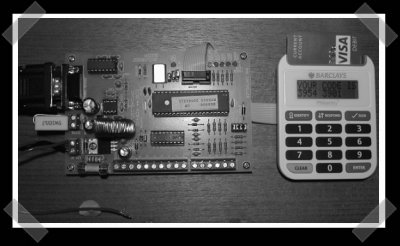
[Mr G] in London sent in his pin sentry hack. He wasn’t pleased that the device looks like an old calculator, so he rigged up a SMS board to send him his pin on demand. He multiplexed the output of the display driver to the SMS board. When he authenticates from his phone, the board sends a message with the latest code.
Cellphone Hacks540 Articles
Cell Phone Taser

I’m not going to reccomend it, but [cameron] modded his Sony Ericsson k800i to tase people as well as take pictures. Apparently, the k800i has a xenon flash – meaning that it’s got a high voltage potential available to drive the flash. He added a pair of 16uf caps and scored a good 300 volts to share with the unlucky.
ToorCon 9: Real World Fuzzing

We dropped in on [Charlie Miller]’s fuzzing seminar at the end of the day yesterday. Fuzzing become a fairly popular topic in the last year and essentially involves giving a program garbage input, hoping that it will break. If it can’t handle the fake data and fails in a non-graceful fashion, you could have found a potentially exploitable bug. Fuzzing is a fairly simple idea, but as Charlie points out, without some thinking while you’re doing it it’s unlikely to be very productive.
Automatic JTAG Pinout Detection
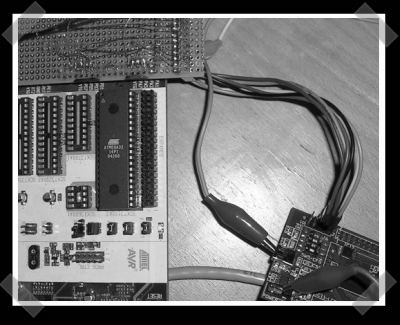
Figuring out the JTAG pinout on a device turns out to be the most time consuming hardware portion of many hacks. [hunz] started a project called JTAG Finder to automatically detect the JTAG pinouts on arbitrary devices using an 8bit AVR ATmega16/32L microcontroller. Check out the slides (PDF) from the talk as they break down how one finds JTAG ports on an arbitrary device, with or without a pinout detection tool. [hunz] is looking for people to pick up the project where he left off.
Once you determine the correct pinout, you will need a JTAG cable: there are two main types, buffered and unbuffered, both of which I have soldered up and tested from these circuit diagrams (image of completed buffered cable here). The software most hardware people use today are the openwince JTAG Tools. To get the JTAG Tools to compile, grab the latest source directly from their CVS repository.
The last time we featured JTAG was with regards to Linksys devices, but the tools listed above can be applied to any device with JTAG.
Simple IPhone Headphone Mod

Apparently the iPhone jack isn’t quite standard – it’s a bit recessed to the point that third parties are offering adapters for it. [John] offers this simple method for modding Etymotic’s fine ER6i headphones. (If only I could find mine. I haven’t seen them for 8 months.) I suggest using a utility knife over a pocket knife. It’s simple, easy, and will probably work on most headphones.
GSM Alarm

Fresh from the tips line, [Pedro] sent in his GSM alarm. He combined a GSM phone, a motion sensor and BasicX24 controller board. If the detector trips during a set time period, the alarm sends SMS messages to the terminator, er whoever you want. He was kind enough to release the code, but I’d like to see this with a smaller micro-controller board to keep the cost/size down.
CCCamp 2007: GSM A5 Cracking
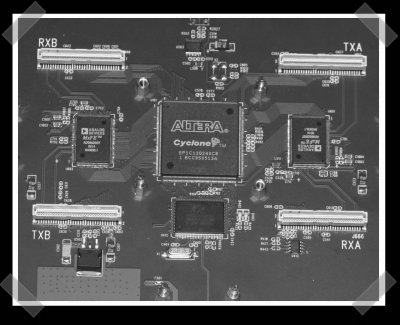
Steve Schear and David Hulton gave a presentation on A5 cracking. A5 is the encryption employed on GSM cellphone networks between the handset and the tower (nowhere else in the network). To sniff the GSM band, they use the GNU radio USRP. GNU radio is a software defined radio project, which given some effort you should be able to both receive and transmit in any RF band. You could use it to broadcast digital television, track radio tags, or even mess with garage door openers. For their initial investigation they used a Nokia 3310 in trace mode to dump the initial frames. Using a box with at least 27 FPGA’s they plan on constructing a 6+ terabyte rainbow table (it’ll take a couple months). Once complete, any GSM conversation can be cracked in less than 5 minutes using a single FPGA. The Hackers Choice has more info on the USRP based GSM analyzer and what they did to crack A5.










