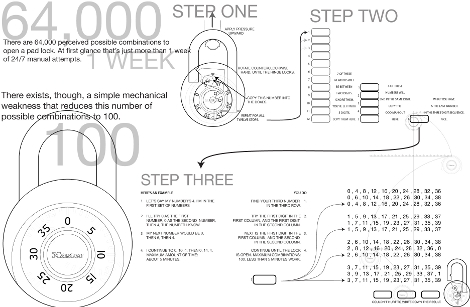
Long, long ago we covered a method to crack a Master lock in about 30 minutes or less. Here’s a revival of the same method but now the instructions to retrieve the combination are in info-graphic format created by [Mark Edward Campos].
If you didn’t get to try this the first time around, here’s how it works: A combination of a physical vulnerability, math, and brute force is used. First, the final number of the code can be obtained by pulling up on the latch while the dial is rotated. Because of the way the lock is built the correct number can be extrapolated using this trick. Secondly, a table of all possible first and second number combinations has been calculated for you. Third, it’s your job to brute force the correct table of possibilities which includes only about one hundred combinations.
We’re not really into felony theft and hopefully you’re not either. But, we have a nasty habit of needing to use a combination lock that’s been in a drawer for a few years and having no idea of what the correct code might be.
Update: We’ve had a lot of comments about shimming as a better method. For your enjoyment we’ve embedded a video after the break that details how to shim a Master lock using a beer can. Just remember: friends don’t let friends drink and shim.