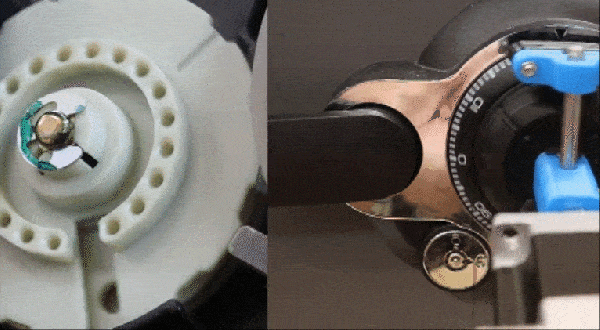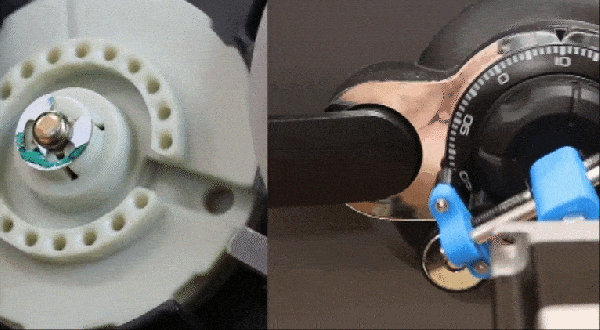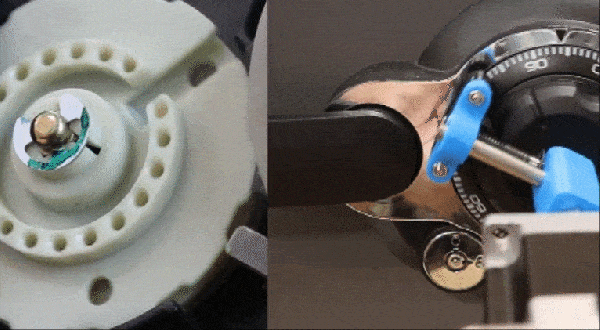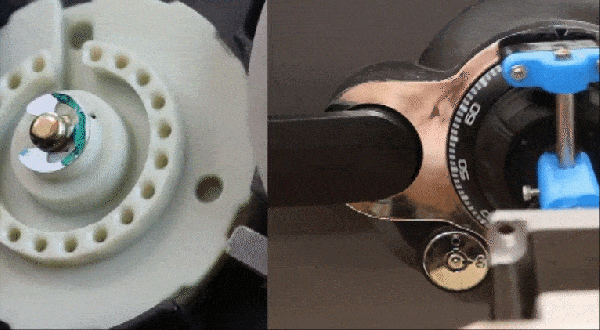
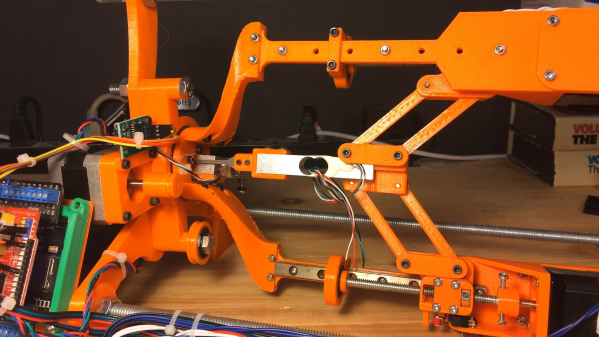
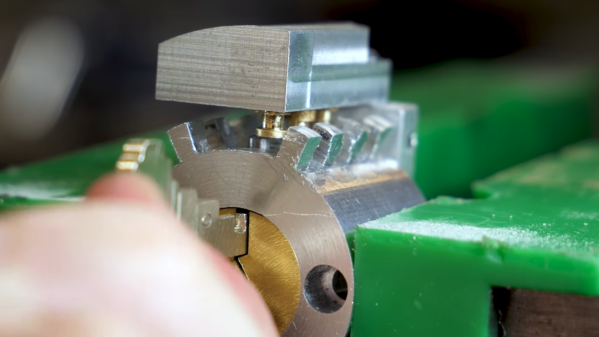
Having a robot that can quickly and unsupervised pick any lock with the skills of a professional human lockpicker has been a dream for many years. A major issue with lockpicking robots is however the lack of any sensing of the pins – or equivalent – as the pick works its magic inside. One approach to try and solve this was attempted by the [Sparks and Code] channel on YouTube, who built a robot that uses thin wires in a hollow key, load cells and servos to imitate the experience of a human lockpicker working their way through a pin-tumbler style lock.
Although the experience was mostly a frustrating series of setbacks and failures, it does show an interesting approach to sensing the resistance from the pin stack in each channel. The goal with picking a pin-tumbler lock is to determine when the pin is bound where it can rotate, and to sense any false gates from security pins that may also be in the pin stack. This is not an easy puzzle to solve, and is probably why most lockpicking robots end up just brute-forcing all possible combinations.
Perhaps that using a more traditional turner and pick style approach here – with one or more loadcells on the pick and turner- or a design inspired by the very effective Lishi decoding tools would be more effective here. Regardless, the idea of making lockpicking robots more sensitive is a good one, albeit a tough nut to crack. The jobs of YouTube-based lockpicking enthusiasts are still safe from the robots, for now.
Continue reading “A Lockpicking Robot That Can Sense The Pins”