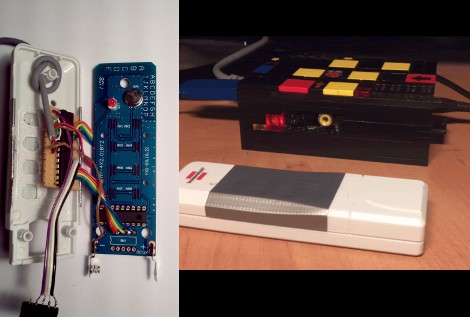
If you’ve been playing with electronics for long enough, eventually you’ll need a nice remote control transmitter to control your RC car, airplane, or any other robotics project you have lying around. With these robotics projects comes the problem remote control, and the XBee Handheld Controller may be just the ticket to remotely control any project that comes off your workbench.
This isn’t the first remote controller we’ve seen that does just about everything, but it is the first one to include an XBee wireless transceiver to easily interface to your robotics project. The controller comes in two models, the Q4, which uses four Playstation-like joysticks, and the Q2, which uses proper remote control gimbal joysticks. Both the controllers have a slew of buttons, toggle switches, four rotary pots and a 2×20 LCD display.
After the break you can check out [Paul]’s pitch explaining what these controllers can do and showing off a hexapod robot under the control of his Q4 controller. A very neat project, and we can’t wait to see this controller out in the field.
Continue reading “Remote Control With An XBee And A Propeller”