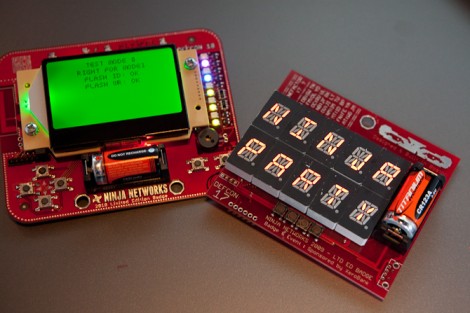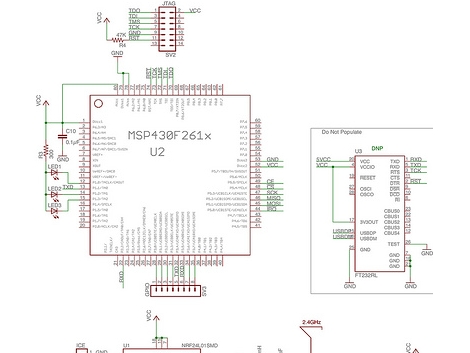
[Travis Goodspeed] is taking a look at the attendee badges for this year’s Next HOPE conference. He’s given us a pretty good look at what is on the board, what it means to you, and how you can get at it. Of course the final hardware specs are a secret until conference time, but this will help you get some ideas and ensure that you bring the right add-on hardware. We normally try not to do too much quoting, but one of [Travis’] statements literally makes us laugh out loud (as opposed to what most people describe as lol):
“These badges are active RFID tags which beacon the position of each attendee a few times a second, so that the god damned devil army of lies–by which I mean the Next HOPE badge committee–can track each attendee around the Hotel Pennsylvania.”
No matter how you feel about the badge committee, the tradition of hacking conference badges is a fun, rewarding, and often frustration past-time. The badges are actually using the concept of OpenAMD. The last three letters stand for Attendee Meta Data which is an evolving concept. How can meta data about attendees be useful to all involved in a non-invasive way? How about associating yourself with a concept, like microcontroller programming. What if you could search to find out where other people interested in that are right now? Could be great… could end up in an impromptu meeting around the restrooms for no good reason. Either way, take a look at the teaser video covering the topic after the break.
Oh, one more note about the hardware. This year they’re moving away from PIC based badges to the more energy-efficient MSP430 line. It’s not one of the value-line processors that the Launchpad is meant for, but this bigger-brother ‘F’ chip will be no problem to work with if you’ve already spent some time with the ‘G’ series.
Continue reading “Next HOPE Badge Hacking Primer” →