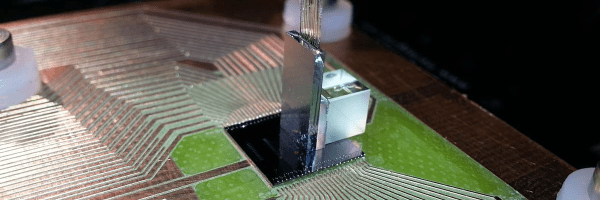
Entangled photons are an ideal choice for large-scale networks employing quantum encryption or similar, as photons can use fiber-optical cables to transmit them. One issue with using existing commercial fiber-optic lines for this purpose is that these have imperfections which can disrupt photon entanglement. This can be worked around by delaying one member of the pair slightly, but this makes using the pairs harder. Instead, a team at New York-based startup Qunnect used polarization entanglement to successfully transmit and maintain thousands of photons over the course of weeks through a section of existing commercial fiber, as detailed in the recently published paper by [Alexander N. Craddock] et al. in PRX Quantum (with accompanying press release).
The entangled photons were created via spontaneous four-wave mixing in a warm rubidium vapor. This creates a photon with a wavelength of 795 nm and one with 1324 nm. The latter of which is compatible with the fiber network and is thus transmitted over the 34 kilometers. To measure the shift in polarization of the transmitted photos, non-entangled photons with a known polarization were transmitted along with the entangled ones. This then allowed for polarization compensation for the entangled photos by measuring the shift on the single photons. Overall, the team reported an uptime of nearly 100% with about 20,000 entangled photons transmitted per second.
As a proof of concept it shows that existing fiber-optical lines could in the future conceivably be used for quantum computing and encryption without upgrades.




 As a self-professed “Crazy Laser Lady”, part of this investigation examined how components held up to big lasers delivering power far outside normal operating range. This turned up exciting effects like a fiber fuse (~17:30 in the video) which is actually a plasma fire propagating through the fiber optic. It looks cool, but it’s destructive and useless for covert attacks. More productive results came when lasers were used to carefully degrade select components to make the system vulnerable.
As a self-professed “Crazy Laser Lady”, part of this investigation examined how components held up to big lasers delivering power far outside normal operating range. This turned up exciting effects like a fiber fuse (~17:30 in the video) which is actually a plasma fire propagating through the fiber optic. It looks cool, but it’s destructive and useless for covert attacks. More productive results came when lasers were used to carefully degrade select components to make the system vulnerable.