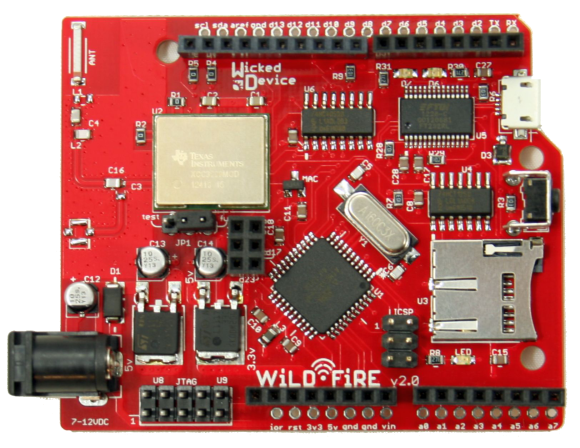
Wicked Device has released the WildFire board to the world. WildFire is a an Arduino compatible processor board with a Texas instruments CC3000. WildFire adds a few interesting features to the typical ‘Duino clone. Instead of the ATMega328 used in the Arduino Uno, the WildFire uses an ATMega1284p, which gives 16K of SRAM and 128K of Flash ROM (as compared to 2K RAM and 32K Flash in an Uno). A micro SD card slot is also on-board for data logging functions.
In the name of full disclosure, we should mention that [Adam] has known [Victor and Ken] over at Wicked Device for a few years now, and got his hands on a pre-release version of the board to play with. As with any non-standard Arduino board, the WildFire does require some modification to the Arduino IDE. This took a bit of time with the pre-release board. Wicked Device has streamlined the process since then. Everything is contained in a zip file on their product page. Once the IDE is up and running, its easy to get the WildFire’s CC3000 connected to your local access point. From there the internet is your playground. For those of you already asking “So, Hack?”, watch this space – Adam is working on a hack using the WildFire board which will show up in a few days.














