[Richard] and [Jay] needed a WiFi connected data logger for remotely monitored aquariums. After working diligently for three years, they’re finally finished. While the Knut was originally designed to keep tabs on a few huge aquariums, it’s more than capable to log all sorts of data and send those sensor readings to your email address.
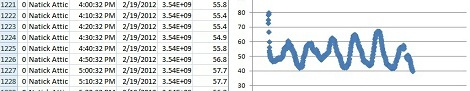
Knut is a small WiFi enabled device replete with a few plugs for temperature, humidity, accelerometer, and other sensors. All this data goes directly into the memory of Knut, and when the memory is full the data is sent to an email address. As a bonus, there’s also an iDevice app (Android and Windows coming soon) to parse the generated .CSV file and display the results on an iPhone
The Knut may be a touch expensive for our tastes, but if you’re looking for an off-the-shelf solution for sending alerts, logging data, or just reading a few sensors via WiFi, Knut may be just the ticket.
[Richard] and [Jay] put together a demo video showing off the capabilities and operation of the Knut app; check that out after the break.