It says it right on the title of the video below: it was bound to happen eventually. It’s only natural that somebody would stick a 3D printer extruder on the business end of a CNC machine. The long-awaited convergence of additive and subtractive manufacturing is here.
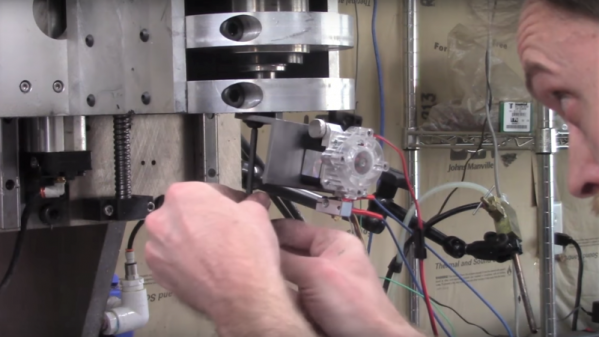
OK, that may be overstating things a bit, but we think [Chris DePrisco] is on to something here. Given the considerable investment he’s made in his DIY CNC machine, an enormous vertical machining center that looks a little like a homebrew Bridgeport, it was a no-brainer to take advantage of the huge XYZ stage. Mounting the Titan Aero extruder to the quill required some custom parts; fair warning that the video below is heavy on machining, but it’s not the seven hours of video he streamed when he milled the heated aluminum bed. Skip ahead to about the six-minute mark if you want to see the first prints and how he optimized the setup.
As we watched [Chris]’ video, we were struck by the potential for adding 3D printing to CNC milling machines. What we’d like to see is a setup where the spindle and the extruder work together to build more complex parts. Or maybe a tool-changing CNC that can pick up a spindle, an extruder, and maybe even a laser or plasma cutter head. Now that would be a powerful machine!
Continue reading “Additive + Subtractive = One Powerful Machine”