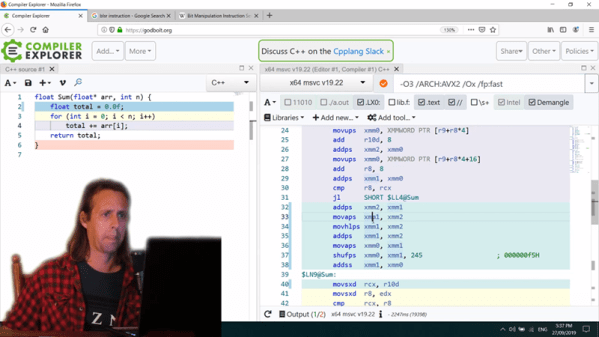
It wasn’t long ago that we introduced you to a web site, the Godbolt compiler explorer, that allows the visitor to compile code using a slew of compilers and compare their output. We suspect some number of readers said, “Wow! I can use that!”, while perhaps everyone else said, “Huh?” Well if you were in the second group, you ought to watch [What’s a Creel’s] video below where he walks through using the website. He looks at four different algorithms using four different compilers and it is a good example of how you might use the tool to make decisions about how you write software.
clang5 Articles
Crash Your Code – Lessons Learned From Debugging Things That Should Never Happen™
Let’s be honest, no one likes to see their program crash. It’s a clear sign that something is wrong with our code, and that’s a truth we don’t like to see. We try our best to avoid such a situation, and we’ve seen how compiler warnings and other static code analysis tools can help us to detect and prevent possible flaws in our code, which could otherwise lead to its demise. But what if I told you that crashing your program is actually a great way to improve its overall quality? Now, this obviously sounds a bit counterintuitive, after all we are talking about preventing our code from misbehaving, so why would we want to purposely break it?
Wandering around in an environment of ones and zeroes makes it easy to forget that reality is usually a lot less black and white. Yes, a program crash is bad — it hurts the ego, makes us look bad, and most of all, it is simply annoying. But is it really the worst that could happen? What if, say, some bad pointer handling doesn’t cause an instant segmentation fault, but instead happily introduces some garbage data to the system, widely opening the gates to virtually any outcome imaginable, from minor glitches to severe security vulnerabilities. Is this really a better option? And it doesn’t have to be pointers, or anything of C’s shortcomings in particular, we can end up with invalid data and unforeseen scenarios in virtually any language.
It doesn’t matter how often we hear that every piece of software is too complex to ever fully understand it, or how everything that can go wrong will go wrong. We are fully aware of all the wisdom and cliches, and completely ignore them or weasel our way out of it every time we put a /* this should never happen */ comment in our code.
So today, we are going to look into our options to deal with such unanticipated situations, how we can utilize a deliberate crash to improve our code in the future, and why the average error message is mostly useless.
Continue reading “Crash Your Code – Lessons Learned From Debugging Things That Should Never Happen™”
Warnings On Steroids – Static Code Analysis Tools
A little while back, we were talking about utilizing compiler warnings as first step to make our C code less error-prone and increase its general stability and quality. We know now that the C compiler itself can help us here, but we also saw that there’s a limit to it. While it warns us about the most obvious mistakes and suspicious code constructs, it will leave us hanging when things get a bit more complex.
But once again, that doesn’t mean compiler warnings are useless, we simply need to see them for what they are: a first step. So today we are going to take the next step, and have a look at some other common static code analysis tools that can give us more insight about our code.
You may think that voluntarily choosing C as primary language in this day and age might seem nostalgic or anachronistic, but preach and oxidate all you want: C won’t be going anywhere. So let’s make use of the tools we have available that help us write better code, and to defy the pitfalls C is infamous for. And the general concept of static code analysis is universal. After all, many times a bug or other issue isn’t necessarily caused by the language, but rather some general flaw in the code’s logic.
Continue reading “Warnings On Steroids – Static Code Analysis Tools”
Warnings Are Your Friend – A Code Quality Primer
If there’s one thing C is known and (in)famous for, it’s the ease of shooting yourself in the foot with it. And there’s indeed no denying that the freedom C offers comes with the price of making it our own responsibility to tame and keep the language under control. On the bright side, since the language’s flaws are so well known, we have a wide selection of tools available that help us to eliminate the most common problems and blunders that could come back to bite us further down the road. The catch is, we have to really want it ourselves, and actively listen to what the tools have to say.
We often look at this from a security point of view and focus on exploitable vulnerabilities, which you may not see as valid threat or something you need to worry about in your project. And you are probably right with that, not every flaw in your code will lead to attackers taking over your network or burning down your house, the far more likely consequences are a lot more mundane and boring. But that doesn’t mean you shouldn’t care about them.
Buggy, unreliable software is the number one cause for violence against computers, and whether you like it or not, people will judge you by your code quality. Just because Linus Torvalds wants to get off Santa’s naughty list, doesn’t mean the technical field will suddenly become less critical or loses its hostility, and in a time where it’s never been easier to share your work with the world, reliable, high quality code will prevail and make you stand out from the masses.
Continue reading “Warnings Are Your Friend – A Code Quality Primer”
A Real Hacker’s IDE
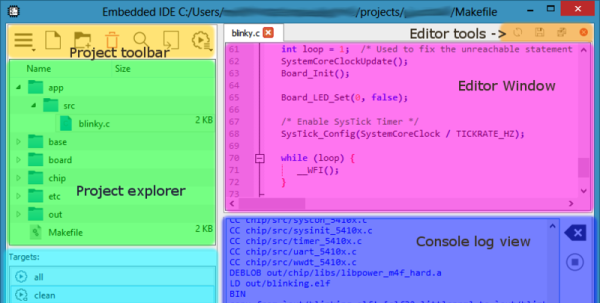
We don’t use a GUI IDE, but if we did, it would most certainly be something along the lines of [Martin]’s embedded-IDE project. We’ve always felt that most IDEs are just fancy wrappers around all the tools that we use anyway: Makefiles, diff, git, ctags, and an editor. [Martin]’s project makes them less fancy, more transparent, and more customizable, while retaining the functionality. That’s the hacker’s way — putting together proven standard tools that already work.
The code editor he uses is QScintilla, which uses clang for code completion. The “template” system for new projects? He uses diff and patch to import and export project templates. Because it uses standard tools all along the way, you can install the entire toolchain with sudo apt-get install clang diffutils patch ctags make on an Ubuntu-like system. Whatever compiler you want to use is supported, naturally.
We can’t see a debugger interface, so maybe that’s something for the future? Anyway, if you want a minimalistic IDE, or one that exposes the inner workings of what it’s doing rather than hiding them, then give [Martin]’s IDE a try. If you want more bells and whistles that you’re not going to use anyway, and don’t mind a little bloat and obscuration, many of our writers swear by Eclipse, both for Arduino and for ARM platforms. We’ll stick to our butterflies.