We all lead digital lives, and we work in and on files of one sort or another. And sometimes we get attached to them. That long manifesto you poured your heart into, but nonetheless probably shouldn’t see the light of day? Love letters from former flames? Your first favorite video game that you can’t play any more, but it just sits there eating up drive space?
These are the files that are important enough that they deserve better than just a drag-and-drop into the trashcan. They deserve to be buried with dignity, and that’s just what [Ulf Schleth]’s /death/null offers us – a digital graveyard where our files no longer exist as they were, but still are allowed to linger in memory.
This is an old project, but one that tickled our funny and poignant bones in equal parts. The pun on /dev/null probably works just a little better if you read both filepaths with a German accent in your head, but the idea translates anyway.
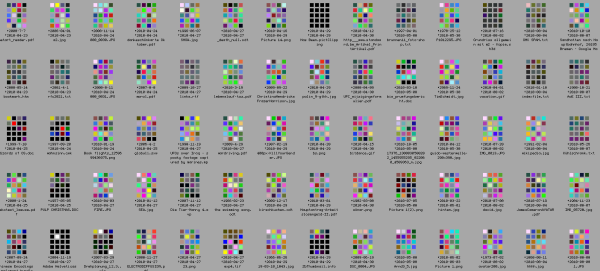
To use it, you simply upload your file and it gets sent to the great trashcan in the sky, but along the way a 4 x 5 matrix of colored blocks is created that represents the file, and it is registered forever in the graveyard, where you can check up on it any time you like. Of course you can’t read it – only 20 RGB triples remain – but you have the digital “gravestone” as commemoration.
Even if you don’t have any loved ones in [Ulf]’s graveyard, you can walk by and see which files others have chosen to remember. Swing on by and pay your respects to notepad.exe.