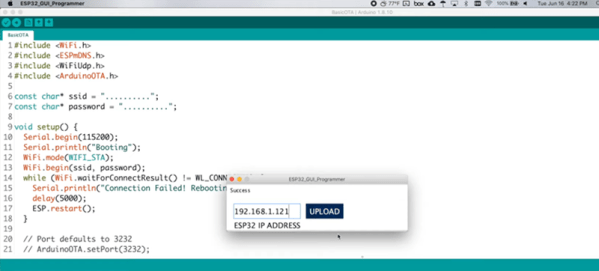
One of the disadvantages of having cheap WiFi-capable boards like those based on the ESP32 is that you have to update them. If you have even a few in every room of your house, it can be a pain to pull them out and connect them to a cable for programming. Over the air programming is a great answer, and [Kevin] shows how you can control the update via a simple GUI. You can see a video demonstration of how it works below.
[Kevin] uses a ready-made OTA library to do the work, but creates a GUI configuration and downloader tool. There is a manual step to force the board into the OTA mode, which might be a mild inconvenience, but it improves security since you need physical access to the device to do an update.