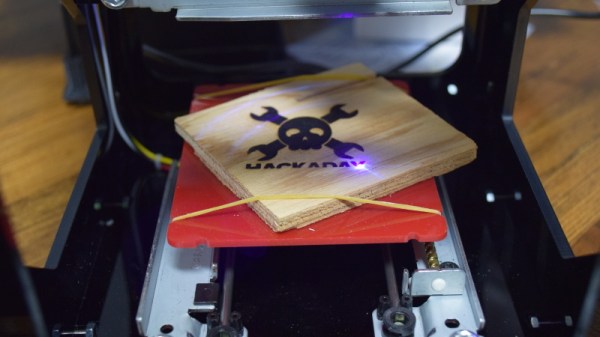
When I got my first 3D printer I was excited, but now that I’m contemplating adding a forth to my collection, I have to come to the terms with the fact that these machines have all the novelty of a screwdriver at this point. Which is fine; getting the cost down and availability up is the key to turning a niche piece of technology into a mainstream tool, and the more people with 3D printers at home or in their workshop the better, as far as I’m concerned. But still, there’s a certain thrill in exploring the cutting edge, and I’ve been looking for something new to get excited about as of late.

Lasers seem like an interesting next step in my quest towards complete in-house fabrication capability, so I started researching cheap setups to get my feet wet. In the course of looking up diode-powered laser cutters, I came across the NEJE DK-8-KZ. At only 1W, there’s no question this device isn’t going to be cutting a whole lot. In fact, it’s specifically sold as an engraver. But given the fact that you can get one of these little guys for around $70 USD shipped, it’s hard to complain.
Now I wasn’t 100% sure what I would do with a laser engraver, but I thought it would be a good way to test the waters before putting serious money (and time) into something more powerful. Plus, if I’m being totally honest, I wanted to start on something on the lower end of the power spectrum because I’m terrified of blinding myself.
So what kind of laser do you get for $70? Let’s find out… Continue reading “Review: NEJE DK-8-KZ Laser Engraver”