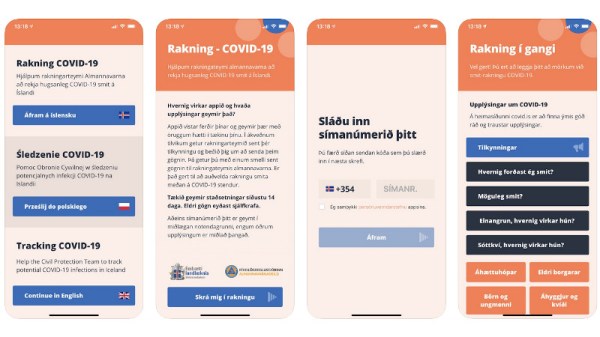
As governments around the world grapple with the problem of tracing those who have had contact with a person known to have been infected with the COVID-19 virus, attention has turned to the idea of mobile apps that can divulge who a person has been near so that they can be alerted of potential infections. This has a huge potential for abuse by regimes with little care for personal privacy, and has been a significant concern for those working in that field. An interesting compromise has been struck by Iceland, who have produced an app for their populace that stores the information on the device and only uploads it with the user’s consent once they have received a diagnosis. We can all take a look, because to ensure transparency they have released it as open source.
On signing up for the scheme a central server stores the details of each user as well as their phone number. When the epidemiologists have a need to trace a person’s contacts they send a notification, and the person can consent to their upload. This is a fine effort to retain user privacy, with depending on your viewpoint the flaw or the advantage being that the user can not have their data slurped without their knowledge. Iceland is a country with a relatively small population, so we can imagine that with enough consent there could be effective tracing.
We installed the Android version on the Hackaday phone to have a look, but unfortunately it seems to need to be in Iceland to be of use enough to explore. We would be interested to hear from our Icelandic readers, to hear their views. Meanwhile readers can juxtapose the Icelandic app with another proposal for a more anonymised version.