[aleaksah] got himself a Mi Smart Kettle Pro, a kettle with Bluetooth connectivity, and a smartphone app to go with it. Despite all the smarts, it couldn’t be turned on remotely. Energized with his vision of an ideal smart home where he can turn the kettle on in the morning right as he wakes up, he set out to right this injustice. (Russian, translated) First, he tore the kettle down, intending to dump the firmware, modify it, and flash it back. Sounds simple enough — where’s the catch?
This kettle is built around the QN9022 controller, from the fairly open QN902X family of chips. QN9022 requires an external SPI flash chip for code, as opposed to its siblings QN9020 and QN9021 which have internal flash akin to ESP8285. You’d think dumping the firmware would just be a matter of reading that flash, but the firmware is encrypted at rest, with a key unique to each MCU and stored internally. As microcontroller reads the flash chip contents, they’re decrypted transparently before being executed. So, some other way had to be found, involving the MCU itself as the only entity with access to the decryption key.
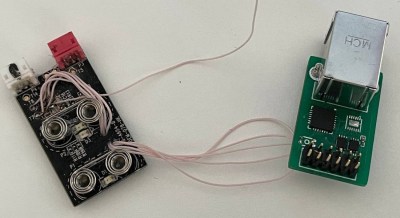 [aleaksah] considered the SWD interface, a powerful debug interface and a fairly common go-to for internal data access of many MCUs. Sadly, this microcontroller has lock bits for blocking SWD, intended to be set as your product leaves the factory floor. Of course, not every manufacturer sets those bits, but after checking the SWD interface anyway, it wouldn’t respond, and he decided to go the other way. He rejoiced, finding documentation on the MCU’s internal bootloader, and decided to load his own code into RAM that would dump the flash contents from the inside. However, the read command seems to have triggered the bootloader to either scramble or erase the flash, leaving him with a dead unit.
[aleaksah] considered the SWD interface, a powerful debug interface and a fairly common go-to for internal data access of many MCUs. Sadly, this microcontroller has lock bits for blocking SWD, intended to be set as your product leaves the factory floor. Of course, not every manufacturer sets those bits, but after checking the SWD interface anyway, it wouldn’t respond, and he decided to go the other way. He rejoiced, finding documentation on the MCU’s internal bootloader, and decided to load his own code into RAM that would dump the flash contents from the inside. However, the read command seems to have triggered the bootloader to either scramble or erase the flash, leaving him with a dead unit.
He persevered, and decided to study the bootloader code itself, loading yet another RAM stub that would dump the bootloader code. After decompiling the bootloader, apart from a few undocumented but uninteresting commands, he found out that loading any kind of program, indeed, sends the flash chip a command to perform a flash erase. From here, he could theoretically do a tweezer hack, write-protecting the flash by short-circuiting its data pins – yet, he decided to find a proper dumping method that would extend to the chips with built-in flash, should one of those appear on our desks.
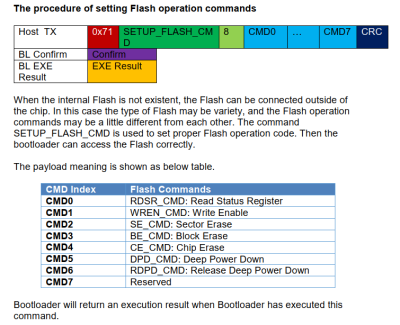 His key discovery came soon thereafter. Different SPI flash chip families have different commands for read/write/erase and other operations, and the bootloader exposes a structure you can modify to use different commands for the kind of flash chip you have connected. Simply substituting the flash erase command in that structure with something harmless resulted in the flash contents staying intact even after new code was loaded externally into RAM. As a result, [aleaksah] has discovered a method for dumping encrypted-at-rest firmware from any QN902X series MCU, using nothing but a USB-UART, the chip’s built-in bootloader and a small code dumping stub (GitHub).
His key discovery came soon thereafter. Different SPI flash chip families have different commands for read/write/erase and other operations, and the bootloader exposes a structure you can modify to use different commands for the kind of flash chip you have connected. Simply substituting the flash erase command in that structure with something harmless resulted in the flash contents staying intact even after new code was loaded externally into RAM. As a result, [aleaksah] has discovered a method for dumping encrypted-at-rest firmware from any QN902X series MCU, using nothing but a USB-UART, the chip’s built-in bootloader and a small code dumping stub (GitHub).
Another day, another firmware readout protection mechanism circumvented! Finding such exploits is beneficial for a lot of fun journeys, like the recent hack that helps us tap into myriads of STM32-powered devices out there. You can even use the abundant ST-Link programmers as your training ground! If the SWD interface isn’t unlocked on your device, check out this educational journey about modding a third-party Xbox controller using SWD. Wonder how to modify the firmware you dumped? We’ve just covered a hacker modding their Kurzweil synthesizer’s firmware with Ghidra!















I was going to comment on the absurdity of a kettle with a microprocessor in it until I remembered that my lightbulbs all have a micro in them.
At least it’s not a toaster.
At least if you can turn your kettle on remotely, when you’ve forgotten to put water in it and the cut-out has failed, you can burn your house down while you are not in it.
Unfortunately I’ve ruined my share of kettles. Didn’t “burn the house down” but the usual overheated smell, and a new kettle on order.
How‽ You buy kettles from Aliexpress or how? All, even the most cheapest kettles where I live have had an overheat protection which works without any water for at least two decades minimum.
They’re regular stove kettles.
Tried a cast iron one? :-D
This is the first time I have ever seen an interrobang in the wild!
Well, if you’re planning to burn your house down, it’s best to do it when you’re not in it.
Now, that’s smart, but I wonder what insurance companies would have to say about it. Is the “cheap IoT kettle burned down the house” included or excluded from the policy?
I use a regular kettle and a smart outlet. The kettle will only heat if I have flipped the switched on the kettle before hand, and I only do that if I’ve filled the kettle.
Lightbulbs are a reasonable thing to control remotely, be it from the sofa or outside the house. They have no dependencies other than electric and internet, and offer nothing to the user other than a continuous stream of light and heat when turned on.
A kettle has dependencies of electric, internet and water. Furthermore, the boiled water has no purpose if it is left to sit in the kettle (unless you somehow hacked it to make a sauna). To get benefit from the kettle you need to get off your backside, go to the kettle and then pour the water to where it’s needed, the app can’t do that bit.
Actually just had a thought, you could pre-fill the kettle, then when watching Corry wait for the little rotating black & white thing in the corner implying the ads are coming, then flick the kettle on from your armchair so the water’s ready by the time the ads come.
For me though, the time taken to prepare the contents of the cup pretty much equals the time for boiling the water for that cup, so having ready-boiled water wouldn’t save any time.
or better yet, let the National Grid have access to your kettle so they can peak-shave by controlling the active kettle demand during Corry. You just have to make sure you’re ready when it boils…
I was thinking a remote filling unit, that you prefill with multiple kettles worth of water, that will dispense the right amount each time it is triggered. Maybe include a cutout that will disconnect your kettle from power when the dispense is out of water, and a water sensor that will prevent the dispense from activating when the kettle already has water in it. (And the remote filling unit might even just connect straight to your water lines, so that it doesn’t even need to be filled,and just turns on a tap into the kettle to fill it.)
I suppose if you’re that lazy, just take a flask of tea into the living room with you.
I have a smart Kettle. When I get out of bed in the cold mornings it’s great to not have to spend a single second more than I have to on the cold tiles.
When I’ve had a really bad day I turn it on on my way home and the water is ready when I walk in the door.
When you’re cuddling and rocking a baby and trying to calm them down at 3am while waiting for the water to warm up without getting too hot for a bottle, the ability to control it with your voice is incredible. Out of the smart home equipment we have it’s used more than just about anything else.
I made an arduino based kettle. the microprocessor allows you to use a time out as well as the thermostatic function. there’s also the possibility to power on in the off state to avoid perpetual boiling with intermittent electricity and to avoid arcing at the mains plug.
all these features should extend the life of the device, and would have in mine if i wasn’t a terrible programmer ;)
I’ve been using mine for 5 years now, and hope to fix the software bug that burned out two elements soon.
Recently, I saw a kettle that requires setting the desired temperature through a couple of small buttons on the handle. Even if you just wanted the same temperature as last time, it still required 3 keypresses to activate it.
I own that kind of kettle. While I admit the interface is not optimal, it is well appreciated by the family as every one here as a hot water temperature preference (how crazy is that?). And past the first weeks usage, we now do the 3 clicks very fast without even thinking about it. I guess human adaptation surpasses technological flaws!
Now, could we get a fingerprint recognition with temperature profiles recalled at startup ? That would be nice…. and overkill ^^
Just be glad the toaster guys didn’t design it, or it would be like 120 levels of “feels like room temperature still” at the bottom, and 120 levels of “boiling violently” at the top, and a handful in between the two.
What features does ‘IOT’ add to a kettle? It can’t start remotely, as a safety feature if there’s no water in I guess. So, errr it reports your kettle usage back to Xiaomi? Gives you a ping on your phone when the kettles boiled? (Trying to imagine situations where you would put a kettle on to boil and be distracted enough that you forget about it).
OK looked at the product, it’s basically a bluetooth enabled digital urn in the form factor of a kettle. You can seemingly set temperatures in intervals of 10C to hold the water at (for up to 12 hours). Interestingly it says you can boil water in 5 minutes, seems a bit slow… But yeah, you might have expected a water level sensor to allow for remote activation.
“Interestingly it says you can boil water in 5 minutes, seems a bit slow…”
It’s a 1.8 kW kettle. 5 minutes is pretty much dead on.
Europeans may have a different experience with electric kettles. I once spent hours on a Reddit thread about tea, and I learned that European kettles are generally 3kW, which would draw 25 amps on American 120V mains power. (For reference, most American sockets are only 15 amps, and even the high current ones are generally only 20 amps. You would have to use an oven socket (30 amps) to get as much power as a European 3kW kettle.) So anyhow, the typical European electric kettle is probably boiling water in under half the time, so 5 minutes would seem rather long. In the U.S. though, 5 minutes is about the fastest you can get (as 1.8kW is exactly at the 15 amp limit, and the only appliance I’ve ever seen in the U.S. with the 20 amp plug is an AC unit).
This is why the guy I bought my house from (who built it) ran a 240V circuit throughout the kitchen with Australian style plugs. He apparently had an Australian coffee maker to plug into one…
“(Trying to imagine situations where you would put a kettle on to boil and be distracted enough that you forget about it)”
AD(H)D ‘ll do the trick.
The funniest fact about the supposedly smart kettle is that turning it on remotely is the only useful application, but they probably disabled it out of fear something bad might happen when kettles turn on by themselves…
The day kettles become sentient and overthrow their masters.
It is not that tough. I have a Keurig coffee maker with a turn on timer. It simply does not engage the heater if the water level is too low.
You can easily avoid that by using the same principle as a rice cooker, with a magnet that demagnetizes itself when the temperature is above the boiling temperature of water, falling down and disconnecting the power to the heater. Purely mechanical system, no need for electronics for it. Can easily work for a coffee maker, a kettle, etc.
I tried to make a custom web interface to control my kettle but I just kept getting a HTTP 418 error.
:iseewhatyoudidthere:
The really strange part here is that there is no way that the firmware for a freaking water heater could ever be a secret remotely worth the investment that ultimately went into their ultimately broken attempt at “protection”.
There’s a whole industry of people selling mostly snake oil methods to hide code that would be trivially reimplemented if it had any value to anybody in the first place. And paying such parasites, and/or spending valuable time and resources to turn on the nonsense they produce, seems to be the “conventional wisdom”.
With every connected device becoming an attack vector for hacks and other ransomware I can understand how they would try to protect their firmware. Clearly not infallible but maybe they’ll improve next rev. And it gives us some interesting challenges:)
I’m sorry, but I don’t buy that at all.
First, trying to keep your code secret is not an effective measure for protection against “hacks”. At least until you get *way* further along than any of these companies typically do, any resources you might put into that, however minor, are far better put into making the code actually resist attacks. In fact, I’m not sure I’ve ever seen any organization, anywhere, that had managed to get to a level of software maturity that would let htem justify diverting resources toward trying to keep the code secret on “security” grounds.
As for this specific case, making a boneheaded mistake like the one described is pretty clear evidence of not being anywhere near that point. If they think they’re protecting against botnets, ransomware, or whatever, by keeping their firmware secret, it is because they don’t have the slightest understanding of the actual threat landscape, NOT because it’s actually true.
Furthermore, if any of these manufacturers actually cared about that stuff *for real*, either they would not put devices on the Internet “just because they can”, or they would have meaningful secure development programs and well-defined, functional processes for security updates throughout the potentially useful lifetimes of the devices (and not just their “marketing lifetimes”). Although I can’t actually say anything specific about this case, I have never seen one of these appliance manufacturers that had anything meaningful along those lines.
Second, the “protection” systems themselves tend to add dangerous attack surface.
What I *have* heard from companies like that is a bunch of bleating about how critical it is to “protect their innovative intellectual property”. And that’s also how the “protection” features in microcontrolers are marketed to the final device manufacturers. So I still believe that 99.99 percent of these cases are idiots buying snake oil.
In this (and most cases) you have to have physical access to the device. Only this device is compromised – not all of them.
The level of effort by the vendor here is trivial – chip already inline encrypts/decrypts its contents using perMCU unique internal key. Disabling SWD is a fuse bit. Code to detect a new program and wipe flash is trivial.
But even with this trivial level of effort – the device is still protected from the vast majority – who have no knowledge, skills, or desire to compromise it.
So I think you are just ranting.
The only real issue here with IOT devices are ones that allow OTA firmware updates, or report home with data – which can be handled at the network level with no changes to the device.
What makes you think only this device is compromised? The encryption here isn’t to verify code is signed, just to hide the code itself. If that’s their goal, then it’s failed. Unless each unit has its own firmware, cracking open the encryption is certain to give at least 2 ways to get RCE, which is what you need for an “iot botnet”. As for security through obscurity, the unit never had any security in the first place. Cracking open the firmware isn’t strictly necessary to exploit the device, it just makes the process faster.
Or could be in place preventing an invading country from reenacting the modern equivalent of O’Leary’s cow burning down a city. The war of the kettles.
olga of kiev burned a city to the ground by tying burning sulphur to birds.
https://en.wikipedia.org/wiki/Olga_of_Kiev#Drevlian_Uprising
RFC 1149 zero day vulnerability.
SSR typically fail closed circuit is probably the reason why the automatic fire starter mode is not enabled on the kettle.
Not too tough to add a temperature switch to interrupt mains power in the event of an overheat.
That’s one of the tests Underwriter’s Laboratories does with coffee pots, electric kettles and other heating appliances. Will they fail safe if in an overheat condition?
One has to be impressed with the determination of this dedicated hacker.
A smart kettle that couldn’t be turned on remotely. What the heck else would anyone want out of a smart kettle? And the endless security hurdles in the thing. All kinds of engineering where it does nobody but the manufacturer any good.
Personally, I would have given this thing an ESP module transplant.
Indeed, one would expect some kind of overtemp sensor, most likely in hardware. My “dumb” kettle at least can turn itself off reliably (I boiled enough kettles dry on the stovetop before I got it, it has been a godsend). I’m not sure what advantage remote turn on would have since I usually fill it with water then turn it on immediately afterwards.
Weird mode of protection, one would expect it to erase the internal encryption keys instead of erasing the flash. But I guess even a 16 bytes of internal eeprom would be difficult to add when aiming for the cheapest CMOS processes.
I’ll stick with my Goblin Teasmade, thank you very much.
https://en.wikipedia.org/wiki/Teasmade
Secure Boot would have prevented modifying the bootloader.
Just get an inline switch with an RF remote. Put the remote on your bedside table and poke it when you wake up. Or get a mechanical 24 hour timer with a lot of settings to turn the kettle on, then off in the morning.
Yeah, I’m still baffled with the idea of a smart kettle.
Mine is 3kW. I add a mug full of water and press ‘On’.
Add coffee and sugar to the mug, retrieve milk from the fridge and the kettle has almost boiled already.
Smart kettles strike me as a classic example of creeping featurism. My own favourite high technology kettle is Colin Furze’s Jettle – though I don’t have one myself as it has a tendency to set fire to the ceiling, as well as there being noise problems.
https://www.youtube.com/watch?v=-fDM9Eb16Do
Didn’t the Goblin Teasmade achieve more or less the same thing without Internet connectivity? Just fill the kettle and set the alarm and you wake up to a pot of freshly brewed tea, or a live test of your smoke alarms! (-:
That said, I could see this being useful in countries with 110v mains. Any American will tell you that plug-in kettles take forever to boil (That’s why they use traditional stove kettles) so pre-filling and being able to set the kettle going as you’re setting off home from work might be practical. But as US households have split-phase supply (2x opposing 110v lives either side of a common neural) a BS1362 outlet wired across both lives* would do the job equally as well, and the British love of Tea means there certainly won’t be a shortage of kettles with British plugs on them! ;-)
(* – But unlike in British setups; You’d need a dual pole isolator/switch as both “Live” and “Neutral” pins would have potential in that sort of implementation.)
As to whether a “Smart” kettle is really necessary – As opposed to merely convenient – Is entirely a matter of personal opinion. You don’t need “smart” appliances to hand load control over to your energy supplier; A dedicated socket controlled by your smart meter could let any primed “dumb” appliance (Kettle, toaster, fan heater etc) start-up whenever local conditions favour it. This could do wonders for smoothing surges and dips in supply voltage whilst affording no greater inconvenience then maybe waiting a few seconds. :-)
This is pretty cool but Smarters iKettle already does this. Problem I have with them is the kettle heating elements always going out and literally no one will sell parts for them.
Struggling to understand why they went to so much trouble to not just encrypt but delete on attempted read… what were they trying to hide? More skyward?