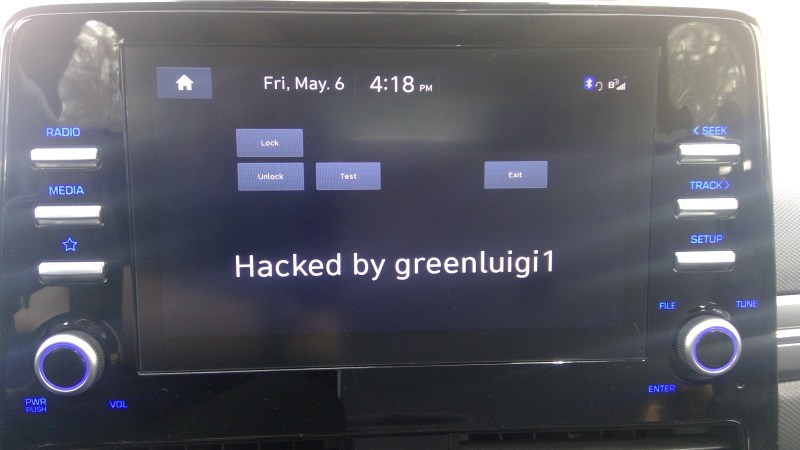
[greenluigi1] bought a Hyundai Ioniq car, and then, to our astonishment, absolutely demolished the Linux-based head unit firmware. By that, we mean that he bypassed all of the firmware update authentication mechanisms, reverse-engineered the firmware updates, and created subversive update files that gave him a root shell on his own unit. Then, he reverse-engineered the app framework running the dash and created his own app. Not just for show – after hooking into the APIs available to the dash and accessible through header files, he was able to monitor car state from his app, and even lock/unlock doors. In the end, the dash got completely conquered – and he even wrote a tutorial showing how anyone can compile their own apps for the Hyundai Ionic D-Audio 2V dash.
In this series of write-ups [greenluigi1] put together for us, he walks us through the entire hacking process — and they’re a real treat to read. He covers a wide variety of things: breaking encryption of .zip files, reprogramming efused MAC addresses on USB-Ethernet dongles, locating keys for encrypted firmware files, carefully placing backdoors into a Linux system, fighting cryptic C++ compilation errors and flag combinations while cross-compiling the software for the head unit, making plugins for proprietary undocumented frameworks; and many other reverse-engineering aspects that we will encounter when domesticating consumer hardware.
This marks a hacker’s victory over yet another computer in our life that we aren’t meant to modify, and a meticulously documented victory at that — helping each one of us fight back against “unmodifiable” gadgets like these. After reading these tutorials, you’ll leave with a good few new techniques under your belt. We’ve covered head units hacks like these before, for instance, for Subaru and Nissan, and each time it was a journey to behold.















Liberation projects always make mMe happy. I’m curious though, do they not use secure-boot and dm-verity?
The world is slowly locking us out because signing and fusing keys has become so easy ..
. which will be unsolvable unless a) we get the keys (will never happen), b) a secondary user key can be used (not supported in any soc AFAIK) c) bootloader unlockin, which only gives you partial (but acceptable) freedom (super unlikely, especially on existting stuff). d) signed shim chainloaders (a possibility) …
In 70s and 80s car tinkerers relying on folk wisdom and word of mouth tried to optimize carbs for better fuel performance in their Fiats 125p, 126p, FSO Polonez and other grand examples of socialist engineering. One of the “tricks” was to stick a needle into carb’s nozzle. Usually result was premature engine damage from excess heat (as if those FSO engines weren’t bad enough already) and even worse performance because it was running far too lean. Alternatively fuel economy only worsened because “tweaks” made it run too rich. Then came imported, fuel injected cars of 90s-00s and you couldn’t tweak them with a screwdriver anymore. Is it bad? The price of progress I guess. My Mazda 323 did 380,000 km without any major failures, it was scrapped only because body turned to rust. Engine itself was perfectly fine and I’ve sold it online. FSO Polonez required full engine overhaul after less than 150,000 km.
I’m quite sure either you or another commenter can clarify, but your comment was a tad confusing. Did the “hack” result in it running too lean or too rich or were you discussing two different “hacks”.
People have hacked EFI engines and projects like Megasquirt and Speeduino will allow you to run almost anything… every new technology is hacked sooner or later.
Back in the fourth-gen F-body days, car geeks were adjusting stock ECUs on their Camaros and Firebirds with lt1edit and getting good results.
These days, things are much more locked down.
But there are also aftermarket ECUs from some of the same companies who made their name selling aftermarket carbs, like Holley, in addition to full-hacker mode kits like Megasquirt.
I think you’ll be happy to know that the linux version has also been hacked… https://g4933.gitlab.io/wideopen/
This is great and all, but I have a nagging feeling that things won’t go well if the car is involved in a crash, and the other party[s] subpoena the car’s software.
Let me add more FUD to that FUD: I think that [greenluigi1] is quicker with responding to such requests as Hyuandi ever will be.
How is this different from a guy replacing his own brake pads? This is exactly the kind of fear mongering manufacturers employ to discourage modifying the software of your property. That ship has sailed a century ago, so it’s weird to now bring it up.
brake pads are pretty straight forward and easy to test…this has access to CANBUS, so it can do all kinds of crap, there already was some research done into fuzzing CAN and it does not respond in a predictable manner…
Infotainment CAN bus is NOT the engine CAN bus. I´d eat my hat if a modern car like this has only one CAN bus.
Besides that, infotainment HW/SW is most of the time outsourced, and no sane car manufacturer would hand over the engine CAN bus to a third party, their liability would be engaged.
So, you can try hard to do something nefarious from the infotainment software, it´s certainly possible but normally quite difficult.
probably generally true, but didn’t they get engine CANbus control over that jeep they crashed in the POC via a radio hack?
> Infotainment CAN bus is NOT the engine CAN bus
Yes, there should be a firewall that blocks access to the CANBUS to avoid exploitation through the head-unit.
But that entirely depends on whether or not the mfg was bother enough to do it..
Odb2 dongles have canbus access too, so what? If you don’t screw your wheels hard enough, they can fall out and if you’re going highway speeds you die, all your passengers die and other people driving near you probably die too(or get injured). It’s a risk we all take everyday. Imagine a world where you cant take and replace your wheels in your car.
This kind of talk encourages corps to take away our rights to tinker with our stuff – which would be a lot safer if they just gave us proper access to the software.
Because replacing brake pads is “grandfathered” in, but hacking your car’s software is legally new territory, and in a legal action any lawyer worth his slime will be all over it.
There’s a difference between replacing your own brake pads and replacing your own brake pads with brake pads you made yourself in your shed.
That’s the (potential) issue here – modern cars are very connected on multiple CAN buses, and often in ways that can cause bad interactions if you start hacking on it. Yes it’s bad, no it shouldn’t be like that, and no your stereo should not be able to affect your engine or ABS… but there’s a risk it could because sometimes they’re sitting on the same wires. That may or may not be the case here.
Now, a project like this that seems very well documented and executed by someone who clearly knows their stuff I suspect he’d be willing and more than capable of standing up in court and arguing with the insurance company or whoever about it – but the average HaD reader hot-glueing an Arduino into their car and futzing with the CANbus may not be so inclined.
Much like chainsaw juggling, the message is not “don’t do it”, simply to stop & think before doing it.
Fortunately, we still have modern brake pads to haul things to a stop, then, eh?
It isn’t but the first law of HaD comments is that some ninny is required to say some version of YOU WON’T BE INSURED FOR THAT, no exceptions. Another requirement is that the poster saying this cannot be a lawyer or insurance adjuster etc.
Regardless of who says it, truth is truth.
There’s a difference between letting me do maintenance on my own car, and letting anybody with internet access to my car do what they will with it.
If I’m worried about the physical security if my car, then I have a reasonably good idea of what steps I should take to physically secure it. Sure, I could worry about parking my car in public, and you might be right to tell me that I’m paranoid. You might also be right to tell me that I’m stupid/naive to park it in certain alleyways at night in certain neighborhoods. The point is that we actually do think about how to keep it from getting broken into or disabled already.
What if somebody figured out how to do this with internet access? Now that most new cars have sim cards and Bluetooth connections, Some even have wifi, the fundamental risk is higher. What if somebody could just connect a USB device inside the car or under the hood and affectively disable the car? Or unlock the doors and tell it that the key is present? Or worse, install malicious software? What if the NSA had the right to install tracking software in your car without a warrant? (They actually do that today).
Do I want to be able to modify my car however I see fit? Yes. Do I want other people to be able to easily modify my car with a thumb drive or ssh access? No.
Pwn!!!
yes ^__^
Im curious about the speedometer, mostly hyundai vehicles store their mileage in a EPPROM inside the dashboard, will this hack be able to get hands over the EPPROM? if yes, then will be a pandora box for any hyundai customer …
Was wondering if someone could do the same hack for Honda fit GK?
No, it can’t, the dash holds its own number, the real number is in the main computer.
at least in EU, authorized service and state inspection log the odometer and this data is publicly available…if your car shows a sudden drop in the logs, it’s been messed with…
And it will not pass yearly inspection (at least in Poland).
you could (not that I’m recommending it) roll it back every year before the inspection to when it was last logged.
I like this for one reason only. Stock UI is the worst. Any car. Frivolous animations, terrible control schemes. The settings you need most buried in sub menus. This at least gives me hope someone could fix it.
putting this on my reading list! More of these kinds of articles!
Great article! I love these kinds of hacks. Please more of this!
Well, I hope that our fellow hackers do more of these! (and send them in too!)
It’s your lucky day hahahaa we did… this is for the linux version (wide screen)… https://g4933.gitlab.io/wideopen/
This is great. Our Hyundai i30 2017 runs android on its infotainment unit. There’s used to be a hidden menu in the settings that would take you to a list of all apps and with some browser trickery you could install apks from a flash drive. The hidden menu shortcut has been removed in an update at the dealer’s but I installed a shortcut app that allows you to open the menu using a long press on one of the buttons and the app has persisted through the update.
but can it run doom?
My takeaway: the files for the update are being encrypted using the first example key in the RSA gudebook. Cue a photo of Jackie Chan.
Sometimes you wonder if this is a wink and a nod
The Linux gen5w has been hacked for quite a loooooong time already though
The only head units that seem impossible to reverse are the Honda’s it’s Android based but no one seems to be able to hack them 🤣
Nice hack 🥰 Love it 🥰