Numerical keypads are common entry devices for everything from home security systems to phones and more. Unfortunately, a great deal of them are difficult to use if you’re visually impaired. This high-contrast Braille keypad aims to solve those issues with simple design choices.
The keypad was developed as a school project by students [Nicholas Nguyen] and [Daniel Wang]. It uses a regular layout, with 1 at the top left and 9 at the bottom right. The keypad itself is 3D printed with large buttons for easier use. Each button has its numeral inlaid on the face which allows it to be easily filled in with paint for high-contrast readability.
The real neat feature, though, is that each individual button features its relevant number in Braille. The pips are directly 3D printed into the shape of each button. For those that familiar with the tactile writing system, this makes the keypad much easier to use. It obviates the need to guess at the keypad’s orientation, and we’re honestly surprised we don’t see this on more devices out in the wild.
We’ve featured a variety of neat Braille hacks over the years, including this neat tactile display.
Continue reading “Students 3D Print Low Cost Braille Keypad”




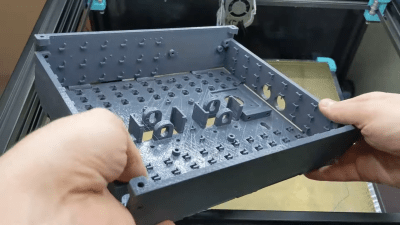 Sloxel’s job is to vet visitors to [Alan’s] house, before inviting them to knock on the door or to leave their details and go away. There’s still plenty of work to do on that functionality, which [Alan] plans to implement using ChatGPT. In the meantime, though, he’s been working hard on the hardware platform that will power Sloxel. A Raspberry Pi 3B+ is charged with running the show, including talking to the ChatGPT API and handling Sloxel’s motion along a linear rail with a number of stepper motors.
Sloxel’s job is to vet visitors to [Alan’s] house, before inviting them to knock on the door or to leave their details and go away. There’s still plenty of work to do on that functionality, which [Alan] plans to implement using ChatGPT. In the meantime, though, he’s been working hard on the hardware platform that will power Sloxel. A Raspberry Pi 3B+ is charged with running the show, including talking to the ChatGPT API and handling Sloxel’s motion along a linear rail with a number of stepper motors.








