Last time, we talked about the surface-level details of Ethernet. They are fundamental to know for Ethernet hacking, but they’re also easy to pick up from bits and pieces online, or just from wiring up a few computers in your home network. Now, there’s also a bunch of equipment and standards that you will want to use with Ethernet – easy to find whether used or new, and typically as easy to work with. Let’s give you a few beacons!
Routers And Switches
Whenever you see a box with a few Ethernet ports, it’s either referred to as a router, or a switch, sometimes people will even use the word “hub”! Fortunately, it’s simpler than it may seem. A router is a smart device, typically with an OS, that ties two or more networks together – routing packers from one network to another, and typically taking care of things like handing out local IP addresses via DHCP. A switch merely helps Ethernet devices exchange packets between each other on the same level – it’s typically nowhere near as smart as a router gets. Oftentimes, a home router will contain a switch inside, so that you can plug in multiple of your home devices at once. That’s the main difference – a switch merely transmits packets between Ethernet-connected devices, while a router is a small computer taking care of packet forwarding between networks and possibly including an Ethernet switch on the side.
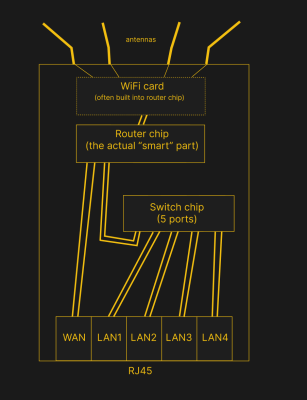
It’s easy to find a router for hacking purposes, and we’ve been reprogramming them for two decades now. Often, they run Linux, and if they don’t, they can be coerced. Inside a common router, you get a Linux device, typically with barely any CPU power, RAM or ROM, but you can run fun stuff alright – a file share, some control software for your robot, or maybe a tiny home automation suite.
Taking the other tack, it’s easy to build something that fulfills the functions of a router – take a low-power PC, put a Linux OS onto it, set up a DHCP server and packet forwarding script of some sort, and add a switch for anything you might want to network up. If you need a WiFi access point, you can plug in a network card and set up something like hostapd. Or don’t – there are also WiFi APs available: a single-purpose device with a single Ethernet port, that tend to be wonderful at what they do, unless you go for the cheapest option possible.
There’s plenty of hacking potential in Ethernet routers and switches alike. For routers, there’s the obvious OS hacking, but even that’s not all. For instance, you can use a multi-port router as a switch in a pinch, as long as you disable the “smart” features like DHCP server and don’t plug anything into the WAN port. Once, when I needed a gigabit Ethernet switch and only had a cheap router with gigabit ports, I did just that. Understand these devices, and you will be able to reuse them in a variety of ways. Speaking of reuse – if you have an outdated router, take one apart, and you can get RJ45 (8P8C) jacks, Ethernet transformers (aka magnetics), switch-mode PSU circuits you can reuse, and some nice WiFi antennas in case you need to boost your ESP32’s coverage in a pinch.
As for switches, here are a few hacks that turn regular switches into “managed” switches that add extra quality of life features like VLANs, port mirroring, or security features. We’ve even covered a hack that lets you tap into the Linux OS powering a particularly fancy switch! Want to build your own Ethernet switch? We’ve previously shown you products from a company building hacker-oriented commercial embeddable Ethernet switches, that I’m sure you could easily learn from and put your own spin on. The company involved started out as “open-source” but took down the hardware design file repo at some point after we started covering their products; thankfully, there are forks still available. Plus, switch schematics can be pretty easy to find, and teardowns even more so!
Have you heard about Ethernet hubs? “Hub” is generally a synonym for “switch” these days, but back in the 10 Mbps days, it used to be a different device – a passive way to tie three Ethernet devices into a network using resistors, diodes, or transistors. Every packet is sent to every device, of course, and it only works for low speeds because it makes the connection half-duplex, and the signal strength is weakened, but the upside is that it’s extremely simple. I’ve never encountered a hub in real life, but if you’re wondering, I’ve found two designs, one using resistors (translated, original) and another using diodes. Both of these designs have three ports – if you’re ever in need of a low-speed Ethernet network, this should do in a pinch.
Power over Ethernet
Speaking of things that you can build yourself, powering your devices is undoubtedly a priority. Let’s talk about Power over Ethernet, where you will find it, how you can build it on your own, and when you might want to reconsider doing that.

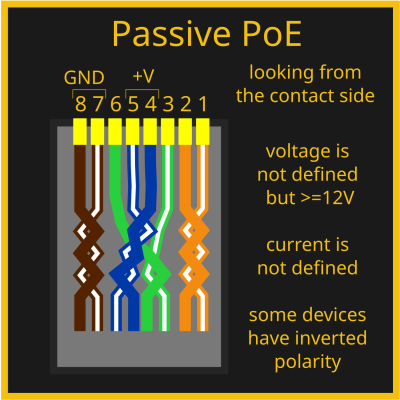
There’s also the PoE “standard” where you use two pairs for 100 Mbps and then just put a high-ish DC voltage on two of the remaining pairs. It’s charitably referred to as “passive PoE”, and it is what you’re likely to encounter in cheap products. You’d better watch out to ensure that it doesn’t blow up your port – there’s no negotiation, and usual devices don’t take kindly to it. In addition to that, there are a few proprietary standards, like the Mikrotik Gigabit PoE.
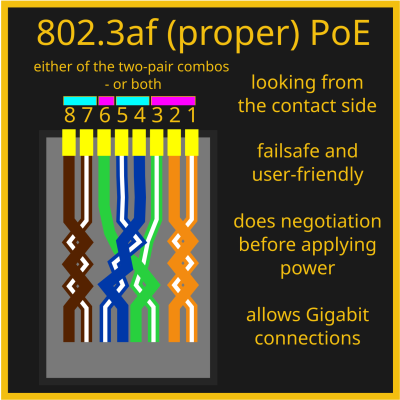
The 802.3af PoE standard works by superimposing a DC voltage onto the signal, using two possible pair combinations, known as Mode A and Mode B respectively. There’s also a higher power option, which uses all four pairs for higher power devices. Power is only applied to the pairs after PoE negotiation, and negotiation only happens after a compatible device is detected on the other end. 802.3af PoE tends to come with a pricetag, and that’s mostly because it has a fair bit more electronics involved, typically even including a small but hefty transformer.
If your device doesn’t come with PoE and you want to add it the proper way, there’s also modules you can buy online and add inline, 802.3af injectors and extractors. It might take a fair minute to find one, but you generally won’t go wrong using a 802.3af-compliant PoE module if you want to go the DIY route while sticking to foolproof PoE tech – they make a lot of sense if most of your network already supports 802.3af and it’s just a few devices that don’t. Oh, and of course, it’s possible to design your own. If you do that, you can even add support for both proper 802.3af and passive PoE!
Passive PoE, the straightforward version, has its spot under the sun and in our toolboxes too. Of course, you better be careful shoving passive PoE-powered cables into places – it can burn out a port on your laptop or Pi, if you’re not careful. Nevertheless, if you’re fine with 10/100Mbps, have control over the network, and just want to wire up a Raspberry Pi or two, passive PoE is a wonderful way to do it – the cheapest, the simplest, and the most flexible. One classic hacky way to make passive PoE work is simply cutting into Ethernet cables, but if you’ll be touching the cabling often, remember that this is breakage-prone. If you want to make a passive PoE circuit easy to maintain when your network inevitably needs some tweaking, you can also buy passive PoE injectors and receivers online – and they’ll be much, much cheaper too! So, you exchange user error protection for lower cost and greater hackability – sounds like exactly the kind of tradeoff a hacker should know about.
Here’s my own advice for passive PoE, having wired up a couple of small-scale networks with it. You should clearly mark passive PoE cables, because they’re meant to go through a PoE tap (“injector”) before you plug them into any device – a red sharpie, maybe a piece of red tape, but a sticker that says “do not touch if you don’t know what you’re doing” is the best option problem. This is the most important part with passive PoE, and you might be able to guess why I stress it. You might be tempted to add PoE by soldering onto the pads of an Ethernet jack on your device’s PCB, but do a multimeter test first – it might be a jack with integrated Ethernet transformer, or there might be resistors connected to the unused pairs.
Also, you have to choose your voltage with passive PoE, and you can’t just do 5 V. The voltage drop over meters of Ethernet cabling is going to halve this voltage immediately, with barely anything left unless you’re powering something really low power. Remember, active PoE uses 48 V for a good reason – as you increase voltage, you decrease current needed to carry the same amount of power. 12 V might be tempting, but 24 V is significantly more advantageous, as long as you don’t use cheap DC-DC modules – those will fail you, especially when powering a Raspberry Pi. Last but not least, if you are about to re-crimp cable carrying a passive PoE link, remember to disconnect the other end, unless you want to have sparks fly.
We’ve covered PoE quite a bit, and even hacks that add PoE to ESP32 using 802.3af modules, reuse the Raspberry Pi PoE header for single-cable wireup, or even transmit Ethernet over DC power instead. Now, for a change, let’s talk about the polar opposite – a way to do Ethernet that does not allow you to do any power transmission at all, which is Ethernet over fiber optics, and how you can get there.
Media Converters
If you’ve ever hacked a bit further than pure home applications of Ethernet, you’ll know there’s a way to put it onto fiber optic. Fiber is wonderful for even longer distance runs than Ethernet can achieve, it’s even more resillient too. Sometimes it lets you reuse an existing fiber connection – many a provider now prefers pulling fiber. A piece of hardware capable of converting Ethernet to fiber is called a “media converter,” and they’re not that hard to find online as separate pieces of equipment – especially given that many are discarded by small-scale ISPs as they upgrade their tech.

Now, unlike Ethernet, you can’t easily crimp fiber, you have to weld it with a special machine, and if you don’t have that machine, you might have to settle with buying pre-terminated fiber lengths. You also have to be seriously careful when bending fiber – it can’t withstand much abuse. However, if the upsides of fiber are tempting for you, what you can do is go find a media converter online, plug your Ethernet cable into it, and on the other port of it, or two ports, and bam, you get fiber Ethernet.
One unexpected use case for a hacker is total galvanic isolation – lightning-proofing your Ethernet links on the cheap. If you’ve ever wanted to add a surefire, guaranteed lightning protection to an Ethernet connection, converting it into a short run of fiber optic cable through two media converters is perhaps the best decision you can make! Fiber is also resilient to electromagnetically noisy environments.
At this point, you might be wondering – how exactly do you build new Ethernet devices? Whether it’s an ESP32, a DIY router, or an Ethernet-enabled stepper motor, worry not. Next time, we will go through the practical side of using Ethernet – Ethernet transformers, internals, and wireup, nuances like Bob Smith termination, magjack recommendations, PHYs and MACs, and how to bend the rules at the hardware level. For illustration and example circuit purposes, expect to see a fair few Ethernet-based hacks from all around the hacker world!
Featured image: “10base-T” by [gratuit]

















“Have you heard about Ethernet hubs? “Hub” is generally a synonym for “switch” these days, but back in the 10 Mbps days, it used to be a different device – a passive way to tie three Ethernet devices into a network using resistors, diodes, or transistors.”
No, hubs don’t have to be passive!
The hub/switch difference is generally that hubs don’t do *any* packet level inspection: they just receive the data on one port and retransmit it to all the other ones equally. If you have ports A, B, C, D, and A tries to send a packet to B, it *also* goes to C and D. Switches actually look at the MAC addresses coming from inbound packets and, well… switch the data from one port to another. They got called “switches” because for device-to-device communication, they’re the same as crossbar switches: if port A talks to port B, the data only goes between A and B, not any other port.
In fact in a lot of ways the conceptual difference between a “router” and a “switch” is that switches only look at the *MAC address* portion of the Ethernet frame, whereas routers look at the *IP address* portion of the frame (with the advent of “managed switches” this isn’t really true, but we’ve abused the heck out of what a “router” is nowadays anyway).
Duh, I forgot to point out the practical points: a hub necessarily shares the bandwidth between all of its ports. For most (all?) actual Ethernet hub devices you could buy, that made them fundamentally half-duplex with collision problems, since they were essentially all electrically connected (think of it like a wired-or, or I2C type situation). But if you were building a “network connector” device yourself (e.g. in an FPGA) there’s no reason you couldn’t put a receive packet buffer from each port and avoid collisions that way, still having a full-duplex connection but with shared bandwidth. From a device perspective once you’ve gone that far, adding a MAC cache and a crossbar is negligible, so I doubt any device actually did it.
Also worth point out is that you don’t even need to use CAT* type wiring. “Back in my day” we used coaxial cable for Ethernet (10base2 or “Thinnet”), with each device strung together in series using T connectors and terminating resistors at each end of the cable. There were also 10base5 networks, also called Thicknet, which you had to connect to via a vampire tap (a spike which went through the shielding to make contact to the core). These wiring schemes effectively functioned as hubs… half-duplex, all stations saw all frames, etc.
My first network setup was thin-net used to play Doom at my apartment.
Great hacker use case for cheap and simple hub is you can use it to sniff traffic between two other devices whereas to do the same with switch technology will require a more complex and expensive managed switch which supports span ports so you can send a copy of all packets from the devices of interest to a third port for you to examine. I still keep a 10mbit hub around for that purpose as unmanaged switches are useless for sniffing.
I keep an old small 100/10 Ethernet hub around just for this. I rarely use it, but when I’ve written and/or debugged close to the wire Ethernet stuff it’s been invaluable since I don’t have expensive equipment for that.
> The hub/switch difference is generally that hubs don’t do *any* packet level inspection: they just receive the data on one port and retransmit it to all the other ones equally.
Exactly – and this is why I still have a few hubs.
If I want to flash an openWRT compatible router the time window between switching on the device and being able to enter it’s “boot menu” can be very short. Too short for a switch to re-learn the MAC address and/or a NIC driver to properly configure itself.
With a hub the NIC just stays connected and there’s no MAC addresses to learn – it just forwards the packets.
And I’m pretty sure ~25 years ago a friend of mine had an 8 port 100Mbit hub. Caused a problem on LAN-party where one computer had a 10MBit-only NIC.
I had a weird hybrid 10/100 Mbit/S twisted pair hub. The ports would auto negotiate and would be connected to virtual shared bus in the device’s ASIC. There were separate 10 Mbit and 100 Mbit buses to which ports would be connected, so all ports at given speed were operating half duplex and shared a common collision domain. There was an internal two port switch which gated layer-2 frames between the two buses, thus allowing fast snd slow devices to talk to each other.
Luckily switch fabric ASICs quickly became inexpensive and hybrid devices were around only briefly
Hubs are also old technology from when we still had small private network with no outside access like some offices, small business, or even home for LAN parties. They are largely extinct as they are obsolete. You won’t find a new gigabit hub anywhere. It’s either switch or router nowadays.
From an old magazine somewhere in the turn of the century: (pre-Y2K I believe)
A hub is like a 4-way intersection with stop signs
A switch is like a 4-way intersection with traffic light
A router is like a 4-way intersection with traffic light and police car
Gigabit’s fundamentally different than 10/100: building a “hub” would be monumentally dumb when you already need analog equalization/echo cancellation and a 6-7 bit ADC/DAC on each port already.
Like I said you could build the *equivalent* of one in an FPGA (and I have) but commercially it wouldn’t make sense considering the digital side is tremendously easier than the analog.
Actually a hub is more like a single lane freeway with mulitple on-ramps. You yield to oncoming cars that you sense. You merge onto the freeway if nothing is coming. If you detect a collision with another car has occurred, you restart at your onramp once again. If you fail to merge onto a busy after a certain amount of time or number of attempts, you return home and park the car.
oh the fun of collision domain back in the day. Fun times back then, we also had to learn IPX networking for certification.
If a company has a hub still (probably in a remote dungeon like area if they still have a hub ) IMHO run.
There is also the opposite of power over Ethernet – Powerline Networking! Which turns your home’s power backbone into a media for shared Ethernet. It is now much less popular now due to popularity of wireless. But it has hacking potential.
Can someone give me a tip for passive PoE? If I want to run a security camera that runs on 5V 1A. I want to supply the power over a 50 foot Ethernet cable. What kind of power should I feed from the source?
Passive POE without voltage regulation on the end is a bad idea. 5v will drop quite a bit with any current. Use real POE with something like this on the end:
https://www.amazon.com/DSLRKIT-Splitter-Ethernet-802-3af-5-5×2-1mm/dp/B07ZH5V89T
Just to illustrate *how* bad, CAT5 is typically 24 AWG, so 25 mohm/ft (50 mohm/ft round trip w/power & gnd), so an amp across 50 feet is 2.5V. So yeah, a ton. Sure, you could do it, but totally not worth the effort.
How about 12v over passive POE with 5v regulator in the camera?
Two things. First, I was surprised no one mentioned the ease of packet sniffing with hubs or, given the resistor/diode comments, the ability to build passive taps.
Second, unless my memory is failing me, when you are looking at the contacts of an RJ45, i.e. tab facing away from you, the leftmost pin is #1. Not #8 as shown in the diagrams.
Yes, PoE-splitter (counter part of PoE-injector) would be better for _”Only one cable for 5V 1A Internet Protocol Camera”_ challenge.
You can get generic injectors if you are running just 100 megabit or 10 megabit. They will use the blue & brown pairs to carry voltage (typically). For gigabit, you would need center-tapped magnetics on each end and are approaching the point where an active PoE converter makes more sense.
I’d start at 24V! 48V is also pretty damn viable. At this point, I’d also consider proper PoE, the injector&extractor for that wouldn’t cost that much more compared to a DIY solution for this range, you’d likely get things regulated properly for you, and you avoid the hazards of having an Ethernet cable with 48V constantly applied to it.
On the camera end I would put a stepdown converter to 5v and on the the power supply end I would use a 15-24v power supply.
Most stepdown converters can convert down from about 30v and the higher voltage the less Amps need to go down the cable and heat it up.
If it wasn’t totally obvious: Supply as much voltage as you can, aiming for 24-48V. On the receiving end, a DC-DC regulator is essential. It should be able to input whatever voltage you’re supplying, and output 5V (at the desired current).
Optical links are also good for long runs near power (reduce inductive coupling), or runs in flammable/explosive areas.
I’ve seen optical links in metal conduit run above ground (cheap to deploy) between building, where someone lit a massive Halloween bonfire (~30 years ago) over the steel conduit which was hot enough to cause the link to fail. So yes I agree that optical is great, but bury and make sure that all documentation is updated that the exact location depth is known. That it will not accidentally be dug up and broken by a digger or bulldozer at some later date.
If you’re ever going backpacking, bring a small strand of fiber with you. If you ever get lost or need help, bury it a few inches in the ground and you can rest assured that in a few hours, a ditch witch will be there in a few hours to cut it.
I remember when we have 6 PC but only 5 ports on switch. Just cut open the cable, paralel the Ethernet cable jack to next pc. It works!
The difference between switches and hubs can be better understood when you go back in time and understand what a bridge was for. When all devices were on one piece of wire (old style ethernet) and two or more systems tried to talk at the same time there would be a collision. The more devices you added, the worse it got.
A bridge was a device that you used to break the network in two or more parts, it learned at layer 2 which MAC addresses were on each side of the bridge. If it heard a conversation that needed to go across the bridge then it let it across, otherwise conversations between devices on one side were not heard on the other side. This cut down the collisions.
This concept was expanded on to create the switch which essentially bridges every connection. The switch learns the MACs on each port and keeps a table. It then switches traffic so that traffic between the ports is not heard on other ports. If the switch does not know where the destination MAC is it floods all the ports until it finds the responding MAC.