The 2015 Midwest RepRap Festival, a.k.a. the MRRF (pronounced murf) was just announced a few hours ago. It will be held in beautiful Goshen, Indiana. Yes, that’s in the middle of nowhere and you’ll learn to dodge Amish buggies when driving around Goshen, but surprisingly there were 1000 people when we attended last year. We’ll be there again.
A few activists in St. Petersburg flushed GPS trackers down the toilet. These trackers were equipped with radios that would send out their position, and surprise, surprise, they ended up in the ocean.
[Stacy] has been tinkering around with Unity2D and decided to make a DDR-style game. She needed a DDR mat, and force sensitive resistors are expensive. What did she end up using? Velostat, conductive thread, and alligator clips.
You know the Espruino, the little microcontroller board that’s basically JavaScript on a USB stick? Yeah, that’s cool. Now you can do remote access through a telnet server letting you write and debug code over the net.
The Open Source RC is a beautiful RC transmitter with buttons and switches everywhere, a real display, and force feedback sticks. It was a Hackaday Prize entry, and has had a few crowdfunding campaigns. Now its hit Indiegogo again.
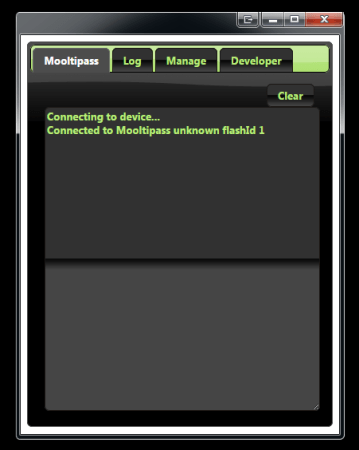
Speaking of crowdfunding campaigns, The Mooltipass, the designed-on-Hackaday offline password keeper, only has a little less than two weeks until its crowdfunding campaign ends. [Mathieu] and the rest of the team are about two-thirds there, with a little more than half of the campaign already over.