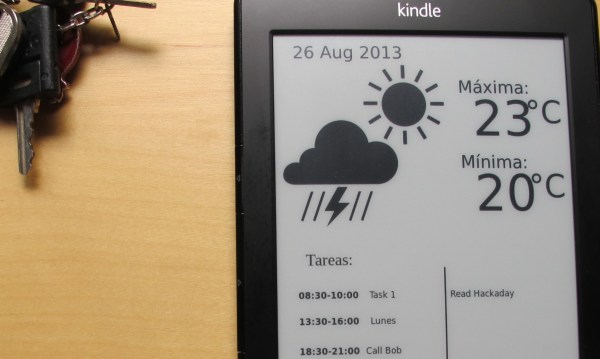
What if your Kindle displayed useful information as the “screensaver”? Now it can thanks to this extension of the Kindle weather display hack we covered a year ago. [Pablo Jiménez Mateo] figured out how to display time, date, weather, and tasks as his Kindle wallpaper while retaining the original functionality of the device as an ePaper reader.
The hack isn’t strictly standalone. Like the Kindle weather station hack on which it is based, you need a computer to act as the server. We see this as a good thing. The server generates a vector graphic which is used as the Kindle screensaver. This process of scraping and packaging the data is just too much for the computing power of the Kindle alone.
Now that [Pablo] got this working without disrupting the normal function of the device, you can remix the hack with your own information sources by working with the server-side code. For those that aren’t familiar with the Linux commands needed to get the Kindle ready, don’t worry. This is reasonably non-invasive. You do need to Jailbreak your device. But once you do, the steps used simply load a small script to grab the images.