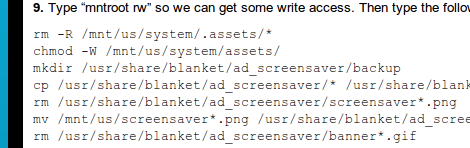
[Kubbur87] put together a guide to replacing the Non-touch Kindle 4 screensavers with your own images. We’ve already seen a way to remove the Special Offers banners from the newest version of Kindle Hardware, this hack lets you use your own 600×800 Portable Network Graphics (.png) file instead of the images pushed to the device by Amazon.
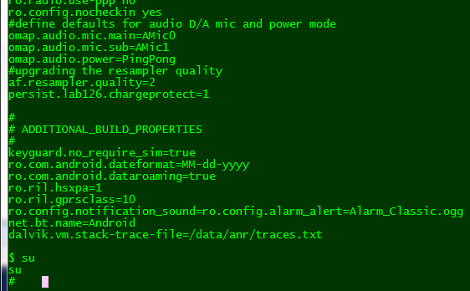
Frankly, we’re shocked at how easy this hack is. [Kubbur87] puts the device into developer mode, enables SSH, and then goes to work on the Linux shell within. It seems the only line of protection is the root password which he somehow acquired.
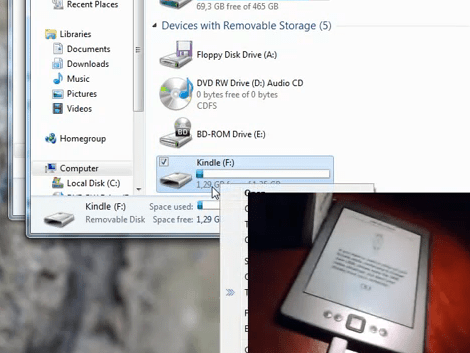
After the break you’ll find his videos which show how to enable developer mode and how to perform this hack. By putting a file named “ENABLE_DIAGS” with no extension on the device when it is recognized as a USB storage device you’ll gain access to the diagnostic menu system. From there it’s just a matter of cruising that menu to get SSH access. Like we said, you’ll need the root password, that that’s as easy as naming your favorite video game character from the 1980’s.
Continue reading “Custom Screensaver On The Non-touch Kindle 4”