It sometimes comes as a shock when you look at a piece of hardware that you maybe bought new and still consider to be rather high-tech, and realise that it was made before someone in their mid-twenties was born. It’s the moment from that Waylon Jennings lyric, about looking in the mirror in total surprise, hair on your shoulders and age in your eyes. Yes, those people in their mid-twenties have never even heard of Waylon Jennings.
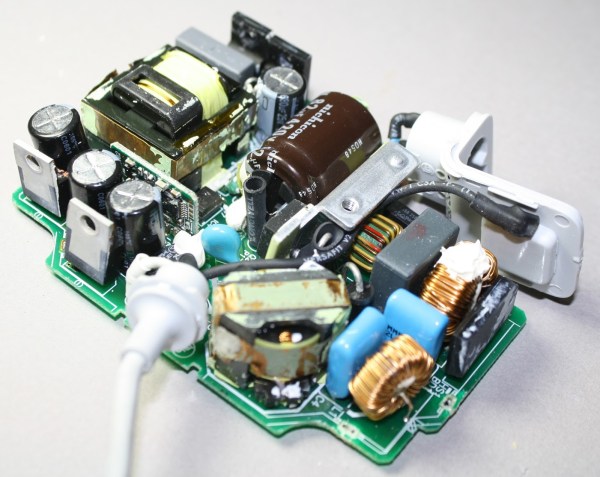
[Steve] at Big Mess o’Wires has a Mac IIsi from the early 1990s that wouldn’t power up. He’d already had the life-expired electrolytic capacitors replaced on the mainboard, so the chief suspect was the power supply. That miracle of technology was now pushing past a quarter century, and showing its age. In case anyone is tempted to say they don’t make ’em like they used to, [Steve]’s PSU should dispel the myth.
It’s easy as an electronic engineer writing this piece to think: So? Just open the lid, pop out the old ones and drop in the new, job done! But it’s also easy to forget that not everyone has the same experiences and opening up a mains PSU is something to approach with some trepidation if you’re not used to working with line power. [Steve] was new to mains PSUs and considered sending it to someone else, but decided he *should* be able to do it so set to work.
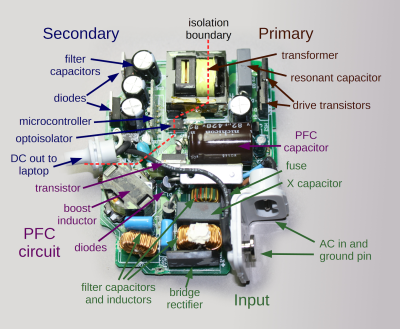
The Apple PSU is a switch-mode design. Ubiquitous today but still a higher-cost item in those days as you’ll know if you owned an earlier Commodore Amiga whose great big PSU box looked the same as but weighed ten times as much as its later siblings. In simple terms, the mains voltage is rectified to a high-voltage DC, chopped at a high frequency and sent through a small and lightweight ferrite-cored transformer to create the lower voltages. This means it has quite a few electrolytic capacitors, and some of them are significantly stressed with heat and voltage.
Forum posts on the same PSU identified three candidates for replacement – the high voltage smoothing capacitor and a couple of SMD capacitors on the PWM control board. We’d be tempted to say replace the lot while you have it open, but [Steve] set to work on these three. The smoothing cap was taken out with a vacuum desoldering gun, but he had some problems with the SMD caps. Using a hot air gun to remove them he managed to dislodge some of the other SMD components, resulting in the need for a significant cleanup and rework. We’d suggest next time forgoing the air gun and using a fine tip iron to melt each terminal in turn, the cap only has two and should be capable of being tipped up with a pair of pliers to separate each one.
So at the end of it all, he had a working Mac with a PSU that should be good for another twenty years. And he gained the confidence to recap mains power supplies.
If you are tempted to look inside a mains power supply you should not necessarily be put off by the fact it handles mains voltage as long as you treat it with respect. Don’t power it up while you have it open unless it is through an isolation transformer, and remember at all times that it can generate lethal voltages so be very careful and don’t touch it in any way while it is powered up. If in doubt, just don’t power it up at all while open. If you are concerned about high voltages remaining in capacitors when it is turned off, simply measure those voltages with your multimeter. If any remain, discharge them through a suitable resistor until you can no longer measure them. There is a lot for the curious hacker to learn within a switch mode PSU, why should the electronic engineers have all the fun!
This isn’t the first recapping story we’ve covered, and it will no doubt not be the last. Browse our recapping tag for more.