Most people tend to enjoy a certain modicum of privacy. Aside from the data we all share willingly on the web in the form of forum posts, Twitter activity, etc., people generally like keeping to themselves.
What would you think then, if you found out your iPhone (or any iDevice with 3G) was tracking and logging your every movement?
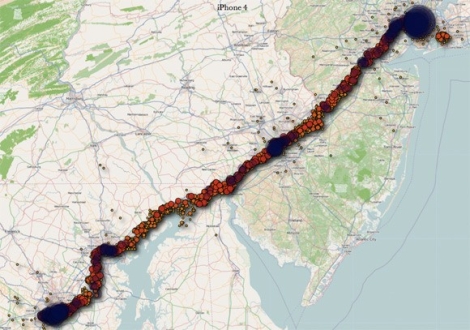
That’s exactly what two researchers from the UK are claiming. They state that the phone is constantly logging your location using cell towers, placing the information into a timestamped database. That database is not encrypted, and is copied to your computer each time you sync with iTunes. Additionally, the database is copied back to your new phone should you ever replace your handset.
We understand that many iPhone apps use location awareness to enhance the user experience, and law enforcement officials should be able to pull data from your phone if necessary – we’re totally cool with that. However, when everywhere you have been is secretly logged in plaintext without any sort of notification, we get a bit wary. At the very least, Apple should consider encrypting the file.
While this data is not quite as sensitive as say your Social Security number or bank passwords, it is dangerous in the wrong hands just the same. Even a moderately skilled thief, upon finding or swiping an iPhone, could easily dump the contents and have a robust dataset showing where you live and when you leave – all the makings of a perfect home invasion.
Continue reading to see a fairly long video of the two researchers discussing their findings.
[Image courtesy of Engadget]
Continue reading “IPhone Watching Every Breath You Take, Every Move You Make” →