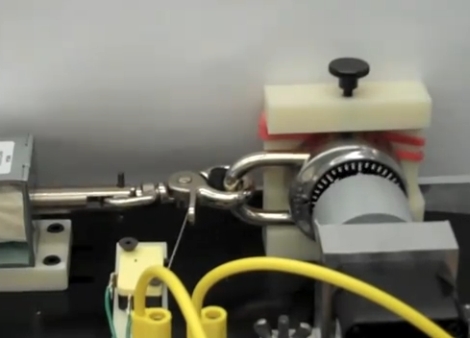
Hackers at the “RaumZeitLabor” hackerspace in Mannheim Germany have noticed that the locking mechanism on the thinkpad mini dock is extremely easy to circumvent. Sold as an additional layer of security, the mechanism itself is not really secured in any way. The button that actuates it is locked by a key, but the latch isn’t secured and can be accessed via a vent on the side. They are using a lockpicking tool in the video, but they say that even a long paperclip would suffice.
We know that no security device is perfect, and if someone really really wants it, they’ll take it, but this seems a bit too easy. Maybe the next version will have a little plastic wall protecting the latch from being actuated manually. Hopefully if security is your main concern you are using something a little more robust that a dock-lock.
[via the RaumZeitLabor hackerspace (google translated)]