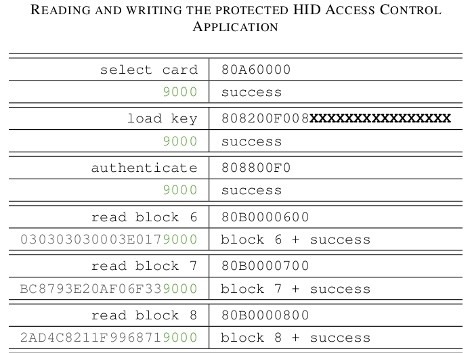
iClass is a popular format of RFID enabled access cards. These are issued to company employees to grant them access to parts of a building via a card reader at each security door. We’ve known for a long time that these access systems are rather weak when it comes to security. But now you can find out just how weak they are and how the security can be cracked. [Milosch Meriac] delved deep into the security protocol for HID iClass devices and has laid out the details in a white paper.
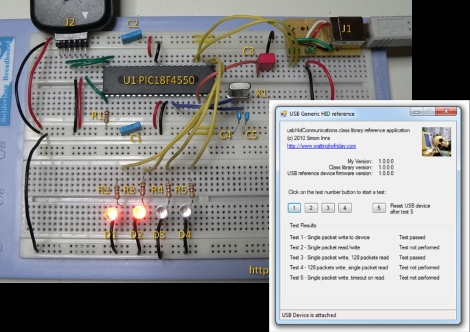
The most invasive part of the process was breaking the copy protection on PIC 18F family of chips in order to read out the firmware that controls card readers. This was done with a USB to serial cable and software that bit-bangs its own implementation of the ICSP protocol. After erasing and attacking several chips (one data block at a time) the original code was read off and patched together. Check out [Milosch’s] talk at 27C3 embedded after the break, and get the code for the ICSP bit banging attacks from the white paper (PDF).