Internet-connected sex toys are a great way to surprise your partner from work (even the home office) or for spicing up long-distance relationships. For some extra excitement, they also add that thrill of potentially having all your very sensitive private data exposed to the public — but hey, it’s not our place to kink-shame. However, their vulnerability issues are indeed common enough to make them regular guests in security conferences, so what better way to fight fire with fire than simply inviting the whole of Twitter in on your ride? Well, [Space Buck] built just the right device for that: the Double-Oh Battery, an open source LiPo-cell-powered ESP32 board in AA battery form factor as drop-in replacement to control a device’s supply voltage via WiFi.
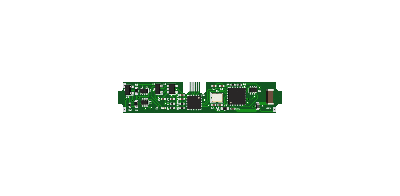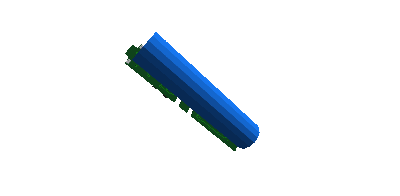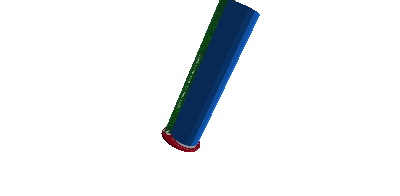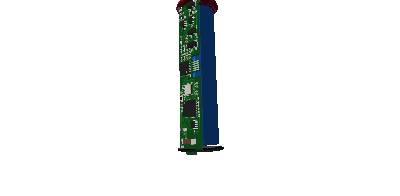
In their simplest and cheapest form, vibrating toys are nothing more than a battery-powered motor with an on-off switch, and even the more sophisticated ones with different intensity levels and patterns are usually limited to the same ten or so varieties that may eventually leave something to be desired. To improve on that without actually taking the devices apart, [Space Buck] initially built the Slot-in Manipulator of Output Levels, a tiny board that squeezed directly onto the battery to have a pre-programmed pattern enabling and disabling the supply voltage — or have it turned into an alarm clock. But understandably, re-programming patterns can get annoying in the long run, so adding WiFi and a web server seemed the logical next step. Of course, more functionality requires more space, so to keep the AA battery form factor, the Double-Oh Battery’s PCB piggybacks now on a smaller 10440 LiPo cell.
But then, where’s the point of having a WiFi-enabled vibrator with a web server — that also happens to serve a guestbook — if you don’t open it up to the internet? So in some daring experiments, [Space Buck] showcased the project’s potential by hooking it up to his Twitter account and have the announcement tweet’s likes and retweets take over the control, adding a welcoming element of surprise, no doubt. Taking this further towards Instagram for example might be a nice vanity reward-system improvement as well, or otherwise make a great gift to send a message to all those attention-seeking people in your circle.
All fun aside, it’s an interesting project to remote control a device’s power supply, even though its application area might be rather limited due to the whole battery nature, but the usual Sonoff switches may seem a bit unfitting here. If this sparked your interest in lithium-based batteries, check out [Lewin Day]’s beginner guide and [Bob Baddeley]’s deeper dive into their chemistry.