In a move that would induce ire in Lord Helmet, [Kedar Nimbalkar] has recreated Instructables user spacehun’s version of WiFi jammer that comes with a handful of features certain to frustrate whomever has provoked its wrath.
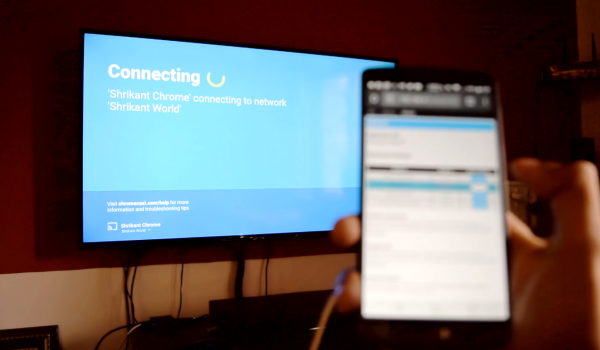
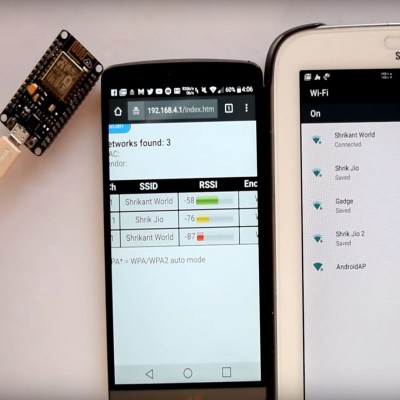 The jammer is an ESP8266 development board — running some additional custom code — accessed and controlled by a cell phone. From the interface, [Nimbalkar] is able to target a WiFi network and boot all the devices off the network by de-authenticating them. Another method is to flood the airspace with bogus SSIDs to make connecting to a valid network a drawn-out affair.
The jammer is an ESP8266 development board — running some additional custom code — accessed and controlled by a cell phone. From the interface, [Nimbalkar] is able to target a WiFi network and boot all the devices off the network by de-authenticating them. Another method is to flood the airspace with bogus SSIDs to make connecting to a valid network a drawn-out affair.
This kind of signal interruption is almost certainly illegal where you live. It does no permanent damage, but once again raises the existing deauth exploit and SSID loophole. [Nimbalkar]’s purpose in recreating this was for educational purposes and to highlight weaknesses in 802.11 WiFi protocols. The 802.11w standard should alleviate some of our fake deauth woes by using protected frames. Once the device authenticates on a network it will be able to detect fake deauth packets.
We featured a more targeted version of this hack that can be done using a PC — even targeting itself! And more recently there was a version that can target specific devices by jumping on the ACK.