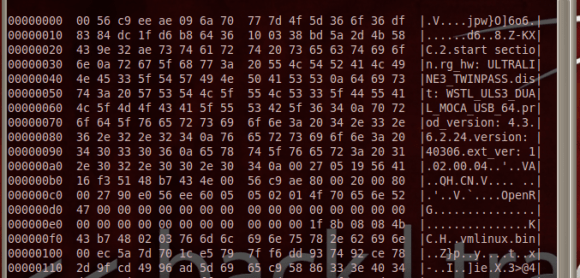
[Leland Flynn] did a great job of picking apart the firmware image for a Westell 9100EM FiOS router. Unfortunately he didn’t actually find the information he was looking for. But he’s not quite done poking around yet either. If you have never tried to make sense of an embedded Linux firmware image this serves as a great beginner’s example of how it’s done.
He was turned on to the project after port scanning his external IP and finding a random login prompt which he certainly didn’t set up. Some searching led him to believe this is some kind of back door for Verizon to push automatic firmware updates to his router. He figured why not see if he could yank the credentials and poke around inside of the machine?
He started by downloading the latest firmware upgrade. Running ‘hexdump’ and ‘strings’ gives him confirmation that the image is based on Linux. He’s then able to pick apart the package, getting at just the filesystem portion. His persistence takes him through extracting and decompressing three different filesystems. Even though he now has access to all of those files, broken symlinks meant a dead-end on his login search.











