
Against all previous indications-including being called The Last HOPE-the conference will not only be returning in 2010, it will be at the Hotel Pennsylvania. We’re looking forward to The Next HOPE, which will probably followed by The Last HYPE, which in turn will be followed by: We’re Super Serious This Is The Last HOPE.
hope38 Articles
HOPE 2008: Community Fabrication

Today at The Last HOPE, [Far McKon] from Philadelphia’s Hacktory presented on community fabrication. Over the last few years we’ve seen a lot of different accessible rapid prototyping machines created. There’s the RepRap, a fabrication machine that has achieved self replication; our friends at Metalab have gotten their own version of the machine running too. The Hacktory has recently acquired a Fab@home machine. Fab@home hopes to make manufacturing using multiple materials accessible to home users. Multiple materials means people have constructed objects that vary from embedded circuits to hors d’oeuvres. We can’t talk about edible prototyping without bringing up the CandyFab machine, which fuses sugar. The Hacktory has enjoyed their machine so far, but have found the learning curve fairly difficult. While it’s great to see the cost of rapid prototyping dropping, we’ll be much happier when the ease of use improves.
HOPE 2008: Wikiscanner 2.0

[Virgil] presented the next version of Wikiscanner at The Last HOPE today. To build the original Wikiscanner, he scanned the monthly database dump of anonymous edits and compared that against a purchased list of known company IP addresses. The 34.5 million edits account for nearly 21% of all edits. The idea was to unearth businesses and groups white washing critical pages. This only handles anonymous edits though. Users could log in to avoid having their IP reversed.
In the new version, [Virgil]’s team developed a Poor Man’s CheckUser. If you spend too much time editing a talk page, your session could end and when you hit save it attaches your IP. Most regular users will then log in and remove their IP. They found 13,000 username/IP address pairs by searching for IPs being removed and replaced with usernames. These are some of the most active users. Using this list, they could potentially uncover sockpuppets or potential collusion by top editors.
HOPE 2008: Cold Boot Attack Tools Released
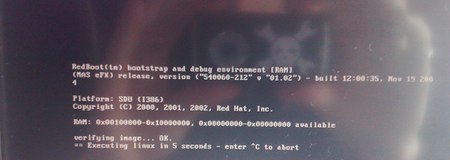
The team from Princeton has released their cold boot attack tools at The Last HOPE. Earlier this year they showed how to recover crypto keys from the memory of a machine that had been powered off. Now they’ve provided the tools necessary to acquire and play around with your own memory dumps. The bios_memimage tool is written in C and uses PXE to boot the machine and copy the memory. The package also has a disk boot dumper with instructions for how to run it on an iPod. There’s also efi_memimage which implements the BSD TCP/IP stack in EFI, but it can be problematic. aeskeyfind can recover 128 and 256bit AES keys from the memory dumps and rsakeyfind does the same for RSA. They’ve also provided aesfix to correct up to 15% of a key. In testing, they only ever saw 0.1% error in there memory dumps and 0.01% if they cooled the chips first.
Continue reading “HOPE 2008: Cold Boot Attack Tools Released”
HOPE 2008: The Impossibility Of Hardware Obfuscation

The Last HOPE is off and running in NYC. [Karsten Nohl] started the day by presenting The (Im)possibility of Hardware Obfuscation. [Karsten] is well versed in this subject having worked on a team that the broke the MiFare crypto1 RFID chip. The algorithm used is proprietary so part of their investigation was looking directly at the hardware. As [bunnie] mentioned in his Toorcon silicon hacking talk, silicon is hard to design even before considering security, it must obey the laws of physics (everything the hardware does has to be physically built), and in the manufacturing process the chip is reverse engineered to verify it. All of these elements make it very interesting for hackers. For the MiFare crack, they shaved off layers of silicon and photographed them. Using Matlab they visually identified the various gates and looked for crypto like parts. If you’re interested in what these logic cells look like, [Karsten] has assembled The Silicon Zoo. The Zoo has pictures of standard cells like inverters, buffers, latches, flip-flops, etc. Have a look at [Chris Tarnovsky]’s work to learn about how he processes smart cards or [nico]’s guide to exposing standard chips we covered earlier in the week.
Music And Visual Arts At The Last HOPE

[Peter Kirn] from Create Digital Music has an article up highlighting many of the great music and visual performance pieces planned for The Last HOPE on Friday night. If you are around New York and not accustomed to hacking conferences, this could be a great excuse to go check it out. Here are some of our favorite projects.
Toool Picksets At The Last HOPE

Speaking of laser engraving, the blackbag blog announced that Toool has designed 2 unique picksets for The Last HOPE this year. First is the credit card sized snap-off set seen above. They have named this one The Last HOPE emergency pickset. The other pickset is a new version of the ‘double sided pick’ series. This set consists of picks with the same tool on either end, but they are sized differently. This set will contain 8 picks with promised improvements. If you are interested in more complex picks, check out the centipede.










