Despite the repeated warnings of system administrators, IT personnel, and anyone moderately aware of operational security, there are still quite a few people who will gladly plug a mysterious flash drive into their computers to see what’s on it. Devices which take advantage of this well-known behavioral vulnerability have a long history, the most famous of which is Hak5’s USB Rubber Ducky. That emulates a USB input device to rapidly execute attacker-defined commands on the target computer.
The main disadvantage of these keystroke injection attacks, from the attacker’s point of view, is that they’re not particularly subtle. It’s usually fairly obvious when something starts typing thousands of words per minute on your computer, and the victim’s next move is probably a call to IT. This is where [Krzysztof Witek]’s open-source Rubber Ducky clone has an advantage: it uses a signal detected by a SYN480R1 RF receiver to trigger the deployment of its payload. This does require the penetration tester who uses this to be on the site of the attack, but unlike with an always-on or timer-delayed Rubber Ducky, the attacker can trigger the payload when the victim is distracted or away from the computer.
This project is based around the ATmega16U2, and runs a firmware based on microdevt, a C framework for embedded development which [Krzysztof] also wrote. The project includes a custom compiler for a reduced form of Hak5’s payload programming language, so at least some of the available DuckyScript programs should be compatible with this. All of the project’s files are available on GitHub.
Perhaps due to the simplicity of the underlying concept, we’ve seen a few open source implementations of malicious input devices. One was even built into a USB cable.
keystroke injection3 Articles
Brute Forcing A Mobile’s PIN Over USB With A $3 Board
Mobile PINs are a lot like passwords in that there are a number of very common ones, and [Mobile Hacker] has a clever proof of concept that uses a tiny microcontroller development board to emulate a keyboard to test the 20 most common unlock PINs on an Android device.
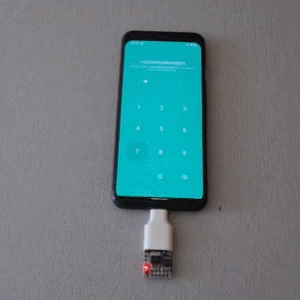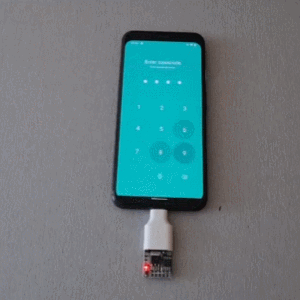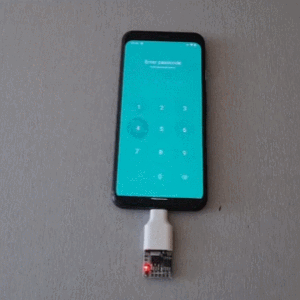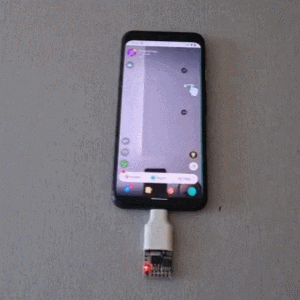
The project is based on research analyzing the security of 4- and 6-digit smartphone PINs which found some striking similarities between user-chosen unlock codes. While the research is a few years old, user behavior in terms of PIN choice has probably not changed much.
The hardware is not much more than a Digispark board, a small ATtiny85-based board with built-in USB connector, and an adapter. In fact, it has a lot in common with the DIY Rubber Ducky except for being focused on doing a single job.
Once connected to a mobile device, it performs a form of keystroke injection attack, automatically sending keyboard events to input the most common PINs with a delay between each attempt. Assuming the device accepts, trying all twenty codes takes about six minutes.
Disabling OTG connections for a device is one way to prevent this kind of attack, and not configuring a common PIN like ‘1111’ or ‘1234’ is even better. You can see the brute forcing in action in the video, embedded below.
Continue reading “Brute Forcing A Mobile’s PIN Over USB With A $3 Board”
DIY Rubber Ducky Is As Cheap As Its Namesake
The “Rubber Ducky” by Hak5 is a very powerful tool that lets the user perform rapid keystroke injection attacks, which is basically a fancy way of saying the device can type fast. Capable of entering text at over 1000 WPM, Mavis Beacon’s got nothing on this $45 gadget. Within just a few seconds of plugging it in, a properly programmed script can do all sorts of damage. Just think of all the havoc that can be caused by an attacker typing in commands on the local machine, and now image they are also the Flash.
 But unless you’re a professional pentester, $45 might be a bit more than you’re looking to spend. Luckily for the budget conscious hackers out there, [Tomas C] has posted a guide on using open source software to create a DIY version of Hak5’s tool for $3 a pop. At that cost, you don’t even have to bother recovering the things when you deploy them; just hold on tight to your balaclava and make a run for it.
But unless you’re a professional pentester, $45 might be a bit more than you’re looking to spend. Luckily for the budget conscious hackers out there, [Tomas C] has posted a guide on using open source software to create a DIY version of Hak5’s tool for $3 a pop. At that cost, you don’t even have to bother recovering the things when you deploy them; just hold on tight to your balaclava and make a run for it.
The hardware side of this hack is the Attiny85-based Digispark, clones of which can be had for as low as $1.50 USD depending on how long your willing to wait on the shipping from China. Even the official ones are only $8, though as of the time of this writing are not currently available. Encapsulating the thing in black shrink tubing prevents it from shorting out, and as an added bonus, gives it that legit hacker look. Of course, it wouldn’t be much of a hack if you could just buy one of these little guys and install the Rubber Ducky firmware on it.
In an effort to make it easier to use, the official Rubber Ducky runs scripts written in a BASIC-like scripting language. [Tomas C] used a tool called duck2spark by [Marcus Mengs], which lets you take a Rubber Ducky script (which have been released by Hak5 as open source) and compile it into a binary for flashing to the Digispark.
Not quite as convenient as just copying the script to the original Ducky’s microSD card, but what do you want for less than 1/10th the original’s price? Like we’ve seen in previous DIY builds inspired by Hak5 products, the trade-off is often cost for ease of use.
[Thanks to Javier for the tip.]













