We all know that our activity on the Internet is not that hard to track. It just annoys some people more than others. If you are really hardcore, you’ll learn all the ins and outs of networking to help cover your tracks, but what if you don’t want to invest that kind of time? Maybe, as [TechRepublic] suggests, try Kodachi Linux.
You could, of course, start with your own live image. Then when you boot, you could take the following steps:
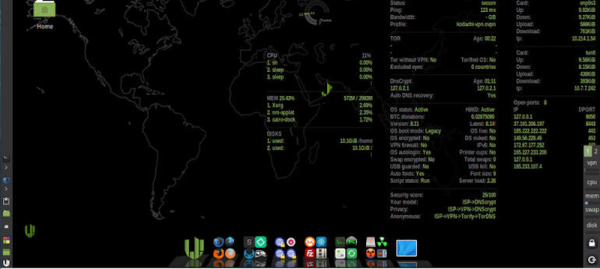
- Randomize your MAC Address
- Establish a TOR connection through a VPN
- Route all internet traffic through TOR and use DNS encryption
- Set up a scheduled task to scramble your MAC address periodically
But that’s what Kodachi does without any real effort on your part.
The distribution is based on Ubuntu, so all the familiar tools are there. There are also a few security and privacy tools included like KeePass, Tox, OnionShare, i2p, and more. The desktop shows a summary of secure network information
Do you need Kodachi? Probably not, if you are a Linux guru. Plus, most people aren’t doing anything that’s that interesting. But if you want to protect your privacy or you are up to something, give Kodachi a try. Then again, if you are that paranoid, maybe that’s just what THEY want you to do. Make your own decisions. You can also check out the video review from [eBuzz Central] below.
Looking for more conventional Linux? Why not Rocky Linux? If you just want a VPN, you can always just use ssh.
Continue reading “Linux For The Paranoid Does The Work For You”