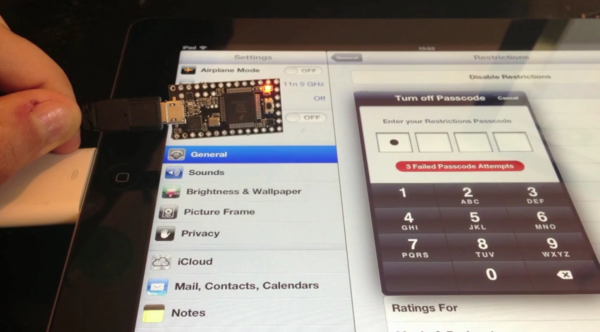
It’s quite common to have a timed lockout after entering several bad passwords. This simple form of security makes automated brute force attacks unfeasible by ballooning the time it would take to try every possible permutation. The lock screen on iOS devices like iPad and iPhone have this built in. Enter your code incorrectly several times and the system will make you wait 1, 5, 15, and 60 minutes between entries as you keep inputting the wrong code. But there is an exploit that gets around this. [Pierre Dandumont] is showing off his hardware-based iPad lock screen attack in the image above.
He was inspired to try this out after reading about some Mac EFI attacks using the Teensy 3. That approach used the microcontroller to spoof a keyboard to try every PIN combination possible. By using the camera kit for iPad [Pierre] was able to do the same. This technique lets you connect wired keyboards to the iPad, but apparently not the iPhone. A bluetooth keyboard can also be used. These external keyboards get around the timing lockout associated with the virtual lockscreen keyboard.
We’re of the opinion that this is indeed a security vulnerability. If you forget your passcode you can simply restore the device to remove it. That wipes all of your personal data which can then be loaded from an iTunes backup. Lockscreens are paramount if a device is stolen. They will give you the time you need to change any online credentials which might be remembered by the device.
Continue reading “IOS Keyboard Exploit Allows Brute Force IPad Lock Screen Attack”