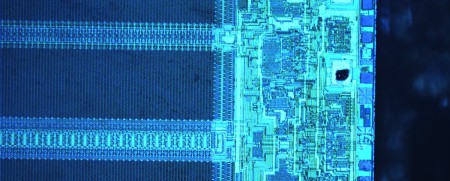
Wired recently posted an article and video detailing our friend [Chris Tarnovsky]’s process for hacking smart cards. In the video, [Chris] shows how he strips away physical components of the chips inside the smartcards using various gadgets and chemicals.
The first step is to remove the chip from its plastic frame. After soaking it in acid for about 10 minutes, the epoxy is removed and the chip is exposed. After that the outer layer is loosened by soaking the chip in two solutions of acetone, the second being the “clean” one. Then the chip is placed on a hotplate where a drop of fuming nitric acid is applied with a dropper; the chip is washed again in an ultrasonic cleaner, removing any residue left.
[Chris] then returns the chip to the card. He will apply nail polish to act as a masking material. He scratches a hole through the polish with a needle held by a micro positioner in the area of interest. The hole is treated with hydrofluoric acid and then etched in short intervals until the desired layer of silicon is exposed. At this point, the card is fully prepped.
Now by powering the chip with the needle resting on the bus, [Chris] can read the code on the chip by sending it various commands and watching how it reacts. To see more of [Chris]’s reverse engineering work, check out Flylogic Engineering’s Analytical Blog. It’s a enjoyable read even if you’re new to silicon hacking.