The 2013 IEEE International Conference of Robotics and Automation was held early in May. Here’s a video montage of several robots shown off at the event. Looks like it would have been a blast to attend, but at least you can draw some inspiration from such a wide range of examples.
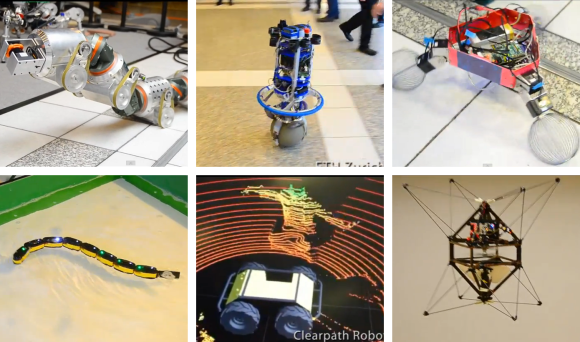
We grabbed a half-dozen screenshots that caught our eye. Moving from the top left in clockwise fashion we have a segmented worm bot that uses rollers for locomotion. There’s an interesting game of catch going on in the lobby with this sphere-footed self balancer. Who would have thought about using wire beaters as wheels? Probably the team that developed the tripod in the upper right. Just below there’s one of the many flying entries, a robot with what looks like a pair of propellers at its center. The rover in the middle is showing off the 3D topography map it creates to find its way. And finally, someone set up a pool of water for this snake to swim around in.













