Everyone wants to 3D print with metals, but it is a difficult task. You need high temperatures and metals with high thermal conductivity make the problem even worse. Researchers at Caltech have a way of printing tiny metal structures. The trick? They don’t print metals at all. Instead, they 3D print a hydrogel and then use it as a scaffold to form metallic structures. You can read the full paper, if you are interested in the details.
Hydrogels are insoluble in water and made from flexible polymer chains. If you’ve ever handled a soft contact lens, that’s a hydrogel. Like resin printing, UV light triggers chemical reactions in the hydrogels, causing them to harden in the desired pattern.
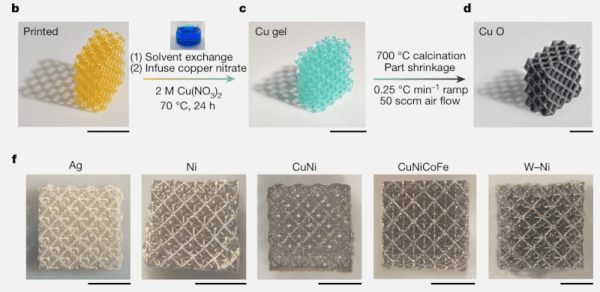
What about the metal? They infuse the hydrogel with a metallic salt dissolved in water. This saturates the hydrogel. Burning in a furnace causes the hydrogel to burn away but leaves the metal. The furnace also causes the structure to shrink, so this is a good method for very tiny pieces. The team has made prints with feature sizes around 40 microns.
By altering the metal salts, you can work with different metals or even mix different metals. The team has produced parts using copper, nickel, silver, and several alloys.
Printing small structures is a big research goal with many different approaches. We’ve even seen a tiny welder.