Friday saw what looked like the most dangerous ransomware infection to date. The infection known as WannaCry was closing down vital hospital IT systems across the UK canceling major operations and putting lives at risk.
Spread Halted?
It spread further around the world and almost became a global pandemic. Although machines are still encrypted demanding Bitcoin, one security blogger [MalwareTech] halted the ransomware by accident. As he was analyzing the code he noticed that the malware kept trying to connect to an unregistered domain name “iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com”. So he decided to register the domain to see if he could get some analytics or any information the worm was trying to send home. Instead much to his surprise, this halted the spread of the ransomware. Originally he thought this was some kind of kill switch but after further analysis, it became clear that this was a test hard-coded into the malware which was supposed to detect if it was running in a virtual machine. So by registering the domain name, the ransomware has stopped spreading as it thinks the internet is a giant virtual machine.
Why was the UK’s NHS Hit So Badly?
According to the [BBC] Information obtained by software firm Citrix under Freedom of Information laws in December suggest up to 90% of NHS trusts were still using Windows XP, However NHS Digital says it is a “much smaller number”. Microsoft has rolled out a free security update to Windows XP, Windows 8, and Windows Server 2003 “to protect their customers”. There was much warning about XP no longer receiving updates etc, the 2001 operating system just needs to die however so many programs especially embedded devices rely upon the fact that the OS running is Windows XP, This is a problem that needs sorted sooner rather than later. There is still obvious problems facing the NHS as all outpatients appointment’s have been canceled at London’s Barts Health NHS Trust which happens to be the largest in the country. However [Amber Rudd], Home Secretary, said 97% of NHS trusts were “working as normal” and there was no evidence patient data was affected. Let’s just hope they update their systems and get back to fixing people as soon as they can.
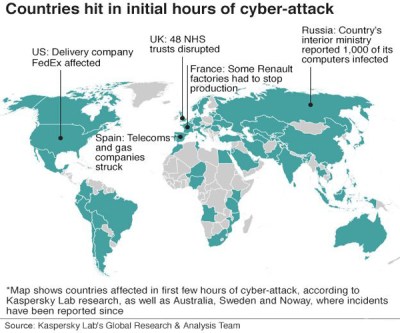
Where Else Was Hit?
There was quite a few other places hit as well as the UK’s NHS including The Sunderland Nissan Plant also in the UK, Spanish telecoms giant Telefonica along with some gas companies in Spain. In the US FedEx was affected, France has seen production in some of it’s Renault factories halted. Finally, Russia reported 1000 governmental computer systems has been hit.
So is this the end for ransomware?
No, this infection was stopped by accident the infected are either still infected or have paid up, had they not included the sloppy code in the first place then who knows what would have happened. Microsoft had rolled out patches but some people/organizations/Governments are lazy and don’t bother to apply them. Keep your computers up to date, Good luck because we think we will be seeing a lot more ransomware malware in the coming years.
[Update WannaCry v. 2.0 has been released without the “kill switch”, We wonder what will happen now. Probably not a lot as the media attention has been quite intense so it may not be that big an infection however there is always a few who live in the land where news doesn’t exist and will go a long their day until BAM! Ransom Ware installed and pockets emptied.]





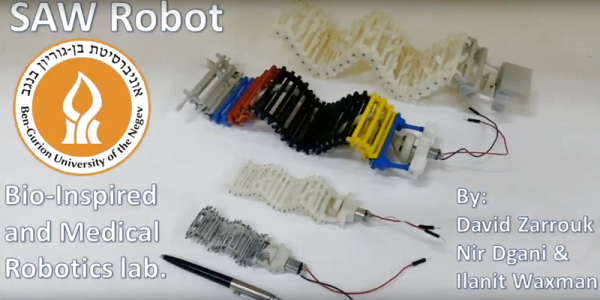
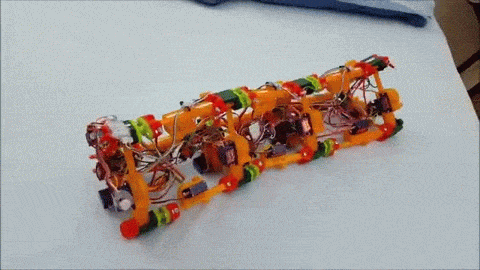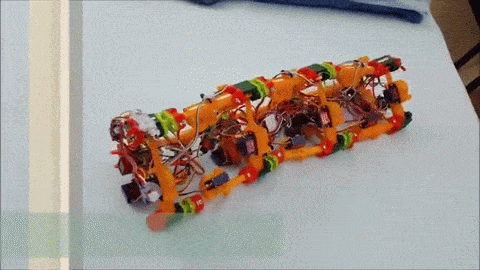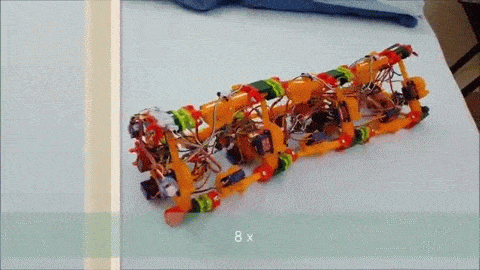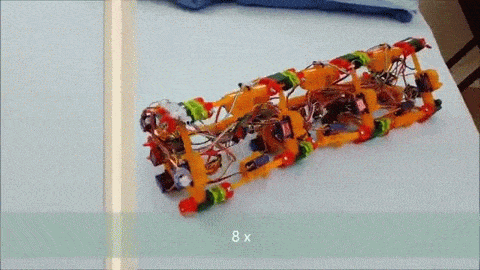

 Version 1 of [Roger]’s robot is only semi-vermiform and is more of
Version 1 of [Roger]’s robot is only semi-vermiform and is more of 








