
Day: August 26, 2010
So You Want To Make A Command Line Interface
[Keba] not only asked Answeres.HackaDay.com, but also sent us an email as follows.
“Can you make a basic guide to designing a good Command Line User Interface?”
Wouldn’t you know the luck, I’m currently working on a Command Line type interface for a project of mine. While after the jump I’ll be walking through my explanation, it should be noted that the other replies to Answers.HackaDay.com are also great suggestions.
Continue reading “So You Want To Make A Command Line Interface”
Building A Laser Cutter From A Weak Laser
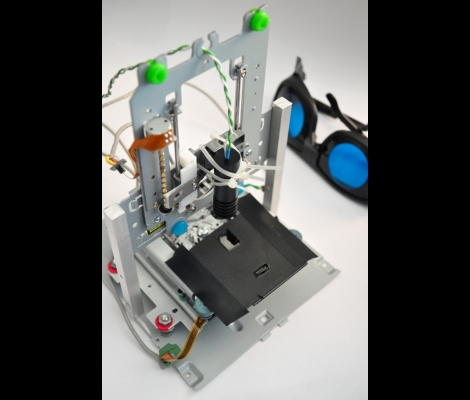
We covet laser cutters and this diy model with a 1 Watt IR diode may be well within our price range. Most commercially available laser cutters, and some homemade ones, work in the 20-100 Watt ranges, using a CO2 laser. They have more than enough power to cut right through a lot of materials so how can a 1W diode compare? It seems that the weaker laser is still quite powerful right at its focal length, so moving that point along the Z axis will let you burn away a larger depth of material. The test rig seen above uses optical drive components for the three axes and managed to cut a rectangular piece out of the black plastic from a CD case.
This isn’t [Peter’s] first try with CNC lasers. He’s the one that’s be working on an open source selective laser sintering platform.
[Thanks Osgeld and Vesanies]
Hacking A Code-protected Hard Disk
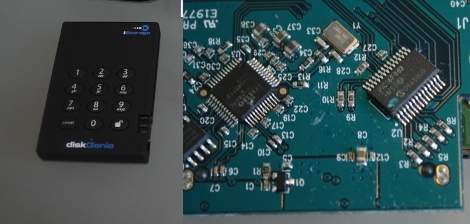
Our friend [Sprite_TM] took a look at the security of a code-protected hard disk. The iStorage diskGenie is an encrypted USB hard drive that has a keypad for passcode entry. After cracking it open he found that the chip handling the keypad is a PIC 16F883 microcontroller. He poked and prodded at the internals and found some interesting stuff. Like the fact that there is an onboard LED that blinks differently based on the code entered; one way for the right code, another for the wrong code of the right number of digits, and a third for a wrong code with the wrong number of digits. This signal could be patched into for a brute force attacking but there’s a faster way. The microcontroller checks for the correct code one digit at a time. So by measuring the response time of the chip an attacker can determine when the leading digit is correct, and reduce the time needed to crack the code. There is brute force protection that watches for multiple incorrect passwords but [Sprite_TM] even found a way around that. He attached an AVR chip to monitor the PIC response time. If it was taking longer than it should for a correct password the AVR resets the PIC before it can write incorrect attempt data to its EEPROM. This can be a slow process, but he concluded it should work. We had fun watching the Flash_Destroyer hammer away and we’d like to see a setup working to acquire the the code from this device.
Burglar Alarm In A Zippo Lighter

[Madmanmoe64] has really done a fantastic job with this burglar alarm built into a zippo. He crammed a picaxe microcontroller, some IR LEDs, an IR sensor, a battery and various switches in there quite well. It almost closes perfectly, something we think he could remedy if it really bugged him that much.
It has several modes, all initiated by a different sequence of button presses. There is the proximity alarm, which sounds when something moves very close. The reverse proximity alarm which sounds when you remove something from its immediate vicinity. A doorbell mode, and a silent alarm mode. Check out the video after the break to see it in action.










