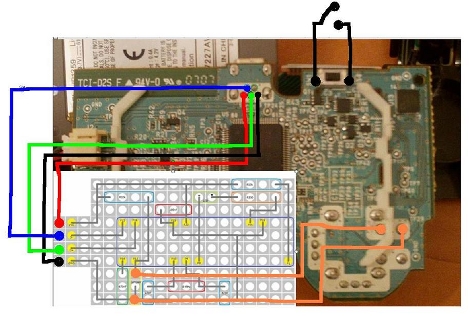
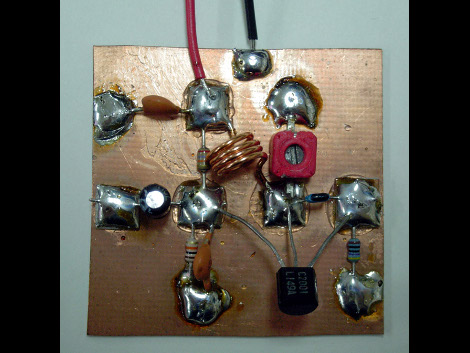
ChemHacker has posted schematics and code for a scanning tunneling microscope. [Sacha De’Angeli] finalized the proof-of-concept design for version 0.1 and released all of the information under the Gnu general public license version 3. You’ll need to build a sensor from a combination of a needle, a piezo, and a ring of magnets. There’s an analog circuit that gathers data from the probe, which is then formatted by and Arduino and sent to your computer.
We haven’t really dabbled in this type of equipment, though we did cover an STM earlier in the year. Take a look at the video after the break and then help jump-start are imagination by sharing your plans for this equipment in the comments.