Love him or hate him, Edward Snowden knew a thing or two about anonymity. In June of 2013, he blew the whistle on the NSA’s out-of-control programs that can target virtually anyone plugged into the digital age. The former CIA employee was working as a contractor for the NSA, where he had access to highly classified documents for many of these general populace surveillance programs. He eventually took off to Hong Kong and released the documents to a handful of reporters. One of these documents was a power point presentation of the NSA complaining about how the TAILS operating system was a major thorn in their side. Naturally, Snowden insisted that the reporters and himself only communicate via the TAILS O/S. He used PGP, which is an encryption method with the highly sophisticated title of “Pretty Good Privacy”, and asked not to be quoted at length for fear of identification via stylometry.
In this article, we’re going to go over the basics of anonymity, and introduce you to methods of staying anonymous while online.
Anonymity vs Privacy
Virtual Private Networks
Let us imagine sending a letter in an enclosed envelope across the country. Once the envelope leaves your house, it’s out in the open. Anyone can see it. Anyone can read the sending and receiving addresses. They cannot, however, see the contents of the envelope, and therefore the information contained within the letter. In this case, you have privacy, but not anonymity.
A Virtual Private Network, or VPN, can provide you with privacy. Like our letter example, the IP addresses of  your computer and the server on the VPN side are visible. The data exchanged between the two is encrypted. Remember that a VPN will provide you with privacy, but not anonymity. Many of the LulzSec hackers that we talked about in the first article in this series made use of the popular hidemyass VPN. This kept their activities private from the prying eyes of law enforcement. In order to maintain anonymity, they used fake accounts and paid for the VPN service with anonymous bitcoins.
your computer and the server on the VPN side are visible. The data exchanged between the two is encrypted. Remember that a VPN will provide you with privacy, but not anonymity. Many of the LulzSec hackers that we talked about in the first article in this series made use of the popular hidemyass VPN. This kept their activities private from the prying eyes of law enforcement. In order to maintain anonymity, they used fake accounts and paid for the VPN service with anonymous bitcoins.
TOR
Going back to our letter example, let us imagine we send the letter with no envelope. The information within the letter is freely available for anyone to read. But we send it in a way that makes it to go through several different places before it reaches its final destination. We do this to the point that it becomes impossible for the receiver to know the sender’s address. They can see the house that sent it to them, but not your house. Now you have anonymity. But because the information within the letter is exposed, you have no privacy.
TOR stands for The Onion Router, and routes internet traffic through various hops between TOR relays in order to hide the origin and destination IP address. But it does not encrypt any data, and anyone who intercepts it coming off the exit relay can read it. They just can’t tell where it came from.
Becoming a Ghost in the Network
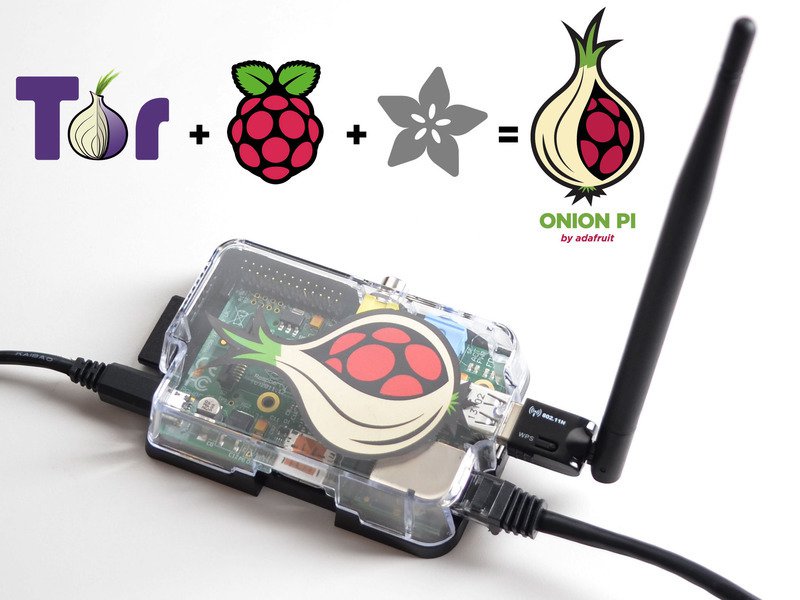
You should be asking yourself if you can use a VPN and TOR together, thereby providing yourself both anonymity and privacy. That answer is yes. There are even VPN services that use TOR. The question is in which order – VPN to TOR or TOR to VPN. This is a hotly debated subject, and both have their advantages and disadvantages. Using TOR through a VPN will keep your ISP from knowing you’re using TOR. Using a VPN through TOR will hide your data from the TOR exit nodes. Either way, you should pay for your VPN service with an anonymous form of payment. [Jake Davis], aka [Topiery], the spokesperson for LulzSec, was outed by his VPN when they were pressed by the UK government. If he had paid for his VPN anonymously, it is likely that he would have never been caught. There is one original LulzSec hacker that remains unknown to this day – [AVUnit]. We can only assume that he or she was able to maintain perfect anonymity…a true ghost on the internet.
There are also TOR enabled routers that will send all traffic through the TOR network. If you don’t trust the commercial options, you can always bake yourself an Onion Pi.
Don’t be Stupid
No form of electronic countermeasures to keep your anonymity intact can save you from dumb decisions. A few years ago, a Harvard student emailed a bomb threat to his university. He sent the threat through the TOR network, but used the university’s WiFi system. The FBI simply correlated the time the threat was sent to the only student using TOR at the time. We’re glad he was caught, it’s one thing to want privacy and anonymity, it’s another to abuse those virtues for the purposes of mayhem.
If you intend to remain anonymous, you cannot put away your common sense. Do not use social media programs, disable Javascript and ensure your browser is sandboxed. Tor and VPNs can give you a cloak of invisibility, but it can be rendered useless in a millisecond if you tear a hole in it with a dumb move.
Sources
Darknet: A Beginner’s Guide to Staying Anonymous Online, by Lance Henderson, ISBN-13: 978-1481931380
















This is a pretty poor article for HaD standards
how ’bout some constructive criticism, instead of harsh opinions?
I agree with Infrared: This is a little on the vague side, but that is not always a bad thing! Instead of slamming a new reader (who may be unfamiliar/timid of the subject) with information and the deep deep details of how it all plays together, that would otherwise scare them off, you have provided a SEMI top level view of how anonymity and the tools to stay anonymous pull together. I personally would have liked to see more of an example as to why you would want to disable JS, even though we all know why, maybe the new guy doesnt.
Regardless. Great work HAD
But for someone to say “HaD Standards” must mean that he/she is an oldie on here.
Yet another political opinion piece unrelated to meaningful facts or insights!
Last month our company IT department discovered all outbound traffic with a GPG signature is being routed by google g-mail through different Tier 2 networks that demand an insecure dns configuration. Sorry guys, your dick pic sent over to a friend is still being held by US officials for future coercion of intelligence assets. The sad part is Google is probably still part of the charade, and we must assume that perhaps they always were.
Finding people is relatively easy these days: PGP style public key systems are easier, as if you use a public key server — chances are it is actively being regularly indexed. A free email address is usually verified by phone, that is bought at a store with a US based credit card. The autodialler program for voice samples started a few years ago, and correlates targets with multiple voice lines not associated via a transaction history record.
Hypothetically, if you manage to dodge normal identification, and think you can avoid having your packages routed into the US for a 3 week inspection delay: There are still people you socialized with online that know real contact information, companies like e-bay/face-book/yahoo/google are legally required to disclose the known user histories, and the exit traffic profile over tor is already known by your ISP when not using tor.
Anonymity is dead!
One thing is for certain: there is no stopping them;
the ants will soon be here. And I for one welcome our new insect overlords.
https://xkcd.com/538/
Well thats depressing
And talkng of your nickname..
I don’t think president Hillary is going to make thing any better, from past pushes and views we know she’ll lock down the internet (and the rest of communication) another notch or..five.
As for the unlikely event of a president Trump, well it might be different with some specific focus, but not necessarily better.
All in all it looks bleak and we can only hope they get distracted by other pet projects.
Just because something is publicly accessible does not mean that people want it to be publicized.
Please do note that TOR is nowadays known to be ‘insecure’
This is just as vague as the article, care to be more specific? Are you talking about CMEs project to dox anonymous users for the FBI? Certainly if you control the exit nodes then you can see the traffic going through them and if you have a comprehensive view of all traffic traversing the internet like the NSA does you can probably correlate what’s coming out of the end nodes with the users themselves but beyond that are you talking about something else? Are you saying we might as well use nothing because the only people we need anonymity from is the NSA?
Sorry to be so vague, im actually very interested in these sort of networks (theres moar) and use them some times, but not a whole lot because of all the bad shit they attract. The thing is i dont wanna get some sort of target on my back just for ‘knowing things’ or something. (while on HaD its obviously fine to talk about, the general public still seems to think only terrorists need anonymus interwebs, and who knows what spiders pass this site lol)
Anyway in short its pretty much what you point out, there’s been several cases where ‘American government related organisations’ appeared to have access, rolling up al sorts of misdeeds done on the tor network (not that im against that btw) darpa (‘funded by us tax dollahs’) owns by far the biggest portion of servers (entrance/exit nodes) tor was actually developed by and for the American army, it all adds up, you cant tell me that they cant track people trough the tor network, im not denying its harder to do, but come on, with all the insight info needed, access to most servers, you cant tell me America (any government body) cant access tor.
And then yea, if you read further into some of the recent cases involving tor, theres some slip ups in explanations from feds which just raise more questions. Theres something to say for how anonymus Tor can really be if ‘1 player holds all cards’.
Imo tor is (while never created with that intention) turned into a honey pot for people looking to do ‘uncool’ things, which i actually guess is a good thing, its just a shame that so many people with harmless usage in mind will also get themselves on the radar, while thinking they do the opposite.
then just use old school hacker tactics. you connecte elsewhere and not in a pattern. Mcdonalds on 53rd tonight, Krispy Kreme a town over tomorrow night, The library in the small town to the west the next… etc… map your locations and keep track of it to look for patterns you can disrupt. Humans like making patterns and only by trying to catch yourself can you disrupt them.
Welcome to what we had to do in the 80’s, except we used phone lines and had to have physical access.
Assuming that you don’t carry a cellphone (or tablet with apps) that broadcast your GPS location. You’ll stand out as the subscriber cell tower location correlates with the access each time.
“Assuming that you don’t carry a cellphone (or tablet with apps) that broadcast your GPS location.”
Or a car with OnStar etc. because they also work through the cellular network. The device does not need a GPS callback because the phone network always knows your approximate location anyways, which is how it routes telephone calls to you – it knows the cells where you were last heard in, and in the city the cells are dense enough to pinpoint you to a street completely passively. If you make a call or they make the network “ping” the phone, they can track you to the building.
also be sure to pay in cash at these establishments and not use your credit card :P
TOR “turned into a honey pot for people looking to do ‘uncool’ things”. There are tons of examples of people using technology for nefarious dealings. Hell I could PoD (ping of death) HAD. Should we deprecate PING because it could be used for evil? Same can be said about guns, bathrooms, republicans…. list goes on….
Not just technology. We can use our own body to cause damage, so should we all just kill ourselves?
But how should we kill ourselves?
Can you elaborate on that?
That is a bold statement. I’d rather say: it is known not to be ultimately secure. However there are “threats” which can perfectly by mitigated with TOR. For example: I don’t want my ISP to know what I am doing or I don’t want some websites to know where I am staying. Of course, if an adversary controls a larger part of of a network then it is rather hard to hide anything if the network is not fully congested.
@steelman
I agree. Has anyone read the orange book? (rainbow series) http://csrc.nist.gov/publications/history/dod85.pdf The only way to gain trust in a networkable computing environment is to own the network and control.
Sure did, but for some reason it kept going on about audio and data, and multisession writing…
All tutorials describing TOR I can remember recommend using SSL/TLS enabled services.over TOR rather than VPN.
if the fbi can trace a bomb scare then why dont they trace copyright and child porn violators too?
fbi working together with mpaa and riaa and centers for missing and exploited children?
Copyright infringement is not a criminal matter unless it’s done on a commercial scale. It’s a civil matter, and so the FBI doesn’t technically have anything to do with it.
Of course the copyrights industry uses the FBI as a scare tactic anyways.
vpn to tor to the other vpn
Using a laptop paid for with cash on Crags list(and only being used once before going into the fire pit) using the open wireless down the street. Now no one will know I enjoy playing candy crush.
Go check out the Qubes OS.
This will be useful in the now & future when FBI attempts to plant tracking malware etc.
I just wan to say that i’m extremely unfamiliar with the subject and very please that you took your time to explain in a way in wich i was able to understand! And as time goes by I’m more convince that we need to start to do something so the gov.those not get to be in our business illegally like most of the time does! Thank you and although i’m a mess right now i will get started on the matter(rageAgainstTheMachine).nothing to hide but still i own the right to my privacy!!!!!
what about speed ??? will it be hampered
Yes it will, always.
This may be kicking the hornet’s nest here, but what’s the point of using a VPN _and_ TOR? The reasons stated in the article don’t quite add up for me. If you use a VPN to access TOR, then yeah, your ISP doesn’t know you’re using TOR, but they do know you’re using a VPN, and your VPN provider knows you’re using TOR. And a VPN provider is just a secondary ISP that you subscribe to.
Heck, I could sign up for a bunch of VPNs, connect to the first one normally, then connect to the second _through_ the first and so on. In the end I would have something very much like TOR, but more expensive and with a very limited number of nodes.
Also, TOR traffic is very much encrypted while in-transit between nodes. No node (other than the originator) has complete knowledge of the transmission (origin, destination, hop list, content). Only traffic leaving the exit node is “unencrypted” – and necessarily so for the ultimate destination to make sense of it. That’s why they tell you to always use an encrypted channel (SSL/SSH or similar) when using TOR. The same applies to any general VPN service.
I’m pretty sure ALL VPN are monitored 24/7 by at least 5 different countries simultaneously.
But the encryption could help.. unless they got the key, and they have many ways to get keys, either by weakness in the protocols or hacking the server or hacking the user.
And of course a VPN bottlenecks all your traffic nicely for anyone that manages to get access, so that makes things so much easier for those spooks.
And apart from actually reading the traffic data the VPN also gives access to timestamps of course, also often helpful in tracking targets.And that works for a large part even when it stays encrypted.
That part about owning the network is correct. We must have a complex distributed “outernet”. Where each node connects to other nodes and the internet. So information cannot be traced the entire way. Pass it between networks a few times along the way. Each node could also host a web page or storage space etc. A bit of delivery randomization. Hell take advantage of comwarnfrontchar. Get some solar powered ones and leave them near open hotspots.