Famed whistleblower [Edward Snowden] has recently taken to YouTube to announce Haven: an Open Source application designed to allow security-conscious users turn old unused Android smartphones and tablets into high-tech monitoring devices for free. While arguably Haven doesn’t do anything that wasn’t already possible with software on the market, the fact that it’s Open Source and designed from the ground up for security does make it a bit more compelling than what’s been available thus far.
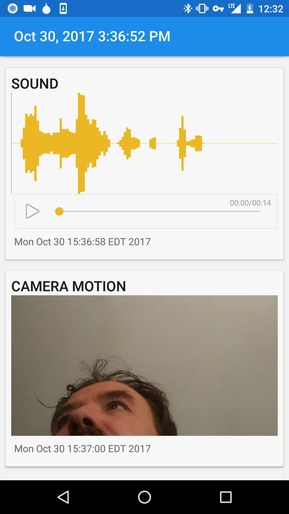 Developed by the Freedom of the Press Foundation, Haven is advertised as something of a role-reversal for the surveillance state. Instead of a smartphone’s microphone and camera spying on its owner, Haven allows the user to use those sensors to perform their own monitoring. It’s not limited to the camera and microphone either, Haven can also pull data from the smartphone’s ambient light sensor and accelerometer to help determine when somebody has moved the device or entered the room. There’s even support for monitoring the device’s power status: so if somebody tries to unplug the device or cut power to the room, the switch over to the battery will trigger the monitoring to go active.
Developed by the Freedom of the Press Foundation, Haven is advertised as something of a role-reversal for the surveillance state. Instead of a smartphone’s microphone and camera spying on its owner, Haven allows the user to use those sensors to perform their own monitoring. It’s not limited to the camera and microphone either, Haven can also pull data from the smartphone’s ambient light sensor and accelerometer to help determine when somebody has moved the device or entered the room. There’s even support for monitoring the device’s power status: so if somebody tries to unplug the device or cut power to the room, the switch over to the battery will trigger the monitoring to go active.
Thanks to the Open Source nature of Haven, it’s hoped that continued development (community and otherwise) will see an expansion of the application’s capabilities. To give an example of a potential enhancement, [Snowden] mentions the possibility of using the smartphone’s barometer to detect the opening of doors and windows.
With most commercially available motion activated monitor systems, such as Nest Cam, the device requires a constant Internet connection and a subscription. Haven, on the other hand, is designed to do everything on the local device without the need for a connection to the Internet, so an intruder can’t just knock out your Wi-Fi to kill all of your monitoring. Once Haven sees or hears something it wants you to know about it can send an alert over standard SMS, or if you’re really security minded, the end-to-end encrypted Signal.
The number of people who need the type of security Haven is advertised as providing is probably pretty low; unless you’re a journalist working on a corruption case or a revolutionary plotting a coup d’etat, you’ll probably be fine with existing solutions. That being said, we’ve covered on our own pages many individuals who’ve spent considerable time and effort rolling their own remote monitoring solutions which seem to overlap the goals of Haven.
So even if your daily life is more John Doe than James Bond, you may want to check out the GitHub page for Haven or even install it on one of the incredibly cheap Android phones that are out there and take it for a spin.















Sweet I have a small pile of old single core and dual core android phones that I will want to test these out on.
Watching the video I realized this is first time I ever watched/listened to Snowden speak. Wow. Is he always so….what’s the word…cringe? It seemed like he was trying to do a Steve Jobs thing. Well, Steve Jobs plus an infomercial salesman.
Glad this article explained WTF the project is about as well, since that video did little to explain the why and how of Haven.
I didn’t think he sounded like that when I heard him before… like he is trying to push this too much maybe?
Perhaps they got to him.
Consider that the management engine would have full access to this app.
I’m sure his Russian masters have their hands in the Haven dough.
The purpose of this software is not to open source spying for random script kids. Its an eye opener for people thinking their phone is something belonging to the private domain. Further should this take off as a tool for social hacking, phones have to change i,e, making them harder for governments to use against the opposition. So what he has done is twofold, both educational and political pressure on tech companies. Claiming he is dirty solely because he has celebrated 6 Christmases in Russia, is teaming up with the dark side!
I watched the video earlier and I didn’t quite get why this is so important until I read “The number of people who need the type of security Haven is advertised as providing is probably pretty low; unless you’re a journalist working on a corruption case or a revolutionary plotting a coup d’etat, you’ll probably be fine with existing solutions.”
So this could have been used to watch who planted the bomb in journalist Caruana Galizia’s car… or who murdered Anna Politkovskaya who wrote on the war in Chechenya and the book ‘Putin’s Russia’…. or who spiked Alexander Litvinenko tea with Polonium 210.
Of course these were all contract killings… the people who perpetrated them might go to jail but those who paid for them will never see the inside of one.
I do have one comment though…. I don’t think Snowden is the most knowledgeable guy in the room when it comes to security. When he was in exile in Hong Kong and he spoke with reporters he had them toss their cell phones in the freezer so they could not be traced. That doesn’t really work. If you want to quickly interfere with phone reception quickly you would be better off throwing it in the microwave oven (though even that isn’t the perfect solution).
Maybe he knows more than you… Obviously it was done to stop audio recordings. Fridges walls have foam insulation.
Actually you’d have to throw them in the Microwave oven then leave that location and go somewhere else! That wayou you wouldn’t be tracked or traced. Remember cellphones can be remotely turned on and manipulated, unless of course you remove the battery. Turning them off is a pacifier, if the battery is charged and i stalled they are always really on. Who knows what hacks exist to remotely turn a simple cellular phone into a bug unwittingly carried by its owner. I used to own one that had an silent auto answer, I would place it where I needed it then call it and listen to what was going on at that location.
Great. Now cops and spooks will start using intercepting (rather than pass-through) stingray devices when breaking into a place.
I definitely don’t use Android to secure my home!
Perfect tin foil hat material.
“Made by” is probably pretty strong. Snowden is definitely the face of the project because he’s head of Freedom of Press Foundation, but it doesn’t seem like he was actually involved with the creation of the app outside of probably an advisory role.
But point taken. A lot of stuff that would have been considered nutter-talk was shown to be tame compared to what the NSA is really capable of, and we have him to thank for a lot of that.
Problem is I don’t really “own” the phone. I’m under the constant assumption that at any moment my telco or Google (or Apple) could pretty much do whatever they want on my phone.
+1
So it is an “Android app”, and not a replacement OS. So the underlying OS is 100% secured by Google (“Don’t be evil”). Yea, hmmmmmmm ….
And with each online camera added to the world, “big brother” is one step closer.
In practice “big brother” isn’t the state monitoring the people… it’s the people monitoring themselves. Putting online every bit of information about themselves willingly and thoughtlessly online for others to see. It starts innocently, facebook, twitter or whatever service that let’s you comment your own life or that of others. The evidence of our actions is piling up more and more each day. Mostly these actions are harmless and do not deserve to be spread around, though we do. And eventually, this information is being used against you, interpreted wrong, twisted or misjudged.
So in essence, WE are big brother!
And it all started so innocently… with a baby monitor.
I’ve started to read through the guardianproject’s haven a bit more, and it appears that it is more to protect a reporters base of operations. So they would setup a haven phone monitoring their workspace and activate it when they needed to go elsewhere and it would notify them if and when their inner sanctum was compromised and send photos if configured that way. So it is an advanced form of hair on a door, where you can’t put the hair back, but you could use a Jammer and smash the phone, if you can find it.
“it’s the people monitoring themselves. Putting online every bit of information about themselves willingly”
^^^^^ THIS !! ^^^^^
It’s incredulous for folks to complain about a “lack of privacy”, “invasion of privacy” – when they THEMSELVES – VOLUNTARILY put their personal information out there for PUBLIC consumption !!
Now with regards to public records, what needs to happen is all these municipal and federal databases need to be immediately shut down. Back in – prehistoric times – when one wanted to look up a tax record of who owns a particular piece of property, they needed to take a physical trip down to the county clerk’s office. Restore that extra step and it’ll immediately restore some element of privacy.
Same thing with banking. Immediately end smart phone and online apps ! In one swoop, the “hacking” threat surface is instantly reduced. Now, one would have to physically walk into a bank and interact with a human agent to transact business.
The point of all these anachronistic desires is, WE are our own worst enemies. In the mad rush for “convenience”, we’ve surrendered our privacy to technology controlled by numerous actors whom no one has any particular control over.
I think another important point is the app runs local. There is no cloud or third party to “trust”
Umm apart from the fact your using software wrote by people who can easily have placed back doors into, on the Android platform, which Google has multiple back doors and direct access routes even for encrypted phones lol.
So when your allegedly fool proof security system decided to fire up your phone/app and report to you, it has to send via your cell provider or your isp routers/servers, this gives the app creators and/or google direct access to the information your phone is sending, in an ideal world, they can intercept that message, delete/modify it, then even send data back to the phone or app and delete any trace of the incursion into your now 100% protected sanctum (lol).
So when you decide to talk about stuff you want kept private, your under a false sense of being secure, never mind that your phone is probably reporting back anything it sees/hears, but now you also have numerous bugs around your place you don’t even bother to sweep for, because no one has intruded and your so safe and secure thanks to your android phone and this app…
Pass, would rather stick to analogue methods that are not possible to hack lol. Heck even my home cctv setup on local Lan, with encrypted communication over the internet is more secure at telling me if anyone has intruded than the above option. Ok it relies on the internet, but when I have a back up hdd hidden out in the garage in a safe, if anyone thinks they can wipe or steal the main recording unit in the house, I would still have a backup of the footage they would not know existed to review who stole or deleted my hdd lol.
Now if I was mega paranoid, could have multiple hdd throughout the house as secondary, tertiary backups to the backup etc. Could even have a remote NAS etc which would give footage up until the internet gets cut.
The utility of Haven is limited by the fact that the phone itself can be compromised and the application’s behavior manipulated to give a target a false sense of security. They’d install a covert malicious ADB service and your phone would get SMASheD. Sure you can spy on the average person with it but the fact that it exists would have professionals looking for phone signals in any target location then they would compromise those phones and therefore know that it was running. They’d go after the phones because knowing what is going on inside a target location is always going to be useful, finding Haven running would just tip them off to be even more careful and suggest to them that you were worth the extra time and effort to monitor more closely.
But for busting criminals in your house, or assholes in your office at work it may be ideal, just watch out for the legal ramifications of placing bug in work spaces.
I totally support Snowden, but be aware that this app although useable against common thugs or third world police, could be ineffective if any 3 letter agency decides you’re worth to be spied on. All mobile phones are closed source in their most critical parts (device drivers) and government agencies, especially US ones, might very likely have full access to those device drivers that nobody can audit. If they know you have an app that will shoot photos or record audio as soon as someone enters your room, rest assured that a magic packet coming from the cellular network, or the internet, will shut off the camera or mics for the needed time.
Let me repeat one more time: you can’t have security on any cellphone in the world, including those marketed as super safe, until all code running on them -all of it, including all firmware plus all device drivers- won’t be released as FOSS, publicly examined then recompiled and installed back. Before that day the level of security on any cellphone on planet Earth is an absolute zero.
Apparently its news that the guys twitter account vanished on Christmas day, wonder if its somehow related to this?
Wow. Super impressive… pfft Welcome to 2006, Snowden.
-Funny to hear how he sounds like the douche he is.