After a quiet week in the news cycle, surveillance concern Flock jumped right back in with both feet, announcing a strategic partnership with Amazon’s Ring to integrate that company’s network of doorbell cameras into one all-seeing digital panopticon. Previously, we’d covered both Flock’s “UAVs as a service” model for combating retail theft from above, as well as the somewhat grassroots effort to fight back at the company’s wide-ranging network of license plate reader cameras. The Ring deal is not quite as “in your face” as drones chasing shoplifters, but it’s perhaps a bit more alarming, as it gives U.S. law enforcement agencies easy access to the Ring Community Request program directly through the Flock software that they (probably) already use.
surveillance38 Articles
Spy Tech: Build Your Own Laser Eavesdropper
Laser microphones have been around since the Cold War. Back in those days, they were a favorite tool of the KGB – allowing spies to listen in on what was being said in a room from a safe distance. This project by [SomethingAbtScience] resurrects that concept with a DIY build that any hacker worth their soldering iron can whip up on a modest budget. And let’s face it, few things are cooler than turning a distant window into a microphone.
At its core this hack shines a laser on a window, detects the reflected light, and picks up subtle vibrations caused by conversations inside the room. [SomethingAbtScience] uses an ordinary red laser (visible, because YouTube rules) and repurposes an amplifier circuit ripped from an old mic, swapping the capsule for a photodiode. The build is elegant in its simplicity, but what really makes it shine is the attention to detail: adding a polarizing filter to cut ambient noise and 3D printing a stabilized sensor mount. The output is still a bit noisy, but with some fine tuning – and perhaps a second sensor for differential analysis – there’s potential for crystal-clear audio reconstruction. Just don’t expect it to pass MI6 quality control.
While you probably won’t be spying on diplomats anytime soon, this project is a fascinating glimpse into a bygone era of physical surveillance. It’s also a reminder of how much can be accomplished with a laser pointer, some ingenuity, and the curiosity to see how far a signal can travel.
Continue reading “Spy Tech: Build Your Own Laser Eavesdropper”
Supercon 2023: Alex Lynd Explores MCUs In Infosec
The average Hackaday reader hardly needs to be reminded of the incredible potential of the modern microcontroller. While the Arduino was certainly transformative when it hit the scene, those early 8-bit MCUs were nothing compared to what’s on the market now. Multiple cores with clock speeds measured in the hundreds of megahertz, several MB of flash storage, and of course integrated WiFi capability mean today’s chips are much closer to being fully-fledged computers than their predecessors.
It’s not hard to see the impact this has had on the electronics hobby. In the early 2000s, getting your hardware project connected to the Internet was a major accomplishment that probably involved bringing some hacked home router along for the ride. But today, most would consider something like an Internet-connected remote environmental monitor to be a good starter project. Just plug in a couple I2C sensors, write a few lines of Python, and you’ve got live data pouring into a web interface that you can view on your mobile device — all for just a few bucks worth of hardware.
But just because we’re keenly aware of the benefits and capabilities of microcontrollers like the ESP32 or the Pi Pico, doesn’t mean they’ve made the same impact in other tech circles. In his talk Wireless Hacking on a $5 Budget, Alex Lynd goes over some examples of how he’s personally put these devices to work as part of his information security (infosec) research.
Continue reading “Supercon 2023: Alex Lynd Explores MCUs In Infosec”
Hackaday Links: March 10, 2024
We all know that we’re living in a surveillance state that would make Orwell himself shake his head, but it looks like at least one company in this space has gone a little rogue. According to reports, AI surveillance start-up Flock <<insert gratuitous “What the Flock?” joke here>> has installed at least 200 of its car-tracking cameras on public roads in South Carolina alone. That’s a serious whoopsie, especially since it’s illegal to install anything on state infrastructure without permission, which it appears Flock failed to obtain. South Carolina authorities are making a good show of being outraged about this, but it sort of rings hollow to us, especially since Flock now claims that 70% of the population (of the USA, we presume) is covered by their technology. Also, police departments across the country are in love with Flock’s service, which lets them accurately track the movements of potential suspects, which of course is everyone. No word on whether Flock will have to remove the rogue cameras, but we’re not holding our breath.
Big Candy Is Watching You: Facial Recognition In Vending Machines Upsets University
Most people don’t think too much of vending machines. They’re just those hulking machines that lurk around on train stations, airports and in the bowels of school and office buildings, where you can exchange far too much money for a drink or a snack. What few people are aware of is just how these vending machines have changed over the decades, to the point where they’re now collecting any shred of information on who interacts with them, down to their age and gender.
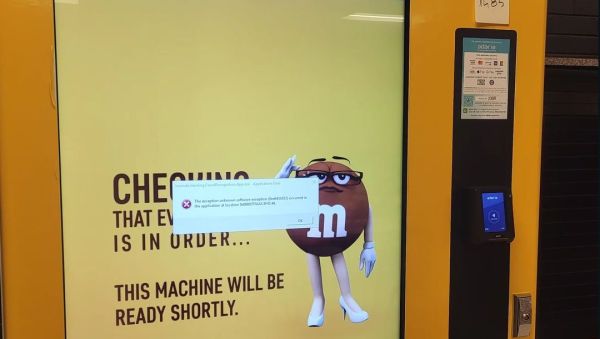
How do we know this? We have a few enterprising students at the University of Waterloo to thank. After [SquidKid47] posted a troubling error message displayed by a campus M&M vending machine on Reddit, [River Stanley] decided to investigate the situation. The resulting article was published in the February 16th edition of the university’s digital newspaper, mathNEWS.
In a bout of what the publication refers to as “Actual Journalism”, [Stanley] found that the machine in question was produced by Invenda, who in their brochure (PDF) excitedly note the many ways in which statistics like age, gender, foot traffic, session time and product demographics can be collected. This data, which includes the feed from an always-on camera, is then processed and ‘anonymized statistics’ are sent to central servers for perusal by the vending machine owner.
The good news is that this probably doesn’t mean that facial recognition and similar personalized information is stored (or sent to the big vaporous mainframe) as this would violate the GDPR and similar data privacy laws, but there is precedence of information kiosks at a mall operator taking more liberties. Although the University of Waterloo has said that these particular vending machines will be removed, there’s something uncomfortable about knowing that those previously benign vending machines are now increasingly more like the telescreens in Orwell’s Nineteen Eighty-Four. Perhaps we’re already at the point in this timeline were it’s best to assume that even vending machines are always watching and listening, to learn our most intimate snacking and drinking habits.
Thanks to [Albert Hall] for the tip.
Hackaday Links: September 10, 2023
Most of us probably have a vision of how “The Robots” will eventually rise up and deal humanity out of the game. We’ve all seen that movie, of course, and know exactly what will happen when SkyNet becomes self-aware. But for those of you thinking we’ll get off relatively easy with a quick nuclear armageddon, we’re sorry to bear the news that AI seems to have other plans for us, at least if this report of dodgy AI-generated mushroom foraging manuals is any indication. It seems that Amazon is filled with publications these days that do a pretty good job of looking like they’re written by human subject matter experts, but are actually written by ChatGPT or similar tools. That may not be such a big deal when the subject matter concerns stamp collecting or needlepoint, but when it concerns differentiating edible fungi from toxic ones, that’s a different matter. The classic example is the Death Cap mushroom (Amanita phalloides) which varies quite a bit in identifying characteristics like color and size, enough so that it’s often tough for expert mycologists to tell it apart from its edible cousins. Trouble is, when half a Death Cap contains enough toxin to kill an adult human, the margin for error is much narrower than what AI is likely to include in a foraging manual. So maybe that’s AI’s grand plan for humanity — just give us all really bad advice and let Darwin take care of the rest.
Smart Garbage Trucks Help With Street Maintenance
If you’ve ever had trouble with a footpath, bus stop, or other piece of urban infrastructure, you probably know the hassles of dealing with a local council. It can be incredibly difficult just to track down the right avenue to report issues, let alone get them sorted in a timely fashion.
In the suburban streets of one Australian city, though, that’s changing somewhat. New smart garbage trucks are becoming instruments of infrastructure surveillance, serving a dual purpose that could reshape urban management. Naturally, though, this new technology raises issues around ethics and privacy.
Continue reading “Smart Garbage Trucks Help With Street Maintenance”