Years before Steve Jobs showed off the first iPhone, the BlackBerry was already the must-have accessory for mobile professionals. Back then, nobody was worried about watching movies or playing the latest games on their mobile devices, they just wanted a secure and fast way to send and receive email on the go. For that, the BlackBerry was king.
Fast forward to today, and the company is just a shell of what it once was. They don’t even bother making their own hardware anymore. Over the last several years they’ve opted to partner with a series of increasingly obscure manufacturers to produce a handful of lackluster Android phones so they still have something to sell to their dwindling userbase. Anyone excited about the new 5G BlackBerry being built by Texas start-up OnwardMobility? Did you even know it was in the works before now?

But this article isn’t about BlackBerry phones. It’s about something that’s even more irrelevant to consumers: the BlackBerry Smart Card Reader. Technically, this little device isn’t dependent on the phones of the same name, but it makes sense that Research In Motion (which eventually just renamed itself to BlackBerry Limited) would market the gadget under the brand of their most popular product. Though as you might expect, software was available to allow it to work with the BlackBerry phone that you almost certainly owned if you needed a dedicated smart card reader.
For those who might not be aware, a smart card in this context is a two-factor authentication token contained in an ID card. These are used extensively by organizations such as the Department of Defense, where they’re known as Common Access Cards, that require you to insert your ID card into a reader before you can log into a secure computer system. This sleek device was marketed as a portable reader that could connect to computers over USB or Bluetooth. Worn around your neck with the included lanyard, the battery-powered reader allowed the card itself to remain on the user’s body while still being readable by nearby devices.
Civilians will recognize the basic technology from modern “Chip and PIN” debit and credit cards, but we’ve never had to stick one of those into our laptop just to log in. To be sure, the BlackBerry Smart Card Reader was never intended for the average home computer user, it was sold to companies and organizations that had tight security requirements; which just so happened to be the same places that would likely already be using BlackBerry mobile devices.
Of course, times and technology change. These devices once cost $200 apiece and were purchased in vast quantities for distribution to trusted personnel, but are now all but worthless. Even in new and unopened condition, they can be had for as little as $10 USD on eBay. For that price, it’s certainly worth taking a peek inside. Perhaps the hacker community can even find new applications for these once cutting-edge devices.
A Cyberpunk Accessory
The BlackBerry Smart Card Reader looks exactly like the kind of thing I would expect some futuristic military force to use as an authentication device, with a design that’s somehow simultaneously simplistic and aggressive. If somebody told me this thing was a prop from RoboCop or Judge Dredd, I’d believe it.

At least this version, anyway. It seems that the hardware changed a number of times, and each one looks different enough that there’s no mistaking which one is which. It’s probably safe to assume that was intentional from a logistics standpoint. The specimen we’re looking at is the second revision, released in 2009.
The smart card slots into a groove in the front of the device, which keeps it secure while still being completely visible. Only the lower part of the card, where the chip itself is located, is actually covered.
There are no controls or indicators of any sort on the front of the reader. At first glance, you might even think it was some kind of passive holder for the card. Which again, was sort of the point. Defense contractors wouldn’t have worn it all day if it was covered in blinking LEDs and indicators, only modern hackers are into that kind of thing.
On the back there’s small LCD, a tri-color LED, and a single button. A tap of the button turns on the Bluetooth radio and displays the PIN code on the LCD, while holding the button resets the device. There’s no power button, and as long as the battery isn’t flat, the device appears to always be on. Though after awhile it will go into some sort of sleep mode and display “OFF” on the LCD.

Built for Business
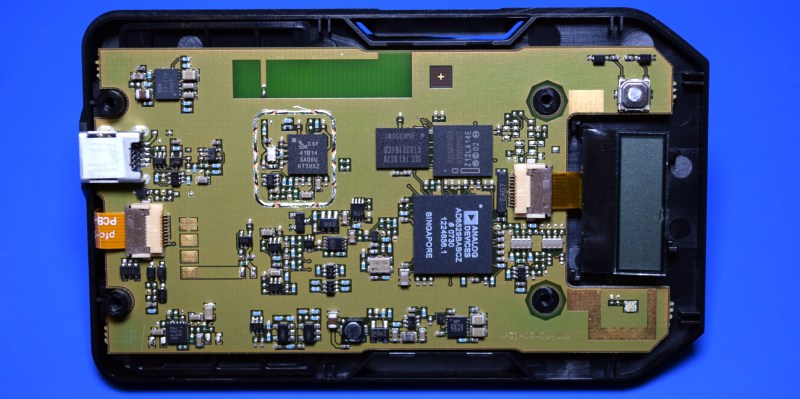
The BlackBerry Smart Card Reader easily comes apart after the removal of four T6 screws located behind the battery cover. There wasn’t even a tamper-evident sticker over any of the screw heads, which frankly surprised me for a high security device.
Inside we’re presented with a concise PCB design, without even a hint of silkscreen markings to help us get our bearings. There are no obvious programming headers or debug points. If there was ever a board layout that said “No User Serviceable Parts Inside”, this would be it. Interestingly, while there’s clearly a place where one would have been mounted, the RF shield that would have surrounded the CSR 41B14 Bluetooth chipset has not been installed.
The star of the show would appear to be the Analog Devices AD6529BABCZ, but I’ve been unable to find any documentation on what this chip actually is. But I did run into a few mentions of the AD6528, which is a GSM baseband processor intended for mobile phones and PDAs.
 At first I thought it was unrelated, but a close look at some of the features of the chip shows interesting parallels with the Smart Card Reader. The AD6528 has a 32-bit ARM7 processor with onboard RAM, a display interface, integrated USB support, and offers various low power modes. Naturally it also has support for interfacing with the SIM cards, which themselves are very similar to the chips used in smart cards. The dimensions and package of the AD6528 also match the AD6529.
At first I thought it was unrelated, but a close look at some of the features of the chip shows interesting parallels with the Smart Card Reader. The AD6528 has a 32-bit ARM7 processor with onboard RAM, a display interface, integrated USB support, and offers various low power modes. Naturally it also has support for interfacing with the SIM cards, which themselves are very similar to the chips used in smart cards. The dimensions and package of the AD6528 also match the AD6529.
Given these facts, we may be looking at a customized version of the AD6528 that was made specifically for this high-security application. When you’re trying to sell a device to the Department of the Defense, spinning up a new chip is hardly out of the question. This version of the chip may even have been bumped up to Industrial or Military/Aerospace rating.
Next to the AD6529 there’s a Intel 320W30 flash memory chip that likely holds the device’s firmware, and a Samsung K1S32161CD SRAM chip.
Keeping Trim
Easily the most impressive feature of the BlackBerry Smart Card Reader, especially given the era in which it was designed and built, is how thin it is. This is partially due to the fact that there’s absolutely nothing on the back side of the PCB, which allowed it to be pushed as tightly as possible against the inside of the case.
A close look at the chip interface also shows how the designers were able to avoid putting an actual power switch on the device. When a card is fully seated in the reader, a miniature switch is pressed in. We didn’t see this inside the chip reader of the VeriFone 925CTLS payment terminal, as there was no reason to ever shut the hardware down. But in a battery powered device, a function to put the hardware to sleep when a card isn’t present will greatly increase the runtime.
Speaking of the battery, they could have made the BlackBerry Smart Card Reader even slimmer if they hadn’t used the same 1150 mAh C-S2 battery utilized by contemporary BlackBerry phones, though that was a clever decision considering their customers likely already had stockpiles of the cells from their phone fleets.
Putting it to Use
Realistically, the components inside of this device are all so antiquated at this point that there’s not much to salvage other than perhaps the chip interface itself if you’re looking to experiment with smart cards. The enclosure could potentially be reused, and it already has the interface and battery compartment for BlackBerry C-S2 batteries. But unless you’re building a DIY smart card reader, I’m not sure what else the case design would really lend itself to.
Trying to reprogram it would be tricky, to say the least. For one thing, there doesn’t appear to be any public data on the chip that’s driving it. More practically, there’s no sign of a programming header, and trying to remove the BGA flash chip and reading the firmware off of it manually is farther than most hackers would be willing to go.
So can we use it as-is? Unfortunately, that’s not looking very good either. When connected over USB, the reader doesn’t appear to be supported by existing open source smart card libraries such as PCSClite. I can see the reader when scanning for Bluetooth devices, but to date, I’ve been unable to successfully pair with it.
Officially the Windows software for the device supports XP and Vista, so if you could find a copy of it, you could potentially run it in a VM and sniff the USB packets with Wireshark to come up with a modern open source driver. But besides taking on an interesting challenge, there’s not much point in it; you can pick up a newly manufactured smart card reader for about as much as one of these relics costs.
As much as it pains me to say it, I don’t think there’s anything very exciting you can do with the BlackBerry Smart Card Reader. It might be worth picking a few up to complement your dystopian cyberpunk cosplay, but that’s about it. Though if you do manage to come up with something, we’d love to hear about it.


















https://hackaday.com/wp-content/uploads/2019/06/verifone_reader.jpg
the verifone pad you mention most definitely has the insertion switch, which likely activates the chip contact pins after full insertion so the chip is not powered on or shorted part way during insertion.
It does look that way in the image, but that metal piece isn’t actually attached to anything electrically. It seems like that tab is just a way to make sure nobody pushes a card so far into the reader that it blows out the back of the plastic housing.
i recall it having electrical contacts to act as a “card fully inserted” switch. i will have to dig into my warranty-voided mx925 again when i get home
I’m hyped for the 5G BlackBerry. Was planning to get a KEY2 soon but now I’ll just hold off with my Priv until the new one launches
I see it will have Google Android, I don’t see how that will be a “secure” phone…
(sigh!)
https://www.slashgear.com/blackberry-5g-phone-coming-in-2021-with-security-and-design-at-the-forefront-30635550/
Yeah they’ve sadly been Android-only for half a decade now. Still the best and one of the only choices for a phone with a keyboard though
You may want to look into the Cosmo Communicator or their less wisely named upcoming phone, the Astro Slide..
Rhymes with astro glide…*shudders*
https://www.pine64.org/2020/07/29/invitation-to-play-along/
Maybe this could be something to wait for? Slide keyboard for non android phone?
Now THIS I am excited about! Otherwise the Pyra might be a usable alternative..
I loved my Priv. I like my Key2. Was looking at the Fxtec Pro1, but my Priv died before I could get one, so Key2 it is. Would really love to get a Priv2, Electric Boogaloo if they ever manage to come out with one.
I wish they would stop adding stupid cameras (especially the selfie cam) to “professional devices” and instead lower the price.
> tamper-evident sticker over any of the screw heads, which frankly surprised me for a high security device
The security of a smart card is independent of the reader. PIN operations should be encrypted (e.g. using the public key corresponding to the private key on the card).
Maybe so that in really high security places they could open them up for inspection regularly to ensure no-one had hidden a camera inside?
Or the added cost of implementing tamper evident screws/methods weren’t necessary for a for card that was designed to not need to worry about the integrity of the reader as it was only ever a connection point. The card itself implements its own security, the reader is just the medium for communication and it isn’t generally considered a sensitive item in and of itself.
There are 4 pads near the connector to the smartcard holder. The outer two pads are connected to GND and what looks like a voltage regulator. The center two probably are either UART RX/TX or some kind of programming interface.
Those are the battery contacts.
If the CPU is anything like the AD6528, there is almost certainly unprotected JTAG available from some balls on the BGA. Given the blank nature of the rear of the PCB it would be quite easy to grind away the groundplane under the CPU, and then drill through to the corresponding balls, hoping that you don’t cut any vital tracks in the layers in between, but even if you do, probably not a big deal.
Once you get the JTAG connected, of course it’s all open to you to dump the code off the flash and disassemble. ARM7TDMI also allows live debug with two hardware breakpoints as I recall.
How about removing the chip, drilling through the spots, then reflowing the chip back onto the PCB?
When I made that device oh-so-many-years-ago, I never thought I’d see a tear down (it wasn’t a phone, so those who scoured the FCC site for certification pics didn’t care).
Creating a device for the US Military is tricky. They purchase 10 for evaluation. Then, years later, they either purchase 10,000,000 of the things or you never hear from them again. That’s why instead of a fully custom device, you’re looking at a BlackBerry phone but without the GSM RF hardware, screen, or keyboard. It’s running the same BlackBerry OS, Java VM, FIPS-certified crypto libraries, Bluetooth stack, etc. That processor was *very* expensive at the time (especially including GSM royalties) and should a large purchase have happened, a custom version would have been created. Re-use of hardware & software dramatically lowered the total project price at the time.
The USB port on the bottom will allow battery charging and the upload of any crypto-signed firmware. It might also work in a wired fashon with Windows, but I don’t remember.
Hacking that hardware is going to take more than getting to the JTAG ports. There are no exposed traces, obviously. The ASIC has a crypto extension that disables JTAG hardware when the crypto-locked OS is loaded. Re-using that hardware for anything else is going to be tricky.
I carry an Android now. It’s an amazing device in some ways. In others, it’s still 20 years behind what BlackBerry was.
Anyone have the software for these?
I have the Blackberry Smartcard Reader 2 but can’t find the software anywhere!!!