Art is a funny thing. Sometimes, it’s best done in a one-off fashion and sold for a hugely inflated price. Othertimes, it’s more accessible, and it becomes desirable to sell it in great quantity. [Wesley Treat] has been doing just that, and he’s shared some of his tricks of the trade on YouTube.
The video concerns some retro-futuristic raygun artwork panels that [Wesley] made in a recent video. The panels proved mighty popular, which meant he had a new problem to contend with: how to make them in quantity. His initial process largely involved making them in a one-off fashion, and that simply wouldn’t scale.
[Wesley] starts right at the beginning, demonstrating first how he produces stacks of blanks for his art panels. For production scale, he used pre-painted matte aluminium panels to speed the process. It’s followed by a sanding step, before the panels go into a laser etching jig to get imprinted with [Wesley’s] maker’s mark. Panels are then drilled via CNC, etched with their front artwork, and then fitted with a front acrylic panel, similarly cut out on the laser cutter. Then it’s just a matter of packing and shipping, a logistical hurdle that many small businesses have had to overcome.
[Wesley] does a great job of examining what it takes to scale from building one of something to many. It’s a topic we’ve looked at a few times in the past. Video after the break.
Continue reading “Tricks For Mass-Producing Laser-Etched Art”




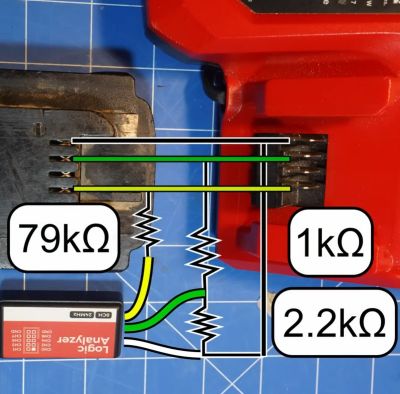
![One of the lists of commands and response messages obtained by [Tool Scientist] on YouTube.](https://hackaday.com/wp-content/uploads/2023/09/reverse_engineering_milwaukee_m18_redlink_protocol_startup_messages.jpg?w=400)









