 Press brakes are invaluable tools when working with sheet metal, but along with their almost infinite versatility comes a dizzying number of press brake types. After starting with an old-school, purely mechanical press brake, [Wes] of Watch Wes Work fame had been thinking of upgrading said press brake to a hydraulic configuration, but soured on this after facing all the disadvantages of the chosen approach. Thus, one does what any rational person does and purchases a used and very much untested 45-ton computer-controlled hydraulic press brake.
Press brakes are invaluable tools when working with sheet metal, but along with their almost infinite versatility comes a dizzying number of press brake types. After starting with an old-school, purely mechanical press brake, [Wes] of Watch Wes Work fame had been thinking of upgrading said press brake to a hydraulic configuration, but soured on this after facing all the disadvantages of the chosen approach. Thus, one does what any rational person does and purchases a used and very much untested 45-ton computer-controlled hydraulic press brake.
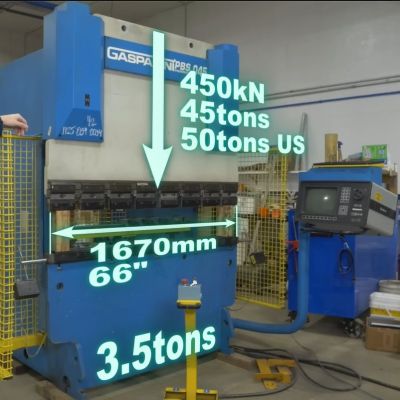
The video first explores the pros and cons of the various types of press brakes, with the issue of providing a balanced force across the entirety of the press brake’s dies being the largest problem. Although various mechanical and hydraulic solutions were attempted over the decades, a computer-controlled press brake like this Gasparini PBS 045 that [Wes] got is probably one of the more effective solutions, even if it provides the headache of more electrical and electronic things that can go wrong. The above screenshot of its basic workings should make that quite obvious, along with [Wes]’s detailed explanation.
As it turned out, this about 25-year-old Italian press brake wasn’t in such a terrible nick, but needed some badly needed TLC and obligatory breaker testing to bring it back to life. While it doesn’t like you not centering the part, this can be worked around by specifying that the part is actually larger than it is. Although [Wes] got it working well enough to do some work with it, it still has some gremlins left in it that will hopefully be hunted down over the coming time and video(s).
Continue reading “The Journey Of Finding The Right Press Brake”