
[Gio] sent in this slick Class A headphone amp. An old CD-ROM case was gutted to hold the goods. The design is fairly simple. Cost can be kept fairly low although the capacitors can add up if you’re a fanatic about quality. If you’ve ever lost any of your headphone gear to sticky fingers, you know that having it blending in to the background can be a great feature.
LED Serial Debugging For Cell Phone Hacking

[Barry] needed some way to get serial output to help debug his efforts to port Linux to the HTC TytnII (Windows mobile Pocket PC phone). He wrote some code to send serial output via one of the LEDs on the phone and rigged up an AVR to pic up the output and provide a USB interface to the computer. It runs at about 200bps – perfect for the quick debug session.
IPhone 2.0 Adds Secure Wipe
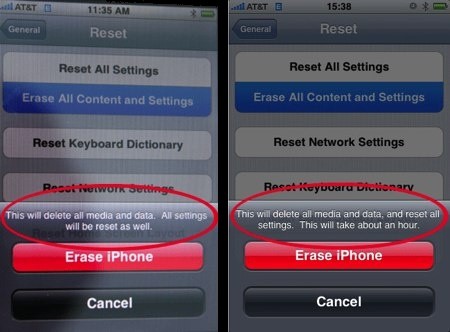
AppleInsider is reporting that iPhone Software v2.0 will add a secure wipe feature. The screenshot above shows the text “This will take about an hour.” added to the normal erase feature. This time is used to overwrite data to the disk multiple times. The need for secure phone erasure came to light after a researcher was able to recover personal information from a refurbished iPhone using forensic tools. Since then, a few people have published techniques for obliterating personal data using either the GUI or the more thorough command line method. Remote wipe has also been added to the new firmware in case the phone is stolen. We’re happy to see security being made easily accessible to nontechnical users and expect that remote wipe will become standard on laptops in the future.
IPhone Used To Control Squad Of UAVs
[youtube=http://www.youtube.com/watch?v=CRcld5aAN2E&hl=en]
Building UAVs is only half the work involved in making them fly; the other half is a control system. The Center for Collaborative Control of Unmanned Vehicles (C3UV) from the University of Califorina, Berkeley has devised a way to control a squad of RC airplanes with an iPhone. The system works by submitting commands and coordinates to a web site via the iPhone’s web browser. The site then sends the commands to the team of drones, which carry out the orders. The drones are outfitted with cameras and a tracking device, which allows them to be monitored on the ground using Google Maps.
The iPhone Terms of Service specifically prohibits it being used to drive remote vehicles, but that shouldn’t really pose a problem: since the orders are deployed via the iPhone’s web browser, they could technically be given by any web-enabled device. Before anyone cries foul, though, bear in mind that the idea is to issue orders from the field, and the iPhone is perhaps the most high-profile mobile web device on the market, which maximizes the project’s exposure. Still, we can’t help but think that they’d have gotten more media attention if they had used a hacked Kindle instead.
Covert IPhone Moleskine Case

Crafting isn’t really our thing, but just last week we were planning on doing this project. Thanks to the how-to singularity: the longer we wait, the more likely someone else will do our dirty work. The instructions are this:
- Cut a hole in a book.
- Stick your phone in that book.
- Let her open the book.
Wired’s write up has about 600 more words if you need clarification. The ebook on the screen is Cory Doctorow’s Little Brother, so expect to see this on BoingBoing… and again when it’s fan translated into Polish. [bre] made a similar hidden compartment book last Fall for Make’s PDFcast.
In all seriousness, we do enjoy the idea of carrying an innocuous little book around that could be doing some covert WiFi scanning, acting as a mobile accesspoint, or live streaming our location to friends. Unfortunately, since it’s an iPhone, most of this isn’t possible yet; you can’t even voice dial from your headset, while leaving the notebook in your pocket. This case also blurs what is considered rude. Most people would be annoyed if you started txting mid conversation, but people taking notes in Moleskines don’t get the same treatment.
Wiping An IPhone (more Thoroughly)

You may be hoping to subsidize the purchase of an iPhone 3G with the sale of your old one, but since you should wipe all your personal data from the old one first, we brought you [Rich Mogull]’s method for wiping all your private data off of an iPhone. The method, which involves overwriting your data with music, is slightly flawed, mainly because of live files that can’t be deleted while the phone’s OS is working and because the OS reserves a portion of the hard drive as unwritable space, which will make it impossible to completely fill it with music.
For those looking to annihilate every scrap of personal information, check out [Jonathan Zdziarski]’s method. It involves restoring the phone as a new phone, then jailbreaking it. Once the user has shell access, umount is used to force the two mount points into read-only mode. Now the partitions can be overwritten with /dev/zero, which should wipe them clean. The phone should then be forced into recovery mode to perform another full system restore, and the process is complete. As [Zdziarski] notes, several iterations of the process with /dev/random should prevent even NAND recovery, but there is an even better way of ensuring full data destruction: “simply take a sledgehammer to the device.” If you are unfamiliar with the command line though, chances are [Rich Mogull]’s method will be easier for you to handle, but don’t blame us if you sell your phone and the Feds get wise to the evidence you left on it.
[via Engadget]
New Vs. Old IPhone Apps

You’ve probably never heard of this obscure new device called the iPhone 3G from no-name manufacturer Apple, but we decided to give a rundown of some of its newest apps anyway. We’ll be comparing them to non-SDK third-party apps that only work on jailbroken iPhones.











