
We’re not surprised to see a car manufacturer using 3D-printing technology, but we think this may be the first time we’ve heard of 3D-prints going into production vehicles. You’ve likely heard of Christian von Koenigsegg’s cars if you’re a fan of BBC’s Top Gear, where the hypercar screams its way into the leading lap times.
Now it seems the Swedish car manufacturer has integrated 3D printing and scanning into the design process. Christian himself explains the benefits of both for iterative design: they roughed out a chair, adjusting it as they went until it was about the right shape and was comfortable. They then used a laser scanner to bring it into a CAD file, which significantly accelerated the production process. He’s also got some examples of brake pedals printed from ABS—they normally machine them out of aluminum—to test the fits and the feeling. They make adjustments as necessary to the prints, sometimes carving them up by hand, then break out the laser scanner again to capture any modifications, bring it back to CAD, and reprint the model.
Interestingly, they’ve been printing some bits and pieces for production cars out of ABS for a few years. Considering the low volume they are working with, it makes sense. Videos and more info after the jump.
Continue reading “Koenigsegg 3D-Printing For Production Vehicles”



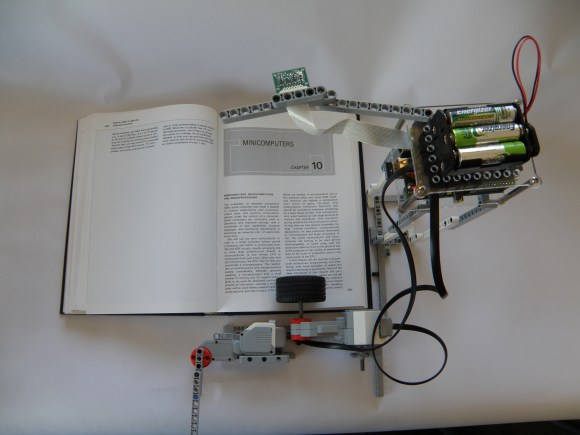
 This is not an application that runs on the tablet, it is a completely separate device that ‘reads’ the tablet screen. As you could guess from the BrickPi name, the brains behind the operation is a Raspberry Pi. A camera takes a photograph of the displayed text and the Raspberry Pi converts that image file to text using Optical Character Recognition. A Text-to-Speech engine then speaks the text in a robotic sounding voice. In order to change the page the Raspberry Pi controls a Lego Mindstorms arm that swipes across the tablet screen and the entire process is repeated.
This is not an application that runs on the tablet, it is a completely separate device that ‘reads’ the tablet screen. As you could guess from the BrickPi name, the brains behind the operation is a Raspberry Pi. A camera takes a photograph of the displayed text and the Raspberry Pi converts that image file to text using Optical Character Recognition. A Text-to-Speech engine then speaks the text in a robotic sounding voice. In order to change the page the Raspberry Pi controls a Lego Mindstorms arm that swipes across the tablet screen and the entire process is repeated.

 Clean PCBs in hand, [Eric] headed to his local TechShop. He drew his dead cat style frame in SolidWorks and cut it out on a ShopBot. While a high-end CNC cutter is nice, it’s not absolutely necessary. The fiberglass sheets could be cut with a rotary tool or a jigsaw. No matter how you cut it, be sure to wear a mask rated for fiberglass resins and some protective clothing. Fiberglass plate is nasty stuff to cut.
Clean PCBs in hand, [Eric] headed to his local TechShop. He drew his dead cat style frame in SolidWorks and cut it out on a ShopBot. While a high-end CNC cutter is nice, it’s not absolutely necessary. The fiberglass sheets could be cut with a rotary tool or a jigsaw. No matter how you cut it, be sure to wear a mask rated for fiberglass resins and some protective clothing. Fiberglass plate is nasty stuff to cut.







